mirror of
https://github.com/openappsec/openappsec.git
synced 2025-11-15 17:02:15 +03:00
Compare commits
56 Commits
support-ad
...
Nov_12_202
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
3061342b45 | ||
|
|
0869b8f24d | ||
|
|
1a4ab5f0d7 | ||
|
|
4a2d25ab65 | ||
|
|
f2ca7301b9 | ||
|
|
3d11ead170 | ||
|
|
39b8c5a5ff | ||
|
|
de6f1033bd | ||
|
|
58958b2436 | ||
|
|
59e7f00b3e | ||
|
|
e102b25b7d | ||
|
|
0386431eee | ||
|
|
fd1a77628e | ||
|
|
da911582a5 | ||
|
|
798dd2a7d1 | ||
|
|
6bda60ae84 | ||
|
|
5b9769e94e | ||
|
|
6693176131 | ||
|
|
c2ced075eb | ||
|
|
0b4bdd3677 | ||
|
|
d6599cc7bc | ||
|
|
4db7a54c27 | ||
|
|
f3ede0c60e | ||
|
|
79bac9f501 | ||
|
|
89263f6f34 | ||
|
|
5feb12f7e4 | ||
|
|
a2ee6ca839 | ||
|
|
1c10a12f6f | ||
|
|
e9f6ebd02b | ||
|
|
433c7c2d91 | ||
|
|
582791e37a | ||
|
|
a4d1fb6f7f | ||
|
|
dfbfdca1a9 | ||
|
|
36f511f449 | ||
|
|
f91f283b77 | ||
|
|
7c762e97a3 | ||
|
|
aaa1fbe8ed | ||
|
|
67e68c84c3 | ||
|
|
149a7305b7 | ||
|
|
ea20a51689 | ||
|
|
19f2383ae2 | ||
|
|
4038c18bda | ||
|
|
a9b6d2e715 | ||
|
|
81c75495cc | ||
|
|
5505022f47 | ||
|
|
b25fd8def5 | ||
|
|
702c1184ea | ||
|
|
b3cfd7e9d8 | ||
|
|
e36b990161 | ||
|
|
09868e6d7c | ||
|
|
e25f517c19 | ||
|
|
42a31e37b1 | ||
|
|
abe275c828 | ||
|
|
71d198f41a | ||
|
|
3ed569fe35 | ||
|
|
edd357f297 |
@@ -3,6 +3,11 @@ project (ngen)
|
||||
|
||||
set(CMAKE_CXX_FLAGS "${CMAKE_CXX_FLAGS} -fPIC -Wall -Wno-terminate -Dalpine")
|
||||
|
||||
execute_process(COMMAND grep -c "Alpine Linux" /etc/os-release OUTPUT_VARIABLE IS_ALPINE)
|
||||
if(IS_ALPINE EQUAL "1")
|
||||
set(CMAKE_CXX_FLAGS "${CMAKE_CXX_FLAGS} -Dalpine")
|
||||
endif()
|
||||
|
||||
find_package(Boost REQUIRED)
|
||||
find_package(ZLIB REQUIRED)
|
||||
find_package(GTest REQUIRED)
|
||||
|
||||
38
README.md
38
README.md
@@ -18,27 +18,41 @@ Every request to the application goes through two phases:
|
||||
|
||||
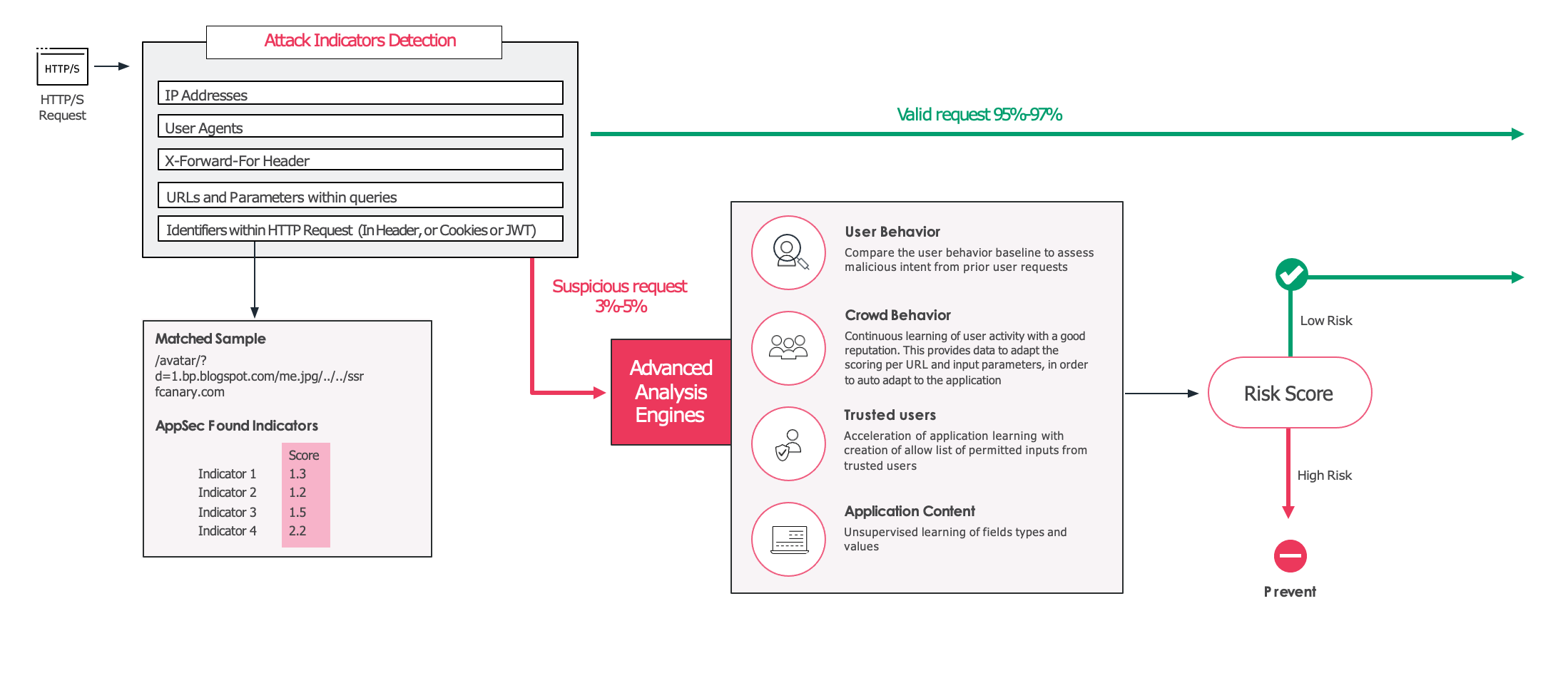
2. If the request is identified as a valid and legitimate request the request is allowed, and forwarded to your application. If, however, the request is considered suspicious or high risk, it then gets evaluated by the unsupervised model, which was trained in your specific environment. This model uses information such as the URL and the users involved to create a final confidence score that determines whether the request should be allowed or blocked.
|
||||
|
||||
The project is currently in Beta and feedback is most welcomed!
|
||||
|
||||
|
||||
## Machine Learning models
|
||||
|
||||
open-appsec uses two models:
|
||||
open-appsec uses two machine learning models:
|
||||
|
||||
1. A supervised model that was trained offline based on millions of requests, both malicious and benign.
|
||||
|
||||
* A basic model is provided as part of this repository. It is recommended for use in Monitor-Only and Test environments.
|
||||
* An advanced model which is more accurate and recommended for Production use can be downloaded from the [open-appsec portal](https://my.openappsec.io)->User Menu->Download advanced ML model. This model updates from time to time and you will get an email when these updates happen.
|
||||
* A **basic model** is provided as part of this repository. It is recommended for use in Monitor-Only and Test environments.
|
||||
* An **advanced model** which is more accurate and **recommended for Production** use can be downloaded from the [open-appsec portal](https://my.openappsec.io)->User Menu->Download advanced ML model. This model updates from time to time and you will get an email when these updates happen.
|
||||
|
||||
2. An unsupervised model that is being built in real time in the protected environment. This model uses traffic patterns specific to the environment.
|
||||
|
||||
|
||||
# Management
|
||||
|
||||
open-appsec can be managed using multiple methods:
|
||||
* [Declarative configuration files](https://docs.openappsec.io/getting-started/getting-started)
|
||||
* [Kubernetes Helm Charts and annotations](https://docs.openappsec.io/getting-started/getting-started)
|
||||
* [Using SaaS Web Management](https://docs.openappsec.io/getting-started/using-the-web-ui-saas)
|
||||
|
||||
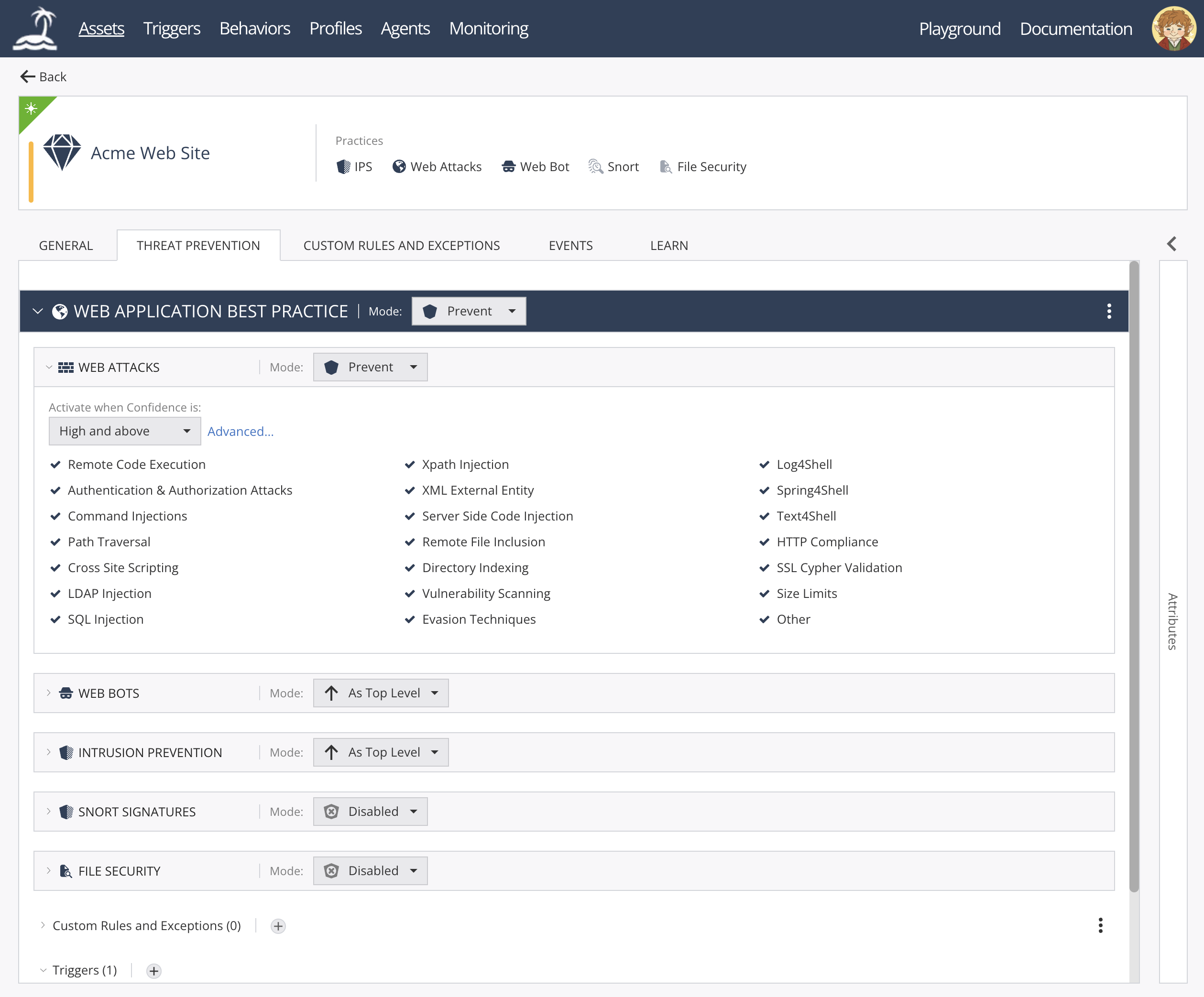
open-appsec Web UI:
|
||||
|
||||
|
||||
|
||||
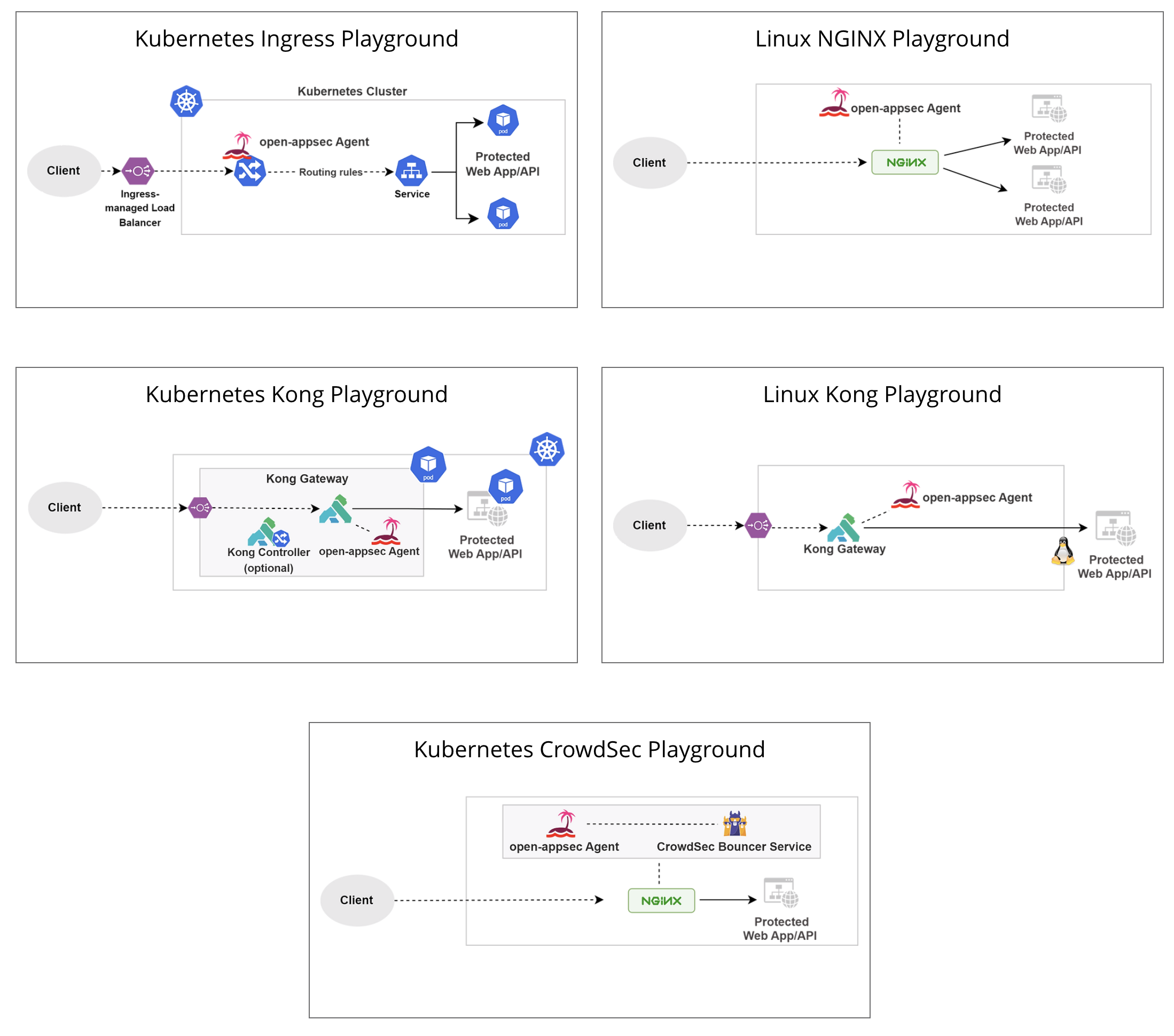
## Deployment Playgrounds (Virtual labs)
|
||||
You can experiment with open-appsec using [Playgrounds](https://www.openappsec.io/playground)
|
||||
|
||||
|
||||
|
||||
# Resources
|
||||
* [Project Website](https://openappsec.io)
|
||||
* [Offical Documentation](https://docs.openappsec.io/)
|
||||
* [Video Tutorials](https://www.openappsec.io/tutorials)
|
||||
* [Live Playgrounds](https://www.openappsec.io/playground)
|
||||
|
||||
|
||||
# open-appsec Installation
|
||||
# Installation
|
||||
|
||||
For Kubernetes (NGINX Ingress) using the installer:
|
||||
|
||||
@@ -49,11 +63,11 @@ $ ./open-appsec-k8s-install
|
||||
|
||||
For Kubernetes (NGINX or Kong) using Helm: follow [documentation](https://docs.openappsec.io/getting-started/start-with-kubernetes/install-using-helm-ingress-nginx-and-kong) – use this method if you’ve built your own containers.
|
||||
|
||||
For Linux (NGINX or Kong) using the installer (list of supported/pre-compiled NGINX attachments is available [here](https://downloads.openappsec.io/supported-nginx.txt)):
|
||||
For Linux (NGINX or Kong) using the installer (list of supported/pre-compiled NGINX attachments is available [here](https://downloads.openappsec.io/packages/supported-nginx.txt)):
|
||||
|
||||
```bash
|
||||
$ wget https://downloads.openappsec.io/open-appsec-install && chmod +x open-appsec-install
|
||||
$ ./open-appsec-install –auto
|
||||
$ ./open-appsec-install --auto
|
||||
```
|
||||
|
||||
For Linux, if you’ve built your own package use the following commands:
|
||||
@@ -90,12 +104,14 @@ Before compiling the services, you'll need to ensure the latest development vers
|
||||
* GTest
|
||||
* GMock
|
||||
* cURL
|
||||
* Redis
|
||||
* Hiredis
|
||||
|
||||
An example of installing the packages on Alpine:
|
||||
|
||||
```bash
|
||||
$ apk update
|
||||
$ apk add boost-dev openssl-dev pcre2-dev libxml2-dev gtest-dev curl-dev
|
||||
$ apk add boost-dev openssl-dev pcre2-dev libxml2-dev gtest-dev curl-dev hiredis-dev redis
|
||||
```
|
||||
|
||||
## Compiling and packaging the agent code
|
||||
|
||||
@@ -32,5 +32,6 @@ DEFINE_KDEBUG_FLAG(statelessValidation)
|
||||
DEFINE_KDEBUG_FLAG(kernelMetric)
|
||||
DEFINE_KDEBUG_FLAG(tproxy)
|
||||
DEFINE_KDEBUG_FLAG(tenantStats)
|
||||
DEFINE_KDEBUG_FLAG(uuidTranslation)
|
||||
|
||||
#endif // DEFINE_KDEBUG_FLAG
|
||||
|
||||
@@ -1,11 +1,9 @@
|
||||
annotations:
|
||||
artifacthub.io/changes: |
|
||||
- "[helm] Support custom port configuration for internal service (#9846)"
|
||||
- "Adding resource type to default HPA configuration to resolve issues with Terraform helm chart usage (#9803)"
|
||||
- "Update Ingress-Nginx version controller-v1.7.1"
|
||||
- "Update Ingress-Nginx version controller-v1.9.1"
|
||||
artifacthub.io/prerelease: "false"
|
||||
apiVersion: v2
|
||||
appVersion: 1.7.1
|
||||
appVersion: latest
|
||||
keywords:
|
||||
- ingress
|
||||
- nginx
|
||||
@@ -13,4 +11,4 @@ kubeVersion: '>=1.20.0-0'
|
||||
name: open-appsec-k8s-nginx-ingress
|
||||
sources:
|
||||
- https://github.com/kubernetes/ingress-nginx
|
||||
version: 4.6.1
|
||||
version: 4.8.1
|
||||
|
||||
@@ -2,7 +2,7 @@
|
||||
|
||||
[ingress-nginx](https://github.com/kubernetes/ingress-nginx) Ingress controller for Kubernetes using NGINX as a reverse proxy and load balancer
|
||||
|
||||
 
|
||||
 
|
||||
|
||||
To use, add `ingressClassName: nginx` spec field or the `kubernetes.io/ingress.class: nginx` annotation to your Ingress resources.
|
||||
|
||||
@@ -79,14 +79,14 @@ else it would make it impossible to evacuate a node. See [gh issue #7127](https:
|
||||
|
||||
### Prometheus Metrics
|
||||
|
||||
The Nginx ingress controller can export Prometheus metrics, by setting `controller.metrics.enabled` to `true`.
|
||||
The Ingress-Nginx Controller can export Prometheus metrics, by setting `controller.metrics.enabled` to `true`.
|
||||
|
||||
You can add Prometheus annotations to the metrics service using `controller.metrics.service.annotations`.
|
||||
Alternatively, if you use the Prometheus Operator, you can enable ServiceMonitor creation using `controller.metrics.serviceMonitor.enabled`. And set `controller.metrics.serviceMonitor.additionalLabels.release="prometheus"`. "release=prometheus" should match the label configured in the prometheus servicemonitor ( see `kubectl get servicemonitor prometheus-kube-prom-prometheus -oyaml -n prometheus`)
|
||||
|
||||
### ingress-nginx nginx\_status page/stats server
|
||||
|
||||
Previous versions of this chart had a `controller.stats.*` configuration block, which is now obsolete due to the following changes in nginx ingress controller:
|
||||
Previous versions of this chart had a `controller.stats.*` configuration block, which is now obsolete due to the following changes in Ingress-Nginx Controller:
|
||||
|
||||
- In [0.16.1](https://github.com/kubernetes/ingress-nginx/blob/main/Changelog.md#0161), the vts (virtual host traffic status) dashboard was removed
|
||||
- In [0.23.0](https://github.com/kubernetes/ingress-nginx/blob/main/Changelog.md#0230), the status page at port 18080 is now a unix socket webserver only available at localhost.
|
||||
@@ -143,8 +143,10 @@ controller:
|
||||
internal:
|
||||
enabled: true
|
||||
annotations:
|
||||
# Create internal ELB
|
||||
service.beta.kubernetes.io/aws-load-balancer-internal: "true"
|
||||
# Create internal NLB
|
||||
service.beta.kubernetes.io/aws-load-balancer-scheme: "internal"
|
||||
# Create internal ELB(Deprecated)
|
||||
# service.beta.kubernetes.io/aws-load-balancer-internal: "true"
|
||||
# Any other annotation can be declared here.
|
||||
```
|
||||
|
||||
@@ -187,13 +189,15 @@ controller:
|
||||
# Any other annotation can be declared here.
|
||||
```
|
||||
|
||||
The load balancer annotations of more cloud service providers can be found: [Internal load balancer](https://kubernetes.io/docs/concepts/services-networking/service/#internal-load-balancer).
|
||||
|
||||
An use case for this scenario is having a split-view DNS setup where the public zone CNAME records point to the external balancer URL while the private zone CNAME records point to the internal balancer URL. This way, you only need one ingress kubernetes object.
|
||||
|
||||
Optionally you can set `controller.service.loadBalancerIP` if you need a static IP for the resulting `LoadBalancer`.
|
||||
|
||||
### Ingress Admission Webhooks
|
||||
|
||||
With nginx-ingress-controller version 0.25+, the nginx ingress controller pod exposes an endpoint that will integrate with the `validatingwebhookconfiguration` Kubernetes feature to prevent bad ingress from being added to the cluster.
|
||||
With nginx-ingress-controller version 0.25+, the Ingress-Nginx Controller pod exposes an endpoint that will integrate with the `validatingwebhookconfiguration` Kubernetes feature to prevent bad ingress from being added to the cluster.
|
||||
**This feature is enabled by default since 0.31.0.**
|
||||
|
||||
With nginx-ingress-controller in 0.25.* work only with kubernetes 1.14+, 0.26 fix [this issue](https://github.com/kubernetes/ingress-nginx/pull/4521)
|
||||
@@ -202,7 +206,7 @@ With nginx-ingress-controller in 0.25.* work only with kubernetes 1.14+, 0.26 fi
|
||||
A validating and configuration requires the endpoint to which the request is sent to use TLS. It is possible to set up custom certificates to do this, but in most cases, a self-signed certificate is enough. The setup of this component requires some more complex orchestration when using helm. The steps are created to be idempotent and to allow turning the feature on and off without running into helm quirks.
|
||||
|
||||
1. A pre-install hook provisions a certificate into the same namespace using a format compatible with provisioning using end user certificates. If the certificate already exists, the hook exits.
|
||||
2. The ingress nginx controller pod is configured to use a TLS proxy container, which will load that certificate.
|
||||
2. The Ingress-Nginx Controller pod is configured to use a TLS proxy container, which will load that certificate.
|
||||
3. Validating and Mutating webhook configurations are created in the cluster.
|
||||
4. A post-install hook reads the CA from the secret created by step 1 and patches the Validating and Mutating webhook configurations. This process will allow a custom CA provisioned by some other process to also be patched into the webhook configurations. The chosen failure policy is also patched into the webhook configurations
|
||||
|
||||
@@ -245,14 +249,13 @@ As of version `1.26.0` of this chart, by simply not providing any clusterIP valu
|
||||
| controller.admissionWebhooks.key | string | `"/usr/local/certificates/key"` | |
|
||||
| controller.admissionWebhooks.labels | object | `{}` | Labels to be added to admission webhooks |
|
||||
| controller.admissionWebhooks.namespaceSelector | object | `{}` | |
|
||||
| controller.admissionWebhooks.networkPolicyEnabled | bool | `false` | |
|
||||
| controller.admissionWebhooks.objectSelector | object | `{}` | |
|
||||
| controller.admissionWebhooks.patch.enabled | bool | `true` | |
|
||||
| controller.admissionWebhooks.patch.image.digest | string | `"sha256:01d181618f270f2a96c04006f33b2699ad3ccb02da48d0f89b22abce084b292f"` | |
|
||||
| controller.admissionWebhooks.patch.image.digest | string | `"sha256:543c40fd093964bc9ab509d3e791f9989963021f1e9e4c9c7b6700b02bfb227b"` | |
|
||||
| controller.admissionWebhooks.patch.image.image | string | `"ingress-nginx/kube-webhook-certgen"` | |
|
||||
| controller.admissionWebhooks.patch.image.pullPolicy | string | `"IfNotPresent"` | |
|
||||
| controller.admissionWebhooks.patch.image.registry | string | `"registry.k8s.io"` | |
|
||||
| controller.admissionWebhooks.patch.image.tag | string | `"v20230312-helm-chart-4.5.2-28-g66a760794"` | |
|
||||
| controller.admissionWebhooks.patch.image.tag | string | `"v20230407"` | |
|
||||
| controller.admissionWebhooks.patch.labels | object | `{}` | Labels to be added to patch job resources |
|
||||
| controller.admissionWebhooks.patch.nodeSelector."kubernetes.io/os" | string | `"linux"` | |
|
||||
| controller.admissionWebhooks.patch.podAnnotations | object | `{}` | |
|
||||
@@ -270,10 +273,9 @@ As of version `1.26.0` of this chart, by simply not providing any clusterIP valu
|
||||
| controller.admissionWebhooks.service.servicePort | int | `443` | |
|
||||
| controller.admissionWebhooks.service.type | string | `"ClusterIP"` | |
|
||||
| controller.affinity | object | `{}` | Affinity and anti-affinity rules for server scheduling to nodes # Ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/#affinity-and-anti-affinity # |
|
||||
| controller.allowSnippetAnnotations | bool | `true` | This configuration defines if Ingress Controller should allow users to set their own *-snippet annotations, otherwise this is forbidden / dropped when users add those annotations. Global snippets in ConfigMap are still respected |
|
||||
| controller.allowSnippetAnnotations | bool | `false` | This configuration defines if Ingress Controller should allow users to set their own *-snippet annotations, otherwise this is forbidden / dropped when users add those annotations. Global snippets in ConfigMap are still respected |
|
||||
| controller.annotations | object | `{}` | Annotations to be added to the controller Deployment or DaemonSet # |
|
||||
| controller.autoscaling.annotations | object | `{}` | |
|
||||
| controller.autoscaling.apiVersion | string | `"autoscaling/v2"` | |
|
||||
| controller.autoscaling.behavior | object | `{}` | |
|
||||
| controller.autoscaling.enabled | bool | `false` | |
|
||||
| controller.autoscaling.maxReplicas | int | `11` | |
|
||||
@@ -291,18 +293,20 @@ As of version `1.26.0` of this chart, by simply not providing any clusterIP valu
|
||||
| controller.dnsConfig | object | `{}` | Optionally customize the pod dnsConfig. |
|
||||
| controller.dnsPolicy | string | `"ClusterFirst"` | Optionally change this to ClusterFirstWithHostNet in case you have 'hostNetwork: true'. By default, while using host network, name resolution uses the host's DNS. If you wish nginx-controller to keep resolving names inside the k8s network, use ClusterFirstWithHostNet. |
|
||||
| controller.electionID | string | `""` | Election ID to use for status update, by default it uses the controller name combined with a suffix of 'leader' |
|
||||
| controller.enableAnnotationValidations | bool | `false` | |
|
||||
| controller.enableMimalloc | bool | `true` | Enable mimalloc as a drop-in replacement for malloc. # ref: https://github.com/microsoft/mimalloc # |
|
||||
| controller.enableTopologyAwareRouting | bool | `false` | This configuration enables Topology Aware Routing feature, used together with service annotation service.kubernetes.io/topology-aware-hints="auto" Defaults to false |
|
||||
| controller.enableTopologyAwareRouting | bool | `false` | This configuration enables Topology Aware Routing feature, used together with service annotation service.kubernetes.io/topology-mode="auto" Defaults to false |
|
||||
| controller.existingPsp | string | `""` | Use an existing PSP instead of creating one |
|
||||
| controller.extraArgs | object | `{}` | Additional command line arguments to pass to nginx-ingress-controller E.g. to specify the default SSL certificate you can use |
|
||||
| controller.extraArgs | object | `{}` | Additional command line arguments to pass to Ingress-Nginx Controller E.g. to specify the default SSL certificate you can use |
|
||||
| controller.extraContainers | list | `[]` | Additional containers to be added to the controller pod. See https://github.com/lemonldap-ng-controller/lemonldap-ng-controller as example. |
|
||||
| controller.extraEnvs | list | `[]` | Additional environment variables to set |
|
||||
| controller.extraInitContainers | list | `[]` | Containers, which are run before the app containers are started. |
|
||||
| controller.extraModules | list | `[]` | Modules, which are mounted into the core nginx image. See values.yaml for a sample to add opentelemetry module |
|
||||
| controller.extraVolumeMounts | list | `[]` | Additional volumeMounts to the controller main container. |
|
||||
| controller.extraVolumes | list | `[]` | Additional volumes to the controller pod. |
|
||||
| controller.healthCheckHost | string | `""` | Address to bind the health check endpoint. It is better to set this option to the internal node address if the ingress nginx controller is running in the `hostNetwork: true` mode. |
|
||||
| controller.healthCheckHost | string | `""` | Address to bind the health check endpoint. It is better to set this option to the internal node address if the Ingress-Nginx Controller is running in the `hostNetwork: true` mode. |
|
||||
| controller.healthCheckPath | string | `"/healthz"` | Path of the health check endpoint. All requests received on the port defined by the healthz-port parameter are forwarded internally to this path. |
|
||||
| controller.hostAliases | list | `[]` | Optionally customize the pod hostAliases. |
|
||||
| controller.hostNetwork | bool | `false` | Required for use with CNI based kubernetes installations (such as ones set up by kubeadm), since CNI and hostport don't mix yet. Can be deprecated once https://github.com/kubernetes/kubernetes/issues/23920 is merged |
|
||||
| controller.hostPort.enabled | bool | `false` | Enable 'hostPort' or not |
|
||||
| controller.hostPort.ports.http | int | `80` | 'hostPort' http port |
|
||||
@@ -310,13 +314,13 @@ As of version `1.26.0` of this chart, by simply not providing any clusterIP valu
|
||||
| controller.hostname | object | `{}` | Optionally customize the pod hostname. |
|
||||
| controller.image.allowPrivilegeEscalation | bool | `true` | |
|
||||
| controller.image.chroot | bool | `false` | |
|
||||
| controller.image.digest | string | `"sha256:7244b95ea47bddcb8267c1e625fb163fc183ef55448855e3ac52a7b260a60407"` | |
|
||||
| controller.image.digestChroot | string | `"sha256:e35d5ab487861b9d419c570e3530589229224a0762c7b4d2e2222434abb8d988"` | |
|
||||
| controller.image.digest | string | `"sha256:605a737877de78969493a4b1213b21de4ee425d2926906857b98050f57a95b25"` | |
|
||||
| controller.image.digestChroot | string | `"sha256:2ac744ef08850ee86ad7162451a6879f47c1a41c6a757f6b6f913c52103b8836"` | |
|
||||
| controller.image.image | string | `"ingress-nginx/controller"` | |
|
||||
| controller.image.pullPolicy | string | `"IfNotPresent"` | |
|
||||
| controller.image.registry | string | `"registry.k8s.io"` | |
|
||||
| controller.image.runAsUser | int | `101` | |
|
||||
| controller.image.tag | string | `"v1.7.1"` | |
|
||||
| controller.image.tag | string | `"v1.9.1"` | |
|
||||
| controller.ingressClass | string | `"nginx"` | For backwards compatibility with ingress.class annotation, use ingressClass. Algorithm is as follows, first ingressClassName is considered, if not present, controller looks for ingress.class annotation |
|
||||
| controller.ingressClassByName | bool | `false` | Process IngressClass per name (additionally as per spec.controller). |
|
||||
| controller.ingressClassResource.controllerValue | string | `"k8s.io/ingress-nginx"` | Controller-value of the controller that is processing this ingressClass |
|
||||
@@ -353,7 +357,7 @@ As of version `1.26.0` of this chart, by simply not providing any clusterIP valu
|
||||
| controller.metrics.prometheusRule.enabled | bool | `false` | |
|
||||
| controller.metrics.prometheusRule.rules | list | `[]` | |
|
||||
| controller.metrics.service.annotations | object | `{}` | |
|
||||
| controller.metrics.service.externalIPs | list | `[]` | List of IP addresses at which the stats-exporter service is available # Ref: https://kubernetes.io/docs/user-guide/services/#external-ips # |
|
||||
| controller.metrics.service.externalIPs | list | `[]` | List of IP addresses at which the stats-exporter service is available # Ref: https://kubernetes.io/docs/concepts/services-networking/service/#external-ips # |
|
||||
| controller.metrics.service.labels | object | `{}` | Labels to be added to the metrics service resource |
|
||||
| controller.metrics.service.loadBalancerSourceRanges | list | `[]` | |
|
||||
| controller.metrics.service.servicePort | int | `10254` | |
|
||||
@@ -366,13 +370,15 @@ As of version `1.26.0` of this chart, by simply not providing any clusterIP valu
|
||||
| controller.metrics.serviceMonitor.relabelings | list | `[]` | |
|
||||
| controller.metrics.serviceMonitor.scrapeInterval | string | `"30s"` | |
|
||||
| controller.metrics.serviceMonitor.targetLabels | list | `[]` | |
|
||||
| controller.minAvailable | int | `1` | Define either 'minAvailable' or 'maxUnavailable', never both. |
|
||||
| controller.minAvailable | int | `1` | Minimum available pods set in PodDisruptionBudget. Define either 'minAvailable' or 'maxUnavailable', never both. |
|
||||
| controller.minReadySeconds | int | `0` | `minReadySeconds` to avoid killing pods before we are ready # |
|
||||
| controller.name | string | `"controller"` | |
|
||||
| controller.nodeSelector | object | `{"kubernetes.io/os":"linux"}` | Node labels for controller pod assignment # Ref: https://kubernetes.io/docs/user-guide/node-selection/ # |
|
||||
| controller.networkPolicy.enabled | bool | `false` | Enable 'networkPolicy' or not |
|
||||
| controller.nodeSelector | object | `{"kubernetes.io/os":"linux"}` | Node labels for controller pod assignment # Ref: https://kubernetes.io/docs/concepts/scheduling-eviction/assign-pod-node/ # |
|
||||
| controller.opentelemetry.containerSecurityContext.allowPrivilegeEscalation | bool | `false` | |
|
||||
| controller.opentelemetry.enabled | bool | `false` | |
|
||||
| controller.opentelemetry.image | string | `"registry.k8s.io/ingress-nginx/opentelemetry:v20230312-helm-chart-4.5.2-28-g66a760794@sha256:40f766ac4a9832f36f217bb0e98d44c8d38faeccbfe861fbc1a76af7e9ab257f"` | |
|
||||
| controller.opentelemetry.image | string | `"registry.k8s.io/ingress-nginx/opentelemetry:v20230721-3e2062ee5@sha256:13bee3f5223883d3ca62fee7309ad02d22ec00ff0d7033e3e9aca7a9f60fd472"` | |
|
||||
| controller.opentelemetry.resources | object | `{}` | |
|
||||
| controller.podAnnotations | object | `{}` | Annotations to be added to controller pods # |
|
||||
| controller.podLabels | object | `{}` | Labels to add to the pod container metadata |
|
||||
| controller.podSecurityContext | object | `{}` | Security Context policies for controller pods |
|
||||
@@ -390,27 +396,29 @@ As of version `1.26.0` of this chart, by simply not providing any clusterIP valu
|
||||
| controller.readinessProbe.successThreshold | int | `1` | |
|
||||
| controller.readinessProbe.timeoutSeconds | int | `1` | |
|
||||
| controller.replicaCount | int | `1` | |
|
||||
| controller.reportNodeInternalIp | bool | `false` | Bare-metal considerations via the host network https://kubernetes.github.io/ingress-nginx/deploy/baremetal/#via-the-host-network Ingress status was blank because there is no Service exposing the NGINX Ingress controller in a configuration using the host network, the default --publish-service flag used in standard cloud setups does not apply |
|
||||
| controller.reportNodeInternalIp | bool | `false` | Bare-metal considerations via the host network https://kubernetes.github.io/ingress-nginx/deploy/baremetal/#via-the-host-network Ingress status was blank because there is no Service exposing the Ingress-Nginx Controller in a configuration using the host network, the default --publish-service flag used in standard cloud setups does not apply |
|
||||
| controller.resources.requests.cpu | string | `"100m"` | |
|
||||
| controller.resources.requests.memory | string | `"90Mi"` | |
|
||||
| controller.scope.enabled | bool | `false` | Enable 'scope' or not |
|
||||
| controller.scope.namespace | string | `""` | Namespace to limit the controller to; defaults to $(POD_NAMESPACE) |
|
||||
| controller.scope.namespaceSelector | string | `""` | When scope.enabled == false, instead of watching all namespaces, we watching namespaces whose labels only match with namespaceSelector. Format like foo=bar. Defaults to empty, means watching all namespaces. |
|
||||
| controller.service.annotations | object | `{}` | |
|
||||
| controller.service.annotations | object | `{}` | Annotations are mandatory for the load balancer to come up. Varies with the cloud service. Values passed through helm tpl engine. |
|
||||
| controller.service.appProtocol | bool | `true` | If enabled is adding an appProtocol option for Kubernetes service. An appProtocol field replacing annotations that were using for setting a backend protocol. Here is an example for AWS: service.beta.kubernetes.io/aws-load-balancer-backend-protocol: http It allows choosing the protocol for each backend specified in the Kubernetes service. See the following GitHub issue for more details about the purpose: https://github.com/kubernetes/kubernetes/issues/40244 Will be ignored for Kubernetes versions older than 1.20 # |
|
||||
| controller.service.enableHttp | bool | `true` | |
|
||||
| controller.service.enableHttps | bool | `true` | |
|
||||
| controller.service.enabled | bool | `true` | |
|
||||
| controller.service.external.enabled | bool | `true` | |
|
||||
| controller.service.externalIPs | list | `[]` | List of IP addresses at which the controller services are available # Ref: https://kubernetes.io/docs/user-guide/services/#external-ips # |
|
||||
| controller.service.internal.annotations | object | `{}` | Annotations are mandatory for the load balancer to come up. Varies with the cloud service. |
|
||||
| controller.service.externalIPs | list | `[]` | List of IP addresses at which the controller services are available # Ref: https://kubernetes.io/docs/concepts/services-networking/service/#external-ips # |
|
||||
| controller.service.internal.annotations | object | `{}` | Annotations are mandatory for the load balancer to come up. Varies with the cloud service. Values passed through helm tpl engine. |
|
||||
| controller.service.internal.enabled | bool | `false` | Enables an additional internal load balancer (besides the external one). |
|
||||
| controller.service.internal.loadBalancerIP | string | `""` | Used by cloud providers to connect the resulting internal LoadBalancer to a pre-existing static IP. Make sure to add to the service the needed annotation to specify the subnet which the static IP belongs to. For instance, `networking.gke.io/internal-load-balancer-subnet` for GCP and `service.beta.kubernetes.io/aws-load-balancer-subnets` for AWS. |
|
||||
| controller.service.internal.loadBalancerSourceRanges | list | `[]` | Restrict access For LoadBalancer service. Defaults to 0.0.0.0/0. |
|
||||
| controller.service.internal.ports | object | `{}` | Custom port mapping for internal service |
|
||||
| controller.service.internal.targetPorts | object | `{}` | Custom target port mapping for internal service |
|
||||
| controller.service.ipFamilies | list | `["IPv4"]` | List of IP families (e.g. IPv4, IPv6) assigned to the service. This field is usually assigned automatically based on cluster configuration and the ipFamilyPolicy field. # Ref: https://kubernetes.io/docs/concepts/services-networking/dual-stack/ |
|
||||
| controller.service.ipFamilyPolicy | string | `"SingleStack"` | Represents the dual-stack-ness requested or required by this Service. Possible values are SingleStack, PreferDualStack or RequireDualStack. The ipFamilies and clusterIPs fields depend on the value of this field. # Ref: https://kubernetes.io/docs/concepts/services-networking/dual-stack/ |
|
||||
| controller.service.labels | object | `{}` | |
|
||||
| controller.service.loadBalancerClass | string | `""` | Used by cloud providers to select a load balancer implementation other than the cloud provider default. https://kubernetes.io/docs/concepts/services-networking/service/#load-balancer-class |
|
||||
| controller.service.loadBalancerIP | string | `""` | Used by cloud providers to connect the resulting `LoadBalancer` to a pre-existing static IP according to https://kubernetes.io/docs/concepts/services-networking/service/#loadbalancer |
|
||||
| controller.service.loadBalancerSourceRanges | list | `[]` | |
|
||||
| controller.service.nodePorts.http | string | `""` | |
|
||||
@@ -435,7 +443,6 @@ As of version `1.26.0` of this chart, by simply not providing any clusterIP valu
|
||||
| controller.watchIngressWithoutClass | bool | `false` | Process Ingress objects without ingressClass annotation/ingressClassName field Overrides value for --watch-ingress-without-class flag of the controller binary Defaults to false |
|
||||
| defaultBackend.affinity | object | `{}` | |
|
||||
| defaultBackend.autoscaling.annotations | object | `{}` | |
|
||||
| defaultBackend.autoscaling.apiVersion | string | `"autoscaling/v2"` | |
|
||||
| defaultBackend.autoscaling.enabled | bool | `false` | |
|
||||
| defaultBackend.autoscaling.maxReplicas | int | `2` | |
|
||||
| defaultBackend.autoscaling.minReplicas | int | `1` | |
|
||||
@@ -465,7 +472,8 @@ As of version `1.26.0` of this chart, by simply not providing any clusterIP valu
|
||||
| defaultBackend.minAvailable | int | `1` | |
|
||||
| defaultBackend.minReadySeconds | int | `0` | `minReadySeconds` to avoid killing pods before we are ready # |
|
||||
| defaultBackend.name | string | `"defaultbackend"` | |
|
||||
| defaultBackend.nodeSelector | object | `{"kubernetes.io/os":"linux"}` | Node labels for default backend pod assignment # Ref: https://kubernetes.io/docs/user-guide/node-selection/ # |
|
||||
| defaultBackend.networkPolicy.enabled | bool | `false` | Enable 'networkPolicy' or not |
|
||||
| defaultBackend.nodeSelector | object | `{"kubernetes.io/os":"linux"}` | Node labels for default backend pod assignment # Ref: https://kubernetes.io/docs/concepts/scheduling-eviction/assign-pod-node/ # |
|
||||
| defaultBackend.podAnnotations | object | `{}` | Annotations to be added to default backend pods # |
|
||||
| defaultBackend.podLabels | object | `{}` | Labels to add to the pod container metadata |
|
||||
| defaultBackend.podSecurityContext | object | `{}` | Security Context policies for controller pods See https://kubernetes.io/docs/tasks/administer-cluster/sysctl-cluster/ for notes on enabling and using sysctls # |
|
||||
@@ -479,7 +487,7 @@ As of version `1.26.0` of this chart, by simply not providing any clusterIP valu
|
||||
| defaultBackend.replicaCount | int | `1` | |
|
||||
| defaultBackend.resources | object | `{}` | |
|
||||
| defaultBackend.service.annotations | object | `{}` | |
|
||||
| defaultBackend.service.externalIPs | list | `[]` | List of IP addresses at which the default backend service is available # Ref: https://kubernetes.io/docs/user-guide/services/#external-ips # |
|
||||
| defaultBackend.service.externalIPs | list | `[]` | List of IP addresses at which the default backend service is available # Ref: https://kubernetes.io/docs/concepts/services-networking/service/#external-ips # |
|
||||
| defaultBackend.service.loadBalancerSourceRanges | list | `[]` | |
|
||||
| defaultBackend.service.servicePort | int | `80` | |
|
||||
| defaultBackend.service.type | string | `"ClusterIP"` | |
|
||||
|
||||
@@ -76,14 +76,14 @@ else it would make it impossible to evacuate a node. See [gh issue #7127](https:
|
||||
|
||||
### Prometheus Metrics
|
||||
|
||||
The Nginx ingress controller can export Prometheus metrics, by setting `controller.metrics.enabled` to `true`.
|
||||
The Ingress-Nginx Controller can export Prometheus metrics, by setting `controller.metrics.enabled` to `true`.
|
||||
|
||||
You can add Prometheus annotations to the metrics service using `controller.metrics.service.annotations`.
|
||||
Alternatively, if you use the Prometheus Operator, you can enable ServiceMonitor creation using `controller.metrics.serviceMonitor.enabled`. And set `controller.metrics.serviceMonitor.additionalLabels.release="prometheus"`. "release=prometheus" should match the label configured in the prometheus servicemonitor ( see `kubectl get servicemonitor prometheus-kube-prom-prometheus -oyaml -n prometheus`)
|
||||
|
||||
### ingress-nginx nginx\_status page/stats server
|
||||
|
||||
Previous versions of this chart had a `controller.stats.*` configuration block, which is now obsolete due to the following changes in nginx ingress controller:
|
||||
Previous versions of this chart had a `controller.stats.*` configuration block, which is now obsolete due to the following changes in Ingress-Nginx Controller:
|
||||
|
||||
- In [0.16.1](https://github.com/kubernetes/ingress-nginx/blob/main/Changelog.md#0161), the vts (virtual host traffic status) dashboard was removed
|
||||
- In [0.23.0](https://github.com/kubernetes/ingress-nginx/blob/main/Changelog.md#0230), the status page at port 18080 is now a unix socket webserver only available at localhost.
|
||||
@@ -140,8 +140,10 @@ controller:
|
||||
internal:
|
||||
enabled: true
|
||||
annotations:
|
||||
# Create internal ELB
|
||||
service.beta.kubernetes.io/aws-load-balancer-internal: "true"
|
||||
# Create internal NLB
|
||||
service.beta.kubernetes.io/aws-load-balancer-scheme: "internal"
|
||||
# Create internal ELB(Deprecated)
|
||||
# service.beta.kubernetes.io/aws-load-balancer-internal: "true"
|
||||
# Any other annotation can be declared here.
|
||||
```
|
||||
|
||||
@@ -184,13 +186,15 @@ controller:
|
||||
# Any other annotation can be declared here.
|
||||
```
|
||||
|
||||
The load balancer annotations of more cloud service providers can be found: [Internal load balancer](https://kubernetes.io/docs/concepts/services-networking/service/#internal-load-balancer).
|
||||
|
||||
An use case for this scenario is having a split-view DNS setup where the public zone CNAME records point to the external balancer URL while the private zone CNAME records point to the internal balancer URL. This way, you only need one ingress kubernetes object.
|
||||
|
||||
Optionally you can set `controller.service.loadBalancerIP` if you need a static IP for the resulting `LoadBalancer`.
|
||||
|
||||
### Ingress Admission Webhooks
|
||||
|
||||
With nginx-ingress-controller version 0.25+, the nginx ingress controller pod exposes an endpoint that will integrate with the `validatingwebhookconfiguration` Kubernetes feature to prevent bad ingress from being added to the cluster.
|
||||
With nginx-ingress-controller version 0.25+, the Ingress-Nginx Controller pod exposes an endpoint that will integrate with the `validatingwebhookconfiguration` Kubernetes feature to prevent bad ingress from being added to the cluster.
|
||||
**This feature is enabled by default since 0.31.0.**
|
||||
|
||||
With nginx-ingress-controller in 0.25.* work only with kubernetes 1.14+, 0.26 fix [this issue](https://github.com/kubernetes/ingress-nginx/pull/4521)
|
||||
@@ -199,7 +203,7 @@ With nginx-ingress-controller in 0.25.* work only with kubernetes 1.14+, 0.26 fi
|
||||
A validating and configuration requires the endpoint to which the request is sent to use TLS. It is possible to set up custom certificates to do this, but in most cases, a self-signed certificate is enough. The setup of this component requires some more complex orchestration when using helm. The steps are created to be idempotent and to allow turning the feature on and off without running into helm quirks.
|
||||
|
||||
1. A pre-install hook provisions a certificate into the same namespace using a format compatible with provisioning using end user certificates. If the certificate already exists, the hook exits.
|
||||
2. The ingress nginx controller pod is configured to use a TLS proxy container, which will load that certificate.
|
||||
2. The Ingress-Nginx Controller pod is configured to use a TLS proxy container, which will load that certificate.
|
||||
3. Validating and Mutating webhook configurations are created in the cluster.
|
||||
4. A post-install hook reads the CA from the secret created by step 1 and patches the Validating and Mutating webhook configurations. This process will allow a custom CA provisioned by some other process to also be patched into the webhook configurations. The chosen failure policy is also patched into the webhook configurations
|
||||
|
||||
|
||||
@@ -0,0 +1,14 @@
|
||||
# Changelog
|
||||
|
||||
This file documents all notable changes to [ingress-nginx](https://github.com/kubernetes/ingress-nginx) Helm Chart. The release numbering uses [semantic versioning](http://semver.org).
|
||||
|
||||
### 4.7.0
|
||||
|
||||
* helm: Fix opentelemetry module installation for daemonset (#9792)
|
||||
* Update charts/* to keep project name display aligned (#9931)
|
||||
* HPA: Use capabilites & align manifests. (#9521)
|
||||
* PodDisruptionBudget spec logic update (#9904)
|
||||
* add option for annotations in PodDisruptionBudget (#9843)
|
||||
* Update Ingress-Nginx version controller-v1.8.0
|
||||
|
||||
**Full Changelog**: https://github.com/kubernetes/ingress-nginx/compare/helm-chart-4.6.1...helm-chart-4.7.0
|
||||
@@ -0,0 +1,12 @@
|
||||
# Changelog
|
||||
|
||||
This file documents all notable changes to [ingress-nginx](https://github.com/kubernetes/ingress-nginx) Helm Chart. The release numbering uses [semantic versioning](http://semver.org).
|
||||
|
||||
### 4.7.1
|
||||
|
||||
* Added a doc line to the missing helm value service.internal.loadBalancerIP (#9406)
|
||||
* feat(helm): Add loadBalancerClass (#9562)
|
||||
* added helmshowvalues example (#10019)
|
||||
* Update Ingress-Nginx version controller-v1.8.1
|
||||
|
||||
**Full Changelog**: https://github.com/kubernetes/ingress-nginx/compare/helm-chart-4.7.0...helm-chart-4.7.1
|
||||
@@ -0,0 +1,9 @@
|
||||
# Changelog
|
||||
|
||||
This file documents all notable changes to [ingress-nginx](https://github.com/kubernetes/ingress-nginx) Helm Chart. The release numbering uses [semantic versioning](http://semver.org).
|
||||
|
||||
### 4.7.2
|
||||
|
||||
* Update Ingress-Nginx version controller-v1.8.2
|
||||
|
||||
**Full Changelog**: https://github.com/kubernetes/ingress-nginx/compare/helm-chart-4.7.1...helm-chart-4.7.2
|
||||
@@ -0,0 +1,13 @@
|
||||
# Changelog
|
||||
|
||||
This file documents all notable changes to [ingress-nginx](https://github.com/kubernetes/ingress-nginx) Helm Chart. The release numbering uses [semantic versioning](http://semver.org).
|
||||
|
||||
### 4.8.0-beta.0
|
||||
|
||||
* ci(helm): fix Helm Chart release action 422 error (#10237)
|
||||
* helm: Use .Release.Namespace as default for ServiceMonitor namespace (#10249)
|
||||
* [helm] configure allow to configure hostAliases (#10180)
|
||||
* [helm] pass service annotations through helm tpl engine (#10084)
|
||||
* Update Ingress-Nginx version controller-v1.9.0-beta.0
|
||||
|
||||
**Full Changelog**: https://github.com/kubernetes/ingress-nginx/compare/helm-chart-4.7.2...helm-chart-4.8.0-beta.0
|
||||
@@ -0,0 +1,13 @@
|
||||
# Changelog
|
||||
|
||||
This file documents all notable changes to [ingress-nginx](https://github.com/kubernetes/ingress-nginx) Helm Chart. The release numbering uses [semantic versioning](http://semver.org).
|
||||
|
||||
### 4.8.0
|
||||
|
||||
* ci(helm): fix Helm Chart release action 422 error (#10237)
|
||||
* helm: Use .Release.Namespace as default for ServiceMonitor namespace (#10249)
|
||||
* [helm] configure allow to configure hostAliases (#10180)
|
||||
* [helm] pass service annotations through helm tpl engine (#10084)
|
||||
* Update Ingress-Nginx version controller-v1.9.0
|
||||
|
||||
**Full Changelog**: https://github.com/kubernetes/ingress-nginx/compare/helm-chart-4.7.2...helm-chart-4.8.0
|
||||
@@ -0,0 +1,9 @@
|
||||
# Changelog
|
||||
|
||||
This file documents all notable changes to [ingress-nginx](https://github.com/kubernetes/ingress-nginx) Helm Chart. The release numbering uses [semantic versioning](http://semver.org).
|
||||
|
||||
### 4.8.1
|
||||
|
||||
* Update Ingress-Nginx version controller-v1.9.1
|
||||
|
||||
**Full Changelog**: https://github.com/kubernetes/ingress-nginx/compare/helm-chart-4.8.0...helm-chart-4.8.1
|
||||
@@ -198,15 +198,20 @@ IngressClass parameters.
|
||||
Extra modules.
|
||||
*/}}
|
||||
{{- define "extraModules" -}}
|
||||
|
||||
- name: {{ .name }}
|
||||
image: {{ .image }}
|
||||
{{- if .distroless | default false }}
|
||||
command: ['/init_module']
|
||||
{{- else }}
|
||||
command: ['sh', '-c', '/usr/local/bin/init_module.sh']
|
||||
{{- if (.containerSecurityContext) }}
|
||||
{{- end }}
|
||||
{{- if .containerSecurityContext }}
|
||||
securityContext: {{ .containerSecurityContext | toYaml | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- if .resources }}
|
||||
resources: {{ .resources | toYaml | nindent 4 }}
|
||||
{{- end }}
|
||||
volumeMounts:
|
||||
- name: {{ toYaml "modules"}}
|
||||
mountPath: {{ toYaml "/modules_mount"}}
|
||||
|
||||
{{- end -}}
|
||||
|
||||
@@ -1,5 +1,8 @@
|
||||
{{- define "ingress-nginx.params" -}}
|
||||
- /nginx-ingress-controller
|
||||
{{- if .Values.controller.enableAnnotationValidations }}
|
||||
- --enable-annotation-validation=true
|
||||
{{- end }}
|
||||
{{- if .Values.defaultBackend.enabled }}
|
||||
- --default-backend-service=$(POD_NAMESPACE)/{{ include "ingress-nginx.defaultBackend.fullname" . }}
|
||||
{{- end }}
|
||||
|
||||
@@ -1,4 +1,4 @@
|
||||
{{- if and .Values.controller.admissionWebhooks.enabled .Values.controller.admissionWebhooks.networkPolicyEnabled }}
|
||||
{{- if and .Values.controller.admissionWebhooks.enabled .Values.controller.admissionWebhooks.patch.enabled (not .Values.controller.admissionWebhooks.certManager.enabled) -}}
|
||||
apiVersion: networking.k8s.io/v1
|
||||
kind: NetworkPolicy
|
||||
metadata:
|
||||
@@ -16,11 +16,11 @@ metadata:
|
||||
spec:
|
||||
podSelector:
|
||||
matchLabels:
|
||||
{{- include "ingress-nginx.labels" . | nindent 6 }}
|
||||
{{- include "ingress-nginx.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: admission-webhook
|
||||
policyTypes:
|
||||
- Ingress
|
||||
- Egress
|
||||
- Ingress
|
||||
- Egress
|
||||
egress:
|
||||
- {}
|
||||
- {}
|
||||
{{- end }}
|
||||
|
||||
@@ -1,3 +1,4 @@
|
||||
{{- if not (eq .Values.kind "Vanilla") -}}
|
||||
{{- if and (eq "standalone" .Values.appsec.mode) (eq .Values.appsec.persistence.enabled true) -}}
|
||||
kind: PersistentVolumeClaim
|
||||
apiVersion: v1
|
||||
@@ -18,3 +19,4 @@ spec:
|
||||
storageClassName: {{ required "A storage class for learning data is required" .Values.appsec.persistence.learning.storageClass.name }}
|
||||
{{- end -}}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@@ -1,4 +1,4 @@
|
||||
{{- if (eq .Values.controller.kind "Deployment") -}}
|
||||
{{- if (and (eq .Values.kind "AppSec") .Values.appsec.persistence.enabled) }}
|
||||
kind: PersistentVolumeClaim
|
||||
apiVersion: v1
|
||||
metadata:
|
||||
|
||||
@@ -0,0 +1,32 @@
|
||||
{{- if not (eq .Values.kind "Vanilla") -}}
|
||||
{{- if .Values.appsec.configMapContent }}
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: {{ .Values.appsec.configMapName | default "appsec-settings-configmap" | quote }}
|
||||
data:
|
||||
{{- if .Values.appsec.configMapContent.crowdsec }}
|
||||
CROWDSEC_ENABLED: {{ .Values.appsec.configMapContent.crowdsec.enabled | default "false" | quote }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.api }}
|
||||
CROWDSEC_API_URL: {{ .Values.appsec.configMapContent.crowdsec.api.url | default "http://crowdsec-service:8080/v1/decisions/stream" }}
|
||||
{{- else }}
|
||||
CROWDSEC_API_URL: "http://crowdsec-service:8080/v1/decisions/stream"
|
||||
{{- end }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.auth }}
|
||||
CROWDSEC_AUTH_METHOD: {{ .Values.appsec.configMapContent.crowdsec.auth.method | default "apikey" }}
|
||||
{{- else }}
|
||||
CROWDSEC_AUTH_METHOD: "apikey"
|
||||
{{- end }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.mode }}
|
||||
CROWDSEC_MODE: {{ .Values.appsec.configMapContent.crowdsec.mode | default "prevent" }}
|
||||
{{- else }}
|
||||
CROWDSEC_MODE: "prevent"
|
||||
{{- end }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.logging }}
|
||||
CROWDSEC_LOGGING: {{ .Values.appsec.configMapContent.crowdsec.logging | default "enabled" }}
|
||||
{{- else }}
|
||||
CROWDSEC_LOGGING: "enabled"
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@@ -0,0 +1,12 @@
|
||||
{{- if not (eq .Values.kind "Vanilla") -}}
|
||||
{{ if .Values.appsec.secretContent }}
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: {{ .Values.appsec.secretName | default "appsec-settings-secret" | quote }}
|
||||
data:
|
||||
{{- if and .Values.appsec.secretContent.crowdsec .Values.appsec.secretContent.crowdsec.auth }}
|
||||
CROWDSEC_AUTH_DATA: {{ .Values.appsec.secretContent.crowdsec.auth.data | b64enc }}
|
||||
{{- end }}
|
||||
{{ end }}
|
||||
{{ end }}
|
||||
@@ -1,6 +1,15 @@
|
||||
{{- if or (eq .Values.controller.kind "StatefulSet") (eq .Values.controller.kind "Both") -}}
|
||||
{{- if (not (eq .Values.kind "Vanilla")) }}
|
||||
{{- include "isControllerTagValid" . -}}
|
||||
apiVersion: apps/v1
|
||||
{{- if (eq .Values.kind "AppSec") }}
|
||||
{{- if (eq .Values.controller.kind "DaemonSet") }}
|
||||
kind: DaemonSet
|
||||
{{- else }}
|
||||
kind: Deployment
|
||||
{{- end }}
|
||||
{{- else if eq .Values.kind "AppSecStateful" }}
|
||||
kind: StatefulSet
|
||||
{{- end }}
|
||||
metadata:
|
||||
labels:
|
||||
{{- include "ingress-nginx.labels" . | nindent 4 }}
|
||||
@@ -18,16 +27,25 @@ spec:
|
||||
matchLabels:
|
||||
{{- include "ingress-nginx.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: controller
|
||||
{{- if not .Values.controller.autoscaling.enabled }}
|
||||
{{- if not (or .Values.controller.autoscaling.enabled .Values.controller.keda.enabled) }}
|
||||
{{- if eq .Values.kind "AppSecStateful" }}
|
||||
serviceName: "open-appsec-stateful-set"
|
||||
{{- end }}
|
||||
{{- if or (not (eq .Values.controller.kind "DaemonSet")) (and (eq .Values.kind "AppSecStateful") (eq .Values.controller.kind "DaemonSet")) }}
|
||||
replicas: {{ .Values.controller.replicaCount }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
revisionHistoryLimit: {{ .Values.revisionHistoryLimit }}
|
||||
{{- if .Values.controller.updateStrategy }}
|
||||
strategy:
|
||||
{{ toYaml .Values.controller.updateStrategy | nindent 4 }}
|
||||
{{- if (and (not (eq .Values.kind "AppSecStateful")) (eq .Values.controller.kind "DaemonSet")) }}
|
||||
updateStrategy: {{ toYaml .Values.controller.updateStrategy | nindent 4 }}:
|
||||
{{- else }}
|
||||
strategy: {{ toYaml .Values.controller.updateStrategy | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if (eq .Values.kind "AppSec") }}
|
||||
minReadySeconds: {{ .Values.controller.minReadySeconds }}
|
||||
{{- end }}
|
||||
#minReadySeconds: {{ .Values.controller.minReadySeconds }}
|
||||
template:
|
||||
metadata:
|
||||
{{- if .Values.controller.podAnnotations }}
|
||||
@@ -49,6 +67,9 @@ spec:
|
||||
{{- if .Values.controller.dnsConfig }}
|
||||
dnsConfig: {{ toYaml .Values.controller.dnsConfig | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.hostAliases }}
|
||||
hostAliases: {{ tpl (toYaml .Values.controller.hostAliases) $ | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.hostname }}
|
||||
hostname: {{ toYaml .Values.controller.hostname | nindent 8 }}
|
||||
{{- end }}
|
||||
@@ -79,6 +100,10 @@ spec:
|
||||
- name: {{ .Values.appsec.name }}
|
||||
securityContext:
|
||||
{{ toYaml .Values.appsec.securityContext | nindent 12 }}
|
||||
{{- $tag := .Values.appsec.image.tag }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.enabled }}
|
||||
{{- $tag = "crowdsec-1.2314-rc1" }}
|
||||
{{- end }}
|
||||
{{- with .Values.appsec.image }}
|
||||
image: "{{- if .registry }}{{ .registry }}/{{- end }}{{- if .repository }}{{ .repository }}/{{- end }}{{ .image }}{{- if .tag }}:{{ .tag }}{{- end }}{{- if (.digest) -}} @{{.digest}} {{- end }}"
|
||||
{{- end }}
|
||||
@@ -106,6 +131,8 @@ spec:
|
||||
env:
|
||||
- name: user_email
|
||||
value: {{ .Values.appsec.userEmail }}
|
||||
- name: registered_server
|
||||
value: "NGINX Server"
|
||||
{{- if eq .Values.appsec.playground false }}
|
||||
- name: SHARED_STORAGE_HOST
|
||||
value: {{ .Values.appsec.storage.name }}-svc
|
||||
@@ -115,20 +142,29 @@ spec:
|
||||
- name: PLAYGROUND
|
||||
value: "true"
|
||||
{{- end }}
|
||||
envFrom:
|
||||
- configMapRef:
|
||||
name: {{ .Values.appsec.configMapName | default "appsec-settings-configmap" }}
|
||||
- secretRef:
|
||||
name: {{ .Values.appsec.secretName | default "appsec-settings-secret" }}
|
||||
resources:
|
||||
{{ toYaml .Values.resources | nindent 12 }}
|
||||
volumeMounts:
|
||||
- name: advanced-model
|
||||
mountPath: /advanced-model
|
||||
{{- if .Values.appsec.persistence.enabled }}
|
||||
{{- if (eq .Values.appsec.persistence.enabled true) }}
|
||||
- name: appsec-conf
|
||||
mountPath: /etc/cp/conf
|
||||
- name: appsec-data
|
||||
mountPath: /etc/cp/data
|
||||
{{- end }}
|
||||
- name: {{ .Values.controller.containerName }}
|
||||
{{- with .Values.controller.image }}
|
||||
image: "{{- if .registry }}{{ .registry }}/{{- end }}{{- if .repository }}{{ .repository }}/{{- end }}{{ .image }}{{- if .tag }}:{{ .tag }}{{- end }}{{- if (.digest) -}} @{{.digest}} {{- end }}"
|
||||
{{- $tag := .Values.appsec.nginx.image.tag }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.enabled }}
|
||||
{{- $tag = "1.2303.1-rc1-v1.3.0" }}
|
||||
{{- end }}
|
||||
{{- with .Values.appsec.nginx.image }}
|
||||
image: "{{ .repository }}:{{ .tag }}"
|
||||
{{- end }}
|
||||
imagePullPolicy: {{ .Values.controller.image.pullPolicy }}
|
||||
{{- if .Values.controller.lifecycle }}
|
||||
@@ -234,13 +270,14 @@ spec:
|
||||
{{- end }}
|
||||
{{- if .Values.controller.extraModules }}
|
||||
{{- range .Values.controller.extraModules }}
|
||||
{{ $containerSecurityContext := .containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{ include "extraModules" (dict "name" .name "image" .image "containerSecurityContext" $containerSecurityContext) | indent 8 }}
|
||||
{{- $containerSecurityContext := .containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{- include "extraModules" (dict "name" .name "image" .image "containerSecurityContext" $containerSecurityContext) | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.opentelemetry.enabled}}
|
||||
{{ $otelContainerSecurityContext := $.Values.controller.opentelemetry.containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{- include "extraModules" (dict "name" "opentelemetry" "image" .Values.controller.opentelemetry.image "containerSecurityContext" $otelContainerSecurityContext) | nindent 8}}
|
||||
{{- $otelContainerSecurityContext := $.Values.controller.opentelemetry.containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{ $otelResources := $.Values.controller.opentelemetry.resources | default dict }}
|
||||
{{- include "extraModules" (dict "name" "opentelemetry" "image" .Values.controller.opentelemetry.image "containerSecurityContext" $otelContainerSecurityContext "distroless" true "resources" $otelResources) | nindent 8}}
|
||||
{{- end}}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.hostNetwork }}
|
||||
@@ -256,7 +293,7 @@ spec:
|
||||
affinity: {{ toYaml .Values.controller.affinity | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.topologySpreadConstraints }}
|
||||
topologySpreadConstraints: {{ toYaml .Values.controller.topologySpreadConstraints | nindent 8 }}
|
||||
topologySpreadConstraints: {{ tpl (toYaml .Values.controller.topologySpreadConstraints) $ | nindent 8 }}
|
||||
{{- end }}
|
||||
serviceAccountName: {{ template "ingress-nginx.serviceAccountName" . }}
|
||||
terminationGracePeriodSeconds: {{ .Values.controller.terminationGracePeriodSeconds }}
|
||||
@@ -266,6 +303,14 @@ spec:
|
||||
configMap:
|
||||
name: advanced-model-config
|
||||
optional: true
|
||||
{{- if (and (eq .Values.kind "AppSec") .Values.appsec.persistence.enabled) }}
|
||||
- name: appsec-conf
|
||||
persistentVolumeClaim:
|
||||
claimName: {{ .Values.appsec.name }}-conf
|
||||
- name: appsec-data
|
||||
persistentVolumeClaim:
|
||||
claimName: {{ .Values.appsec.name }}-data
|
||||
{{- end }}
|
||||
{{- if (or .Values.controller.extraModules .Values.controller.opentelemetry.enabled)}}
|
||||
- name: modules
|
||||
emptyDir: {}
|
||||
@@ -294,7 +339,7 @@ spec:
|
||||
{{ toYaml .Values.controller.extraVolumes | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.appsec.persistence.enabled }}
|
||||
{{- if (and (eq .Values.kind "AppSecStateful") .Values.appsec.persistence.enabled) }}
|
||||
volumeClaimTemplates:
|
||||
- metadata:
|
||||
name: appsec-conf
|
||||
@@ -1,4 +1,4 @@
|
||||
{{- if or (eq .Values.controller.kind "DaemonSet") (eq .Values.controller.kind "Both") -}}
|
||||
{{- if and (eq .Values.kind "Vanilla") (or (eq .Values.controller.kind "DaemonSet") (eq .Values.controller.kind "Both")) -}}
|
||||
{{- include "isControllerTagValid" . -}}
|
||||
apiVersion: apps/v1
|
||||
kind: DaemonSet
|
||||
@@ -45,6 +45,9 @@ spec:
|
||||
{{- if .Values.controller.dnsConfig }}
|
||||
dnsConfig: {{ toYaml .Values.controller.dnsConfig | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.hostAliases }}
|
||||
hostAliases: {{ tpl (toYaml .Values.controller.hostAliases) $ | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.hostname }}
|
||||
hostname: {{ toYaml .Values.controller.hostname | nindent 8 }}
|
||||
{{- end }}
|
||||
@@ -53,12 +56,12 @@ spec:
|
||||
imagePullSecrets: {{ toYaml .Values.imagePullSecrets | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.priorityClassName }}
|
||||
priorityClassName: {{ .Values.controller.priorityClassName }}
|
||||
priorityClassName: {{ .Values.controller.priorityClassName | quote }}
|
||||
{{- end }}
|
||||
{{- if or .Values.controller.podSecurityContext .Values.controller.sysctls }}
|
||||
securityContext:
|
||||
{{- end }}
|
||||
{{- if .Values.controller.podSecurityContext }}
|
||||
{{- if .Values.controller.podSecurityContext }}
|
||||
{{- toYaml .Values.controller.podSecurityContext | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.sysctls }}
|
||||
@@ -143,11 +146,15 @@ spec:
|
||||
hostPort: {{ $key }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if (or .Values.controller.customTemplate.configMapName .Values.controller.extraVolumeMounts .Values.controller.admissionWebhooks.enabled .Values.controller.extraModules) }}
|
||||
{{- if (or .Values.controller.customTemplate.configMapName .Values.controller.extraVolumeMounts .Values.controller.admissionWebhooks.enabled .Values.controller.extraModules .Values.controller.opentelemetry.enabled) }}
|
||||
volumeMounts:
|
||||
{{- if .Values.controller.extraModules }}
|
||||
{{- if (or .Values.controller.extraModules .Values.controller.opentelemetry.enabled) }}
|
||||
- name: modules
|
||||
{{ if .Values.controller.image.chroot }}
|
||||
mountPath: /chroot/modules_mount
|
||||
{{ else }}
|
||||
mountPath: /modules_mount
|
||||
{{ end }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.customTemplate.configMapName }}
|
||||
- mountPath: /etc/nginx/template
|
||||
@@ -169,22 +176,21 @@ spec:
|
||||
{{- if .Values.controller.extraContainers }}
|
||||
{{ toYaml .Values.controller.extraContainers | nindent 8 }}
|
||||
{{- end }}
|
||||
|
||||
|
||||
{{- if (or .Values.controller.extraInitContainers .Values.controller.extraModules) }}
|
||||
{{- if (or .Values.controller.extraInitContainers .Values.controller.extraModules .Values.controller.opentelemetry.enabled) }}
|
||||
initContainers:
|
||||
{{- if .Values.controller.extraInitContainers }}
|
||||
{{ toYaml .Values.controller.extraInitContainers | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.extraModules }}
|
||||
{{- range .Values.controller.extraModules }}
|
||||
{{ $containerSecurityContext := .containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{ include "extraModules" (dict "name" .name "image" .image "containerSecurityContext" $containerSecurityContext) | indent 8 }}
|
||||
{{- $containerSecurityContext := .containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{- include "extraModules" (dict "name" .name "image" .image "containerSecurityContext" $containerSecurityContext) | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.opentelemetry.enabled}}
|
||||
{{ $otelContainerSecurityContext := $.Values.controller.opentelemetry.containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{- include "extraModules" (dict "name" "opentelemetry" "image" .Values.controller.opentelemetry.image "containerSecurityContext" $otelContainerSecurityContext) | nindent 8}}
|
||||
{{- $otelContainerSecurityContext := $.Values.controller.opentelemetry.containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{ $otelResources := $.Values.controller.opentelemetry.resources | default dict }}
|
||||
{{- include "extraModules" (dict "name" "opentelemetry" "image" .Values.controller.opentelemetry.image "containerSecurityContext" $otelContainerSecurityContext "distroless" true "resources" $otelResources) | nindent 8}}
|
||||
{{- end}}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.hostNetwork }}
|
||||
@@ -200,7 +206,7 @@ spec:
|
||||
affinity: {{ toYaml .Values.controller.affinity | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.topologySpreadConstraints }}
|
||||
topologySpreadConstraints: {{ toYaml .Values.controller.topologySpreadConstraints | nindent 8 }}
|
||||
topologySpreadConstraints: {{ tpl (toYaml .Values.controller.topologySpreadConstraints) $ | nindent 8 }}
|
||||
{{- end }}
|
||||
serviceAccountName: {{ template "ingress-nginx.serviceAccountName" . }}
|
||||
terminationGracePeriodSeconds: {{ .Values.controller.terminationGracePeriodSeconds }}
|
||||
|
||||
@@ -1,4 +1,4 @@
|
||||
{{- if or (eq .Values.controller.kind "Deployment") (eq .Values.controller.kind "Both") -}}
|
||||
{{- if and (eq .Values.kind "Vanilla") (or (eq .Values.controller.kind "Deployment") (eq .Values.controller.kind "Both")) -}}
|
||||
{{- include "isControllerTagValid" . -}}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
@@ -19,13 +19,12 @@ spec:
|
||||
matchLabels:
|
||||
{{- include "ingress-nginx.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: controller
|
||||
{{- if not .Values.controller.autoscaling.enabled }}
|
||||
{{- if not (or .Values.controller.autoscaling.enabled .Values.controller.keda.enabled) }}
|
||||
replicas: {{ .Values.controller.replicaCount }}
|
||||
{{- end }}
|
||||
revisionHistoryLimit: {{ .Values.revisionHistoryLimit }}
|
||||
{{- if .Values.controller.updateStrategy }}
|
||||
strategy:
|
||||
{{ toYaml .Values.controller.updateStrategy | nindent 4 }}
|
||||
strategy: {{ toYaml .Values.controller.updateStrategy | nindent 4 }}
|
||||
{{- end }}
|
||||
minReadySeconds: {{ .Values.controller.minReadySeconds }}
|
||||
template:
|
||||
@@ -49,6 +48,9 @@ spec:
|
||||
{{- if .Values.controller.dnsConfig }}
|
||||
dnsConfig: {{ toYaml .Values.controller.dnsConfig | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.hostAliases }}
|
||||
hostAliases: {{ tpl (toYaml .Values.controller.hostAliases) $ | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.hostname }}
|
||||
hostname: {{ toYaml .Values.controller.hostname | nindent 8 }}
|
||||
{{- end }}
|
||||
@@ -76,59 +78,9 @@ spec:
|
||||
shareProcessNamespace: {{ .Values.controller.shareProcessNamespace }}
|
||||
{{- end }}
|
||||
containers:
|
||||
- name: {{ .Values.appsec.name }}
|
||||
securityContext:
|
||||
{{ toYaml .Values.appsec.securityContext | nindent 12 }}
|
||||
{{- with .Values.appsec.image }}
|
||||
image: "{{- if .registry }}{{ .registry }}/{{- end }}{{- if .repository }}{{ .repository }}/{{- end }}{{ .image }}{{- if .tag }}:{{ .tag }}{{- end }}{{- if (.digest) -}} @{{.digest}} {{- end }}"
|
||||
{{- end }}
|
||||
command:
|
||||
- {{ .Values.appsec.command }}
|
||||
imagePullPolicy: {{ .Values.appsec.image.pullPolicy }}
|
||||
args:
|
||||
{{- if (eq "standalone" .Values.appsec.mode) }}
|
||||
- --hybrid-mode
|
||||
- --token
|
||||
- cp-3fb5c718-5e39-47e6-8d5e-99b4bc5660b74b4b7fc8-5312-451d-a763-aaf7872703c0
|
||||
{{- else }}
|
||||
- --token
|
||||
- {{ .Values.appsec.agentToken }}
|
||||
{{- end -}}
|
||||
{{- if .Values.appsec.customFog.enabled }}
|
||||
- --fog
|
||||
- {{ .Values.appsec.customFog.fogAddress }}
|
||||
{{- end }}
|
||||
{{- if .Values.appsec.proxy }}
|
||||
- --proxy
|
||||
- {{ .Values.appsec.proxy }}
|
||||
{{- end }}
|
||||
imagePullPolicy: {{ .Values.appsec.image.pullPolicy }}
|
||||
env:
|
||||
- name: user_email
|
||||
value: {{ .Values.appsec.userEmail }}
|
||||
{{- if eq .Values.appsec.playground false }}
|
||||
- name: SHARED_STORAGE_HOST
|
||||
value: {{ .Values.appsec.storage.name }}-svc
|
||||
- name: LEARNING_HOST
|
||||
value: {{ .Values.appsec.learning.name }}-svc
|
||||
{{- else }}
|
||||
- name: PLAYGROUND
|
||||
value: "true"
|
||||
{{- end }}
|
||||
resources:
|
||||
{{ toYaml .Values.resources | nindent 12 }}
|
||||
volumeMounts:
|
||||
- name: advanced-model
|
||||
mountPath: /advanced-model
|
||||
{{- if .Values.appsec.persistence.enabled }}
|
||||
- name: appsec-conf
|
||||
mountPath: /etc/cp/conf
|
||||
- name: appsec-data
|
||||
mountPath: /etc/cp/data
|
||||
{{- end }}
|
||||
- name: {{ .Values.controller.containerName }}
|
||||
{{- with .Values.controller.image }}
|
||||
image: "{{- if .registry }}{{ .registry }}/{{- end }}{{- if .repository }}{{ .repository }}/{{- end }}{{ .image }}{{- if .tag }}:{{ .tag }}{{- end }}{{- if (.digest) -}} @{{.digest}} {{- end }}"
|
||||
image: "{{- if .repository -}}{{ .repository }}{{ else }}{{ .registry }}/{{ include "ingress-nginx.image" . }}{{- end -}}:{{ .tag }}{{ include "ingress-nginx.imageDigest" . }}"
|
||||
{{- end }}
|
||||
imagePullPolicy: {{ .Values.controller.image.pullPolicy }}
|
||||
{{- if .Values.controller.lifecycle }}
|
||||
@@ -234,13 +186,14 @@ spec:
|
||||
{{- end }}
|
||||
{{- if .Values.controller.extraModules }}
|
||||
{{- range .Values.controller.extraModules }}
|
||||
{{ $containerSecurityContext := .containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{ include "extraModules" (dict "name" .name "image" .image "containerSecurityContext" $containerSecurityContext) | indent 8 }}
|
||||
{{- $containerSecurityContext := .containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{- include "extraModules" (dict "name" .name "image" .image "containerSecurityContext" $containerSecurityContext) | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.opentelemetry.enabled}}
|
||||
{{ $otelContainerSecurityContext := $.Values.controller.opentelemetry.containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{- include "extraModules" (dict "name" "opentelemetry" "image" .Values.controller.opentelemetry.image "containerSecurityContext" $otelContainerSecurityContext) | nindent 8}}
|
||||
{{- $otelContainerSecurityContext := $.Values.controller.opentelemetry.containerSecurityContext | default $.Values.controller.containerSecurityContext }}
|
||||
{{ $otelResources := $.Values.controller.opentelemetry.resources | default dict }}
|
||||
{{- include "extraModules" (dict "name" "opentelemetry" "image" .Values.controller.opentelemetry.image "containerSecurityContext" $otelContainerSecurityContext "distroless" true "resources" $otelResources) | nindent 8}}
|
||||
{{- end}}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.hostNetwork }}
|
||||
@@ -256,18 +209,12 @@ spec:
|
||||
affinity: {{ toYaml .Values.controller.affinity | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.topologySpreadConstraints }}
|
||||
topologySpreadConstraints: {{ toYaml .Values.controller.topologySpreadConstraints | nindent 8 }}
|
||||
topologySpreadConstraints: {{ tpl (toYaml .Values.controller.topologySpreadConstraints) $ | nindent 8 }}
|
||||
{{- end }}
|
||||
serviceAccountName: {{ template "ingress-nginx.serviceAccountName" . }}
|
||||
terminationGracePeriodSeconds: {{ .Values.controller.terminationGracePeriodSeconds }}
|
||||
volumes:
|
||||
- name: appsec-conf
|
||||
persistentVolumeClaim:
|
||||
claimName: {{ .Values.appsec.name }}-conf
|
||||
- name: appsec-data
|
||||
persistentVolumeClaim:
|
||||
claimName: {{ .Values.appsec.name }}-data
|
||||
{{- if (or .Values.controller.customTemplate.configMapName .Values.controller.extraVolumeMounts .Values.controller.admissionWebhooks.enabled .Values.controller.extraVolumes .Values.controller.extraModules .Values.controller.opentelemetry.enabled) }}
|
||||
volumes:
|
||||
{{- if (or .Values.controller.extraModules .Values.controller.opentelemetry.enabled)}}
|
||||
- name: modules
|
||||
emptyDir: {}
|
||||
|
||||
@@ -1,12 +1,9 @@
|
||||
{{- if and .Values.controller.autoscaling.enabled (or (eq .Values.controller.kind "Deployment") (eq .Values.controller.kind "Both")) -}}
|
||||
{{- if not .Values.controller.keda.enabled }}
|
||||
|
||||
apiVersion: {{ .Values.controller.autoscaling.apiVersion }}
|
||||
{{- if and (or (eq .Values.controller.kind "Deployment") (eq .Values.controller.kind "Both")) .Values.controller.autoscaling.enabled (not .Values.controller.keda.enabled) -}}
|
||||
apiVersion: {{ ternary "autoscaling/v2" "autoscaling/v2beta2" (.Capabilities.APIVersions.Has "autoscaling/v2") }}
|
||||
kind: HorizontalPodAutoscaler
|
||||
metadata:
|
||||
annotations:
|
||||
{{- with .Values.controller.autoscaling.annotations }}
|
||||
{{- toYaml . | trimSuffix "\n" | nindent 4 }}
|
||||
annotations: {{ toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "ingress-nginx.labels" . | nindent 4 }}
|
||||
@@ -48,5 +45,3 @@ spec:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
|
||||
@@ -25,6 +25,11 @@ spec:
|
||||
cooldownPeriod: {{ .Values.controller.keda.cooldownPeriod }}
|
||||
minReplicaCount: {{ .Values.controller.keda.minReplicas }}
|
||||
maxReplicaCount: {{ .Values.controller.keda.maxReplicas }}
|
||||
{{- with .Values.controller.keda.fallback }}
|
||||
fallback:
|
||||
failureThreshold: {{ .failureThreshold | default 3 }}
|
||||
replicas: {{ .replicas | default $.Values.controller.keda.maxReplicas }}
|
||||
{{- end }}
|
||||
triggers:
|
||||
{{- with .Values.controller.keda.triggers }}
|
||||
{{ toYaml . | indent 2 }}
|
||||
|
||||
@@ -0,0 +1,45 @@
|
||||
{{- if .Values.controller.networkPolicy.enabled }}
|
||||
apiVersion: networking.k8s.io/v1
|
||||
kind: NetworkPolicy
|
||||
metadata:
|
||||
labels:
|
||||
{{- include "ingress-nginx.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: controller
|
||||
{{- with .Values.controller.labels }}
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
name: {{ include "ingress-nginx.controller.fullname" . }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
podSelector:
|
||||
matchLabels:
|
||||
{{- include "ingress-nginx.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: controller
|
||||
policyTypes:
|
||||
- Ingress
|
||||
- Egress
|
||||
ingress:
|
||||
- ports:
|
||||
{{- range $key, $value := .Values.controller.containerPort }}
|
||||
- protocol: TCP
|
||||
port: {{ $value }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.metrics.enabled }}
|
||||
- protocol: TCP
|
||||
port: {{ .Values.controller.metrics.port }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.admissionWebhooks.enabled }}
|
||||
- protocol: TCP
|
||||
port: {{ .Values.controller.admissionWebhooks.port }}
|
||||
{{- end }}
|
||||
{{- range $key, $value := .Values.tcp }}
|
||||
- protocol: TCP
|
||||
port: {{ $key }}
|
||||
{{- end }}
|
||||
{{- range $key, $value := .Values.udp }}
|
||||
- protocol: UDP
|
||||
port: {{ $key }}
|
||||
{{- end }}
|
||||
egress:
|
||||
- {}
|
||||
{{- end }}
|
||||
@@ -10,12 +10,15 @@ metadata:
|
||||
{{- end }}
|
||||
name: {{ include "ingress-nginx.controller.fullname" . }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- if .Values.controller.annotations }}
|
||||
annotations: {{ toYaml .Values.controller.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
{{- include "ingress-nginx.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: controller
|
||||
{{- if .Values.controller.minAvailable }}
|
||||
{{- if and .Values.controller.minAvailable (not (hasKey .Values.controller "maxUnavailable")) }}
|
||||
minAvailable: {{ .Values.controller.minAvailable }}
|
||||
{{- else if .Values.controller.maxUnavailable }}
|
||||
maxUnavailable: {{ .Values.controller.maxUnavailable }}
|
||||
|
||||
@@ -4,7 +4,7 @@ kind: Service
|
||||
metadata:
|
||||
annotations:
|
||||
{{- range $key, $value := .Values.controller.service.internal.annotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{ $key }}: {{ tpl ($value | toString) $ | quote }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "ingress-nginx.labels" . | nindent 4 }}
|
||||
|
||||
@@ -4,7 +4,7 @@ kind: Service
|
||||
metadata:
|
||||
annotations:
|
||||
{{- range $key, $value := .Values.controller.service.annotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{ $key }}: {{ tpl ($value | toString) $ | quote }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "ingress-nginx.labels" . | nindent 4 }}
|
||||
@@ -28,6 +28,9 @@ spec:
|
||||
{{- if .Values.controller.service.loadBalancerSourceRanges }}
|
||||
loadBalancerSourceRanges: {{ toYaml .Values.controller.service.loadBalancerSourceRanges | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.service.loadBalancerClass }}
|
||||
loadBalancerClass: {{ .Values.controller.service.loadBalancerClass }}
|
||||
{{- end }}
|
||||
{{- if .Values.controller.service.externalTrafficPolicy }}
|
||||
externalTrafficPolicy: {{ .Values.controller.service.externalTrafficPolicy }}
|
||||
{{- end }}
|
||||
|
||||
@@ -11,8 +11,7 @@ metadata:
|
||||
name: {{ template "ingress-nginx.serviceAccountName" . }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- if .Values.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.serviceAccount.annotations | nindent 4 }}
|
||||
annotations: {{ toYaml .Values.serviceAccount.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
automountServiceAccountToken: {{ .Values.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end }}
|
||||
|
||||
@@ -5,6 +5,8 @@ metadata:
|
||||
name: {{ include "ingress-nginx.controller.fullname" . }}
|
||||
{{- if .Values.controller.metrics.serviceMonitor.namespace }}
|
||||
namespace: {{ .Values.controller.metrics.serviceMonitor.namespace | quote }}
|
||||
{{- else }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "ingress-nginx.labels" . | nindent 4 }}
|
||||
|
||||
@@ -1,19 +0,0 @@
|
||||
{{- if .Values.controller.admissionWebhooks.enabled }}
|
||||
{{- if .Values.controller.admissionWebhooks.networkPolicyEnabled }}
|
||||
|
||||
apiVersion: networking.k8s.io/v1
|
||||
kind: NetworkPolicy
|
||||
metadata:
|
||||
name: {{ include "ingress-nginx.fullname" . }}-webhooks-allow
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
ingress:
|
||||
- {}
|
||||
podSelector:
|
||||
matchLabels:
|
||||
app.kubernetes.io/name: {{ include "ingress-nginx.name" . }}
|
||||
policyTypes:
|
||||
- Ingress
|
||||
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@@ -1,37 +1,40 @@
|
||||
{{- if and .Values.defaultBackend.enabled .Values.defaultBackend.autoscaling.enabled }}
|
||||
apiVersion: {{ .Values.defaultBackend.autoscaling.apiVersion }}
|
||||
apiVersion: {{ ternary "autoscaling/v2" "autoscaling/v2beta2" (.Capabilities.APIVersions.Has "autoscaling/v2") }}
|
||||
kind: HorizontalPodAutoscaler
|
||||
metadata:
|
||||
{{- with .Values.defaultBackend.autoscaling.annotations }}
|
||||
annotations: {{ toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "ingress-nginx.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: default-backend
|
||||
{{- with .Values.defaultBackend.labels }}
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
name: {{ template "ingress-nginx.defaultBackend.fullname" . }}
|
||||
name: {{ include "ingress-nginx.defaultBackend.fullname" . }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
scaleTargetRef:
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
name: {{ template "ingress-nginx.defaultBackend.fullname" . }}
|
||||
name: {{ include "ingress-nginx.defaultBackend.fullname" . }}
|
||||
minReplicas: {{ .Values.defaultBackend.autoscaling.minReplicas }}
|
||||
maxReplicas: {{ .Values.defaultBackend.autoscaling.maxReplicas }}
|
||||
metrics:
|
||||
{{- with .Values.defaultBackend.autoscaling.targetCPUUtilizationPercentage }}
|
||||
- type: Resource
|
||||
resource:
|
||||
name: cpu
|
||||
target:
|
||||
type: Utilization
|
||||
averageUtilization: {{ . }}
|
||||
{{- end }}
|
||||
{{- with .Values.defaultBackend.autoscaling.targetMemoryUtilizationPercentage }}
|
||||
- type: Resource
|
||||
resource:
|
||||
name: memory
|
||||
target:
|
||||
type: Utilization
|
||||
averageUtilization: {{ . }}
|
||||
{{- end }}
|
||||
{{- with .Values.defaultBackend.autoscaling.targetCPUUtilizationPercentage }}
|
||||
- type: Resource
|
||||
resource:
|
||||
name: cpu
|
||||
target:
|
||||
type: Utilization
|
||||
averageUtilization: {{ . }}
|
||||
{{- end }}
|
||||
{{- with .Values.defaultBackend.autoscaling.targetMemoryUtilizationPercentage }}
|
||||
- type: Resource
|
||||
resource:
|
||||
name: memory
|
||||
target:
|
||||
type: Utilization
|
||||
averageUtilization: {{ . }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@@ -0,0 +1,25 @@
|
||||
{{- if and .Values.defaultBackend.enabled .Values.defaultBackend.networkPolicy.enabled }}
|
||||
apiVersion: networking.k8s.io/v1
|
||||
kind: NetworkPolicy
|
||||
metadata:
|
||||
labels:
|
||||
{{- include "ingress-nginx.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: default-backend
|
||||
{{- with .Values.defaultBackend.labels }}
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
name: {{ include "ingress-nginx.defaultBackend.fullname" . }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
podSelector:
|
||||
matchLabels:
|
||||
{{- include "ingress-nginx.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: default-backend
|
||||
policyTypes:
|
||||
- Ingress
|
||||
- Egress
|
||||
ingress:
|
||||
- ports:
|
||||
- protocol: TCP
|
||||
port: {{ .Values.defaultBackend.port }}
|
||||
{{- end }}
|
||||
@@ -1,3 +1,4 @@
|
||||
{{- if not (eq .Values.kind "Vanilla") -}}
|
||||
{{- if and (eq "standalone" .Values.appsec.mode) (eq .Values.appsec.playground false) }}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
@@ -137,3 +138,4 @@ spec:
|
||||
claimName: {{ .Values.appsec.name }}-storage
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@@ -1,3 +1,4 @@
|
||||
{{- if not (eq .Values.kind "Vanilla") -}}
|
||||
{{- if and (eq "standalone" .Values.appsec.mode) (eq .Values.appsec.playground false) }}
|
||||
apiVersion: v1
|
||||
kind: Service
|
||||
@@ -31,3 +32,4 @@ spec:
|
||||
selector:
|
||||
app: {{ .Values.appsec.storage.name }}-lbl
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@@ -15,17 +15,18 @@ commonLabels: {}
|
||||
|
||||
controller:
|
||||
name: controller
|
||||
enableAnnotationValidations: false
|
||||
image:
|
||||
## Keep false as default for now!
|
||||
chroot: false
|
||||
registry: ghcr.io/openappsec
|
||||
image: nginx-ingress-attachment
|
||||
registry: registry.k8s.io
|
||||
image: ingress-nginx/controller
|
||||
## for backwards compatibility consider setting the full image url via the repository value below
|
||||
## use *either* current default registry/image or repository format or installing chart by providing the values.yaml will fail
|
||||
## repository:
|
||||
tag: latest
|
||||
digest:
|
||||
digestChroot: sha256:e35d5ab487861b9d419c570e3530589229224a0762c7b4d2e2222434abb8d988
|
||||
tag: "v1.9.1"
|
||||
digest: sha256:605a737877de78969493a4b1213b21de4ee425d2926906857b98050f57a95b25
|
||||
digestChroot: sha256:2ac744ef08850ee86ad7162451a6879f47c1a41c6a757f6b6f913c52103b8836
|
||||
pullPolicy: IfNotPresent
|
||||
# www-data -> uid 101
|
||||
runAsUser: 101
|
||||
@@ -48,6 +49,16 @@ controller:
|
||||
addHeaders: {}
|
||||
# -- Optionally customize the pod dnsConfig.
|
||||
dnsConfig: {}
|
||||
# -- Optionally customize the pod hostAliases.
|
||||
hostAliases: []
|
||||
# - ip: 127.0.0.1
|
||||
# hostnames:
|
||||
# - foo.local
|
||||
# - bar.local
|
||||
# - ip: 10.1.2.3
|
||||
# hostnames:
|
||||
# - foo.remote
|
||||
# - bar.remote
|
||||
# -- Optionally customize the pod hostname.
|
||||
hostname: {}
|
||||
# -- Optionally change this to ClusterFirstWithHostNet in case you have 'hostNetwork: true'.
|
||||
@@ -55,7 +66,7 @@ controller:
|
||||
# to keep resolving names inside the k8s network, use ClusterFirstWithHostNet.
|
||||
dnsPolicy: ClusterFirst
|
||||
# -- Bare-metal considerations via the host network https://kubernetes.github.io/ingress-nginx/deploy/baremetal/#via-the-host-network
|
||||
# Ingress status was blank because there is no Service exposing the NGINX Ingress controller in a configuration using the host network, the default --publish-service flag used in standard cloud setups does not apply
|
||||
# Ingress status was blank because there is no Service exposing the Ingress-Nginx Controller in a configuration using the host network, the default --publish-service flag used in standard cloud setups does not apply
|
||||
reportNodeInternalIp: false
|
||||
# -- Process Ingress objects without ingressClass annotation/ingressClassName field
|
||||
# Overrides value for --watch-ingress-without-class flag of the controller binary
|
||||
@@ -63,14 +74,14 @@ controller:
|
||||
watchIngressWithoutClass: false
|
||||
# -- Process IngressClass per name (additionally as per spec.controller).
|
||||
ingressClassByName: false
|
||||
# -- This configuration enables Topology Aware Routing feature, used together with service annotation service.kubernetes.io/topology-aware-hints="auto"
|
||||
# -- This configuration enables Topology Aware Routing feature, used together with service annotation service.kubernetes.io/topology-mode="auto"
|
||||
# Defaults to false
|
||||
enableTopologyAwareRouting: false
|
||||
# -- This configuration defines if Ingress Controller should allow users to set
|
||||
# their own *-snippet annotations, otherwise this is forbidden / dropped
|
||||
# when users add those annotations.
|
||||
# Global snippets in ConfigMap are still respected
|
||||
allowSnippetAnnotations: true
|
||||
allowSnippetAnnotations: false
|
||||
# -- Required for use with CNI based kubernetes installations (such as ones set up by kubeadm),
|
||||
# since CNI and hostport don't mix yet. Can be deprecated once https://github.com/kubernetes/kubernetes/issues/23920
|
||||
# is merged
|
||||
@@ -85,6 +96,10 @@ controller:
|
||||
http: 80
|
||||
# -- 'hostPort' https port
|
||||
https: 443
|
||||
# NetworkPolicy for controller component.
|
||||
networkPolicy:
|
||||
# -- Enable 'networkPolicy' or not
|
||||
enabled: false
|
||||
# -- Election ID to use for status update, by default it uses the controller name combined with a suffix of 'leader'
|
||||
electionID: ""
|
||||
## This section refers to the creation of the IngressClass resource
|
||||
@@ -150,7 +165,7 @@ controller:
|
||||
# -- Maxmind license key to download GeoLite2 Databases.
|
||||
## https://blog.maxmind.com/2019/12/18/significant-changes-to-accessing-and-using-geolite2-databases
|
||||
maxmindLicenseKey: ""
|
||||
# -- Additional command line arguments to pass to nginx-ingress-controller
|
||||
# -- Additional command line arguments to pass to Ingress-Nginx Controller
|
||||
# E.g. to specify the default SSL certificate you can use
|
||||
extraArgs: {}
|
||||
## extraArgs:
|
||||
@@ -166,7 +181,7 @@ controller:
|
||||
# name: secret-resource
|
||||
|
||||
# -- Use a `DaemonSet` or `Deployment`
|
||||
kind: StatefulSet
|
||||
kind: Deployment
|
||||
# -- Annotations to be added to the controller Deployment or DaemonSet
|
||||
##
|
||||
annotations: {}
|
||||
@@ -245,19 +260,29 @@ controller:
|
||||
## Ref: https://kubernetes.io/docs/concepts/workloads/pods/pod-topology-spread-constraints/
|
||||
##
|
||||
topologySpreadConstraints: []
|
||||
# - maxSkew: 1
|
||||
# topologyKey: topology.kubernetes.io/zone
|
||||
# whenUnsatisfiable: DoNotSchedule
|
||||
# labelSelector:
|
||||
# - labelSelector:
|
||||
# matchLabels:
|
||||
# app.kubernetes.io/instance: ingress-nginx-internal
|
||||
# app.kubernetes.io/name: '{{ include "ingress-nginx.name" . }}'
|
||||
# app.kubernetes.io/instance: '{{ .Release.Name }}'
|
||||
# app.kubernetes.io/component: controller
|
||||
# topologyKey: topology.kubernetes.io/zone
|
||||
# maxSkew: 1
|
||||
# whenUnsatisfiable: ScheduleAnyway
|
||||
# - labelSelector:
|
||||
# matchLabels:
|
||||
# app.kubernetes.io/name: '{{ include "ingress-nginx.name" . }}'
|
||||
# app.kubernetes.io/instance: '{{ .Release.Name }}'
|
||||
# app.kubernetes.io/component: controller
|
||||
# topologyKey: kubernetes.io/hostname
|
||||
# maxSkew: 1
|
||||
# whenUnsatisfiable: ScheduleAnyway
|
||||
|
||||
# -- `terminationGracePeriodSeconds` to avoid killing pods before we are ready
|
||||
## wait up to five minutes for the drain of connections
|
||||
##
|
||||
terminationGracePeriodSeconds: 300
|
||||
# -- Node labels for controller pod assignment
|
||||
## Ref: https://kubernetes.io/docs/user-guide/node-selection/
|
||||
## Ref: https://kubernetes.io/docs/concepts/scheduling-eviction/assign-pod-node/
|
||||
##
|
||||
nodeSelector:
|
||||
kubernetes.io/os: linux
|
||||
@@ -302,15 +327,16 @@ controller:
|
||||
healthCheckPath: "/healthz"
|
||||
# -- Address to bind the health check endpoint.
|
||||
# It is better to set this option to the internal node address
|
||||
# if the ingress nginx controller is running in the `hostNetwork: true` mode.
|
||||
# if the Ingress-Nginx Controller is running in the `hostNetwork: true` mode.
|
||||
healthCheckHost: ""
|
||||
# -- Annotations to be added to controller pods
|
||||
##
|
||||
podAnnotations: {}
|
||||
replicaCount: 1
|
||||
# -- Define either 'minAvailable' or 'maxUnavailable', never both.
|
||||
# -- Minimum available pods set in PodDisruptionBudget.
|
||||
# Define either 'minAvailable' or 'maxUnavailable', never both.
|
||||
minAvailable: 1
|
||||
# -- Define either 'minAvailable' or 'maxUnavailable', never both.
|
||||
# -- Maximum unavalaile pods set in PodDisruptionBudget. If set, 'minAvailable' is ignored.
|
||||
# maxUnavailable: 1
|
||||
|
||||
## Define requests resources to avoid probe issues due to CPU utilization in busy nodes
|
||||
@@ -326,7 +352,6 @@ controller:
|
||||
memory: 90Mi
|
||||
# Mutually exclusive with keda autoscaling
|
||||
autoscaling:
|
||||
apiVersion: autoscaling/v2
|
||||
enabled: false
|
||||
annotations: {}
|
||||
minReplicas: 1
|
||||
@@ -368,6 +393,9 @@ controller:
|
||||
maxReplicas: 11
|
||||
pollingInterval: 30
|
||||
cooldownPeriod: 300
|
||||
# fallback:
|
||||
# failureThreshold: 3
|
||||
# replicas: 11
|
||||
restoreToOriginalReplicaCount: false
|
||||
scaledObject:
|
||||
annotations: {}
|
||||
@@ -412,17 +440,20 @@ controller:
|
||||
# Will be ignored for Kubernetes versions older than 1.20
|
||||
##
|
||||
appProtocol: true
|
||||
# -- Annotations are mandatory for the load balancer to come up. Varies with the cloud service. Values passed through helm tpl engine.
|
||||
annotations: {}
|
||||
labels: {}
|
||||
# clusterIP: ""
|
||||
|
||||
# -- List of IP addresses at which the controller services are available
|
||||
## Ref: https://kubernetes.io/docs/user-guide/services/#external-ips
|
||||
## Ref: https://kubernetes.io/docs/concepts/services-networking/service/#external-ips
|
||||
##
|
||||
externalIPs: []
|
||||
# -- Used by cloud providers to connect the resulting `LoadBalancer` to a pre-existing static IP according to https://kubernetes.io/docs/concepts/services-networking/service/#loadbalancer
|
||||
loadBalancerIP: ""
|
||||
loadBalancerSourceRanges: []
|
||||
# -- Used by cloud providers to select a load balancer implementation other than the cloud provider default. https://kubernetes.io/docs/concepts/services-networking/service/#load-balancer-class
|
||||
loadBalancerClass: ""
|
||||
enableHttp: true
|
||||
enableHttps: true
|
||||
## Set external traffic policy to: "Local" to preserve source IP on providers supporting it.
|
||||
@@ -471,10 +502,10 @@ controller:
|
||||
internal:
|
||||
# -- Enables an additional internal load balancer (besides the external one).
|
||||
enabled: false
|
||||
# -- Annotations are mandatory for the load balancer to come up. Varies with the cloud service.
|
||||
# -- Annotations are mandatory for the load balancer to come up. Varies with the cloud service. Values passed through helm tpl engine.
|
||||
annotations: {}
|
||||
# loadBalancerIP: ""
|
||||
|
||||
# -- Used by cloud providers to connect the resulting internal LoadBalancer to a pre-existing static IP. Make sure to add to the service the needed annotation to specify the subnet which the static IP belongs to. For instance, `networking.gke.io/internal-load-balancer-subnet` for GCP and `service.beta.kubernetes.io/aws-load-balancer-subnets` for AWS.
|
||||
loadBalancerIP: ""
|
||||
# -- Restrict access For LoadBalancer service. Defaults to 0.0.0.0/0.
|
||||
loadBalancerSourceRanges: []
|
||||
## Set external traffic policy to: "Local" to preserve source IP on
|
||||
@@ -547,9 +578,10 @@ controller:
|
||||
|
||||
opentelemetry:
|
||||
enabled: false
|
||||
image: registry.k8s.io/ingress-nginx/opentelemetry:v20230312-helm-chart-4.5.2-28-g66a760794@sha256:40f766ac4a9832f36f217bb0e98d44c8d38faeccbfe861fbc1a76af7e9ab257f
|
||||
image: registry.k8s.io/ingress-nginx/opentelemetry:v20230721-3e2062ee5@sha256:13bee3f5223883d3ca62fee7309ad02d22ec00ff0d7033e3e9aca7a9f60fd472
|
||||
containerSecurityContext:
|
||||
allowPrivilegeEscalation: false
|
||||
resources: {}
|
||||
admissionWebhooks:
|
||||
annotations: {}
|
||||
# ignore-check.kube-linter.io/no-read-only-rootfs: "This deployment needs write access to root filesystem".
|
||||
@@ -578,7 +610,6 @@ controller:
|
||||
labels: {}
|
||||
# -- Use an existing PSP instead of creating one
|
||||
existingPsp: ""
|
||||
networkPolicyEnabled: false
|
||||
service:
|
||||
annotations: {}
|
||||
# clusterIP: ""
|
||||
@@ -609,8 +640,8 @@ controller:
|
||||
## for backwards compatibility consider setting the full image url via the repository value below
|
||||
## use *either* current default registry/image or repository format or installing chart by providing the values.yaml will fail
|
||||
## repository:
|
||||
tag: v20230312-helm-chart-4.5.2-28-g66a760794
|
||||
digest: sha256:01d181618f270f2a96c04006f33b2699ad3ccb02da48d0f89b22abce084b292f
|
||||
tag: v20230407
|
||||
digest: sha256:543c40fd093964bc9ab509d3e791f9989963021f1e9e4c9c7b6700b02bfb227b
|
||||
pullPolicy: IfNotPresent
|
||||
# -- Provide a priority class name to the webhook patching job
|
||||
##
|
||||
@@ -652,7 +683,7 @@ controller:
|
||||
# clusterIP: ""
|
||||
|
||||
# -- List of IP addresses at which the stats-exporter service is available
|
||||
## Ref: https://kubernetes.io/docs/user-guide/services/#external-ips
|
||||
## Ref: https://kubernetes.io/docs/concepts/services-networking/service/#external-ips
|
||||
##
|
||||
externalIPs: []
|
||||
# loadBalancerIP: ""
|
||||
@@ -810,7 +841,7 @@ defaultBackend:
|
||||
# key: value
|
||||
|
||||
# -- Node labels for default backend pod assignment
|
||||
## Ref: https://kubernetes.io/docs/user-guide/node-selection/
|
||||
## Ref: https://kubernetes.io/docs/concepts/scheduling-eviction/assign-pod-node/
|
||||
##
|
||||
nodeSelector:
|
||||
kubernetes.io/os: linux
|
||||
@@ -838,19 +869,22 @@ defaultBackend:
|
||||
# emptyDir: {}
|
||||
|
||||
autoscaling:
|
||||
apiVersion: autoscaling/v2
|
||||
annotations: {}
|
||||
enabled: false
|
||||
minReplicas: 1
|
||||
maxReplicas: 2
|
||||
targetCPUUtilizationPercentage: 50
|
||||
targetMemoryUtilizationPercentage: 50
|
||||
# NetworkPolicy for default backend component.
|
||||
networkPolicy:
|
||||
# -- Enable 'networkPolicy' or not
|
||||
enabled: false
|
||||
service:
|
||||
annotations: {}
|
||||
# clusterIP: ""
|
||||
|
||||
# -- List of IP addresses at which the default backend service is available
|
||||
## Ref: https://kubernetes.io/docs/user-guide/services/#external-ips
|
||||
## Ref: https://kubernetes.io/docs/concepts/services-networking/service/#external-ips
|
||||
##
|
||||
externalIPs: []
|
||||
# loadBalancerIP: ""
|
||||
@@ -905,9 +939,9 @@ appsec:
|
||||
image:
|
||||
#registry:
|
||||
repository: ghcr.io/openappsec
|
||||
image: agent
|
||||
tag: latest
|
||||
pullPolicy: IfNotPresent
|
||||
image: "agent"
|
||||
tag: "latest"
|
||||
pullPolicy: Always
|
||||
|
||||
securityContext: {}
|
||||
# capabilities:
|
||||
@@ -916,7 +950,26 @@ appsec:
|
||||
# readOnlyRootFilesystem: true
|
||||
# runAsNonRoot: true
|
||||
# runAsUser: 1000
|
||||
|
||||
nginx:
|
||||
image:
|
||||
repository: "ghcr.io/openappsec/nginx-ingress-attachment"
|
||||
tag: "latest"
|
||||
configMapName: appsec-settings-configmap
|
||||
configMapContent:
|
||||
crowdsec:
|
||||
enabled: false
|
||||
mode: prevent
|
||||
logging: enabled
|
||||
api:
|
||||
url: http://crowdsec-service:8080/v1/decisions/stream
|
||||
auth:
|
||||
method: apikey
|
||||
secretName: appsec-settings-secret
|
||||
# If you would like to use your own secret with CrowdSec authentication data, please remove the following block
|
||||
secretContent:
|
||||
crowdsec:
|
||||
auth:
|
||||
data: "00000000000000000000000000000000"
|
||||
resources:
|
||||
# limits:
|
||||
# cpu: 100m
|
||||
@@ -980,3 +1033,8 @@ appsec:
|
||||
image: smartsync-shared-files
|
||||
tag: latest
|
||||
|
||||
# -- For nginx vanilla installation use kind Vanilla (no appsec components).
|
||||
# -- For nginx with appsec installation use kind AppSec (default: nginx + appsec without state).
|
||||
# -- For nginx with appsec (statefulset) installation use kind AppSecStateful.
|
||||
kind: AppSec
|
||||
|
||||
|
||||
@@ -2,6 +2,139 @@
|
||||
|
||||
## Unreleased
|
||||
|
||||
Nothing yet.
|
||||
|
||||
## 2.29.0
|
||||
|
||||
### Improvements
|
||||
* Make it possible to set the admission webhook's `timeoutSeconds`.
|
||||
|
||||
## 2.28.1
|
||||
|
||||
### Fixed
|
||||
|
||||
* The admission webhook now includes Gateway API resources and Ingress
|
||||
resources for controller versions 2.12+. This version introduces new
|
||||
validations for Kong's regex path implementation.
|
||||
|
||||
## 2.28.0
|
||||
|
||||
### Improvements
|
||||
|
||||
* Bump default `kong` image tag to 3.4.
|
||||
[#883](https://github.com/Kong/charts/pull/883)
|
||||
* Bump default ingress controller image tag to 2.12.
|
||||
* Added validation rule for `latency` upstream load balancing algorithm to
|
||||
CRDs. [Upgrade your CRDs](https://github.com/Kong/charts/blob/main/charts/kong/UPGRADE.md#updates-to-crds)
|
||||
when installing this release.
|
||||
|
||||
## 2.27.0
|
||||
|
||||
### Improvements
|
||||
|
||||
* Listens now all support `.address` configuration. This was an existing
|
||||
setting that was not applied properly for some listens.
|
||||
[#881](https://github.com/Kong/charts/pull/881)
|
||||
|
||||
## 2.26.5
|
||||
|
||||
### Fixed
|
||||
|
||||
* Kuma ServiceAccount Token hints and volumes are also available in migrations
|
||||
Pods.
|
||||
[#877](https://github.com/Kong/charts/pull/877)
|
||||
|
||||
## 2.26.4
|
||||
|
||||
### Fixed
|
||||
|
||||
* updated `admin_api_uri` to `admin_gui_api_url` as per [kong documentation](https://docs.konghq.com/gateway/3.4.x/reference/configuration/#admin_api_uri).
|
||||
|
||||
## 2.26.3
|
||||
|
||||
### Fixed
|
||||
|
||||
* Enabled Service and Ingress in Kong Manager for non enterprise users.
|
||||
|
||||
## 2.26.2
|
||||
|
||||
### Fixed
|
||||
|
||||
* Add missing CRD KongConsumerGroup and extend status subresource for CRDs
|
||||
|
||||
## 2.26.1
|
||||
|
||||
### Fixed
|
||||
|
||||
* Fix parsing enterprise tags (like e.g. `3.4.0.0`)
|
||||
[#857](https://github.com/Kong/charts/pull/857)
|
||||
|
||||
## 2.26.0
|
||||
|
||||
### Breaking changes
|
||||
|
||||
2.26 changes the default proxy readiness endpoint for newer Kong versions. This
|
||||
causes an issue in a narrow edge case. If all of the following are true:
|
||||
|
||||
* You use Kong 3.3 or newer.
|
||||
* You use controller 2.10 or older.
|
||||
* You run the controller and proxy in separate Deployments.
|
||||
|
||||
you are affected and should review [the 2.26 upgrade instructions](https://github.com/Kong/charts/blob/main/charts/kong/UPGRADE.md#2260).
|
||||
|
||||
### Improvements
|
||||
|
||||
* Use the Kong 3.3 `/status/ready` endpoint for readiness probes by default if
|
||||
available. If not available, use the old `/status` default.
|
||||
[#844](https://github.com/Kong/charts/pull/844)
|
||||
* Add ArgoCD `Sync` and `BeforeHookCreation` [hook policies](https://argo-cd.readthedocs.io/en/stable/user-guide/resource_hooks/)
|
||||
to the the init and pre-upgrade migrations Jobs.
|
||||
* Add controller's RBAC rules for `KongConsumerGroups` CRD.
|
||||
[#850](https://github.com/Kong/charts/pull/850)
|
||||
* Updated controller version to 2.11.
|
||||
|
||||
## 2.25.0
|
||||
|
||||
- Generate the `adminApiService.name` value from `.Release.Name` rather than
|
||||
hardcoding to `kong`
|
||||
[#839](https://github.com/Kong/charts/pull/839)
|
||||
|
||||
## 2.24.0
|
||||
|
||||
### Improvements
|
||||
|
||||
* Running `tpl` against user-supplied labels and annotations used in Deployment
|
||||
[#814](https://github.com/Kong/charts/pull/814)
|
||||
|
||||
Example:
|
||||
```yaml
|
||||
podLabels:
|
||||
version: "{{ .Values.image.tag }}" # Will render dynamically when overridden downstream
|
||||
```
|
||||
|
||||
* Fail to render templates when PodSecurityPolicy was requested but cluster doesn't
|
||||
serve its API.
|
||||
[#823](https://github.com/Kong/charts/pull/823)
|
||||
* Add support for multiple hosts and tls configurations for Kong proxy `Ingress`.
|
||||
[#813](https://github.com/Kong/charts/pull/813)
|
||||
* Bump postgres default tag to `13.11.0-debian-11-r20` which includes arm64 images.
|
||||
[#834](https://github.com/Kong/charts/pull/834)
|
||||
|
||||
### Fixed
|
||||
|
||||
* Fix Ingress and HPA API versions during capabilities checking
|
||||
[#827](https://github.com/Kong/charts/pull/827)
|
||||
|
||||
## 2.23.0
|
||||
|
||||
### Improvements
|
||||
|
||||
* Add custom label configuration option for Kong proxy `Ingress`.
|
||||
[#812](https://github.com/Kong/charts/pull/812)
|
||||
* Bump default `kong/kubernetes-ingress-controller` image tag to 2.10.
|
||||
Bump default `kong` image tag to 3.3.
|
||||
[#815](https://github.com/Kong/charts/pull/815)
|
||||
|
||||
## 2.22.0
|
||||
|
||||
### Improvements
|
||||
@@ -30,7 +163,7 @@
|
||||
|
||||
## 2.20.2
|
||||
|
||||
### Fixed
|
||||
### Fixed
|
||||
|
||||
* Automatic license provisioning for Gateways managed by Ingress Controllers in Konnect mode
|
||||
is disabled by default.
|
||||
|
||||
@@ -1,5 +1,5 @@
|
||||
apiVersion: v2
|
||||
appVersion: "3.2"
|
||||
appVersion: 1.1.0
|
||||
dependencies:
|
||||
- condition: postgresql.enabled
|
||||
name: postgresql
|
||||
@@ -16,4 +16,4 @@ maintainers:
|
||||
name: open-appsec-kong
|
||||
sources:
|
||||
- https://github.com/Kong/charts/tree/main/charts/kong
|
||||
version: 2.22.0
|
||||
version: 2.29.0
|
||||
|
||||
@@ -71,6 +71,7 @@ $ helm install kong/kong --generate-name
|
||||
- [Sessions](#sessions)
|
||||
- [Email/SMTP](#emailsmtp)
|
||||
- [Prometheus Operator integration](#prometheus-operator-integration)
|
||||
- [Argo CD considerations](#argo-cd-considerations)
|
||||
- [Changelog](https://github.com/Kong/charts/blob/main/charts/kong/CHANGELOG.md)
|
||||
- [Upgrading](https://github.com/Kong/charts/blob/main/charts/kong/UPGRADE.md)
|
||||
- [Seeking help](#seeking-help)
|
||||
@@ -599,7 +600,8 @@ directory.
|
||||
| Parameter | Description | Default |
|
||||
| ---------------------------------- | ------------------------------------------------------------------------------------- | ------------------- |
|
||||
| image.repository | Kong image | `kong` |
|
||||
| image.tag | Kong image version | `2.5` |
|
||||
| image.tag | Kong image version | `3.4` |
|
||||
| image.effectiveSemver | Semantic version to use for version-dependent features (if `tag` is not a semver) | |
|
||||
| image.pullPolicy | Image pull policy | `IfNotPresent` |
|
||||
| image.pullSecrets | Image pull secrets | `null` |
|
||||
| replicaCount | Kong instance count. It has no effect when `autoscaling.enabled` is set to true | `1` |
|
||||
@@ -679,11 +681,13 @@ or `ingress` sections, as it is used only for stream listens.
|
||||
| SVC.externalTrafficPolicy | k8s service's externalTrafficPolicy. Options: Cluster, Local | |
|
||||
| SVC.ingress.enabled | Enable ingress resource creation (works with SVC.type=ClusterIP) | `false` |
|
||||
| SVC.ingress.ingressClassName | Set the ingressClassName to associate this Ingress with an IngressClass | |
|
||||
| SVC.ingress.tls | Name of secret resource, containing TLS secret | |
|
||||
| SVC.ingress.hostname | Ingress hostname | `""` |
|
||||
| SVC.ingress.path | Ingress path. | `/` |
|
||||
| SVC.ingress.pathType | Ingress pathType. One of `ImplementationSpecific`, `Exact` or `Prefix` | `ImplementationSpecific` |
|
||||
| SVC.ingress.hosts | Slice of hosts configurations, including `hostname`, `path` and `pathType` keys | `[]` |
|
||||
| SVC.ingress.tls | Name of secret resource or slice of `secretName` and `hosts` keys | |
|
||||
| SVC.ingress.annotations | Ingress annotations. See documentation for your ingress controller for details | `{}` |
|
||||
| SVC.ingress.labels | Ingress labels. Additional custom labels to add to the ingress. | `{}` |
|
||||
| SVC.annotations | Service annotations | `{}` |
|
||||
| SVC.labels | Service labels | `{}` |
|
||||
|
||||
@@ -721,7 +725,7 @@ section of `values.yaml` file:
|
||||
|--------------------------------------------|----------------------------------------------------------------------------------------------------------------------------------------------------------|------------------------------------|
|
||||
| enabled | Deploy the ingress controller, rbac and crd | true |
|
||||
| image.repository | Docker image with the ingress controller | kong/kubernetes-ingress-controller |
|
||||
| image.tag | Version of the ingress controller | 2.0 |
|
||||
| image.tag | Version of the ingress controller | `2.12` |
|
||||
| image.effectiveSemver | Version of the ingress controller used for version-specific features when image.tag is not a valid semantic version | |
|
||||
| readinessProbe | Kong ingress controllers readiness probe | |
|
||||
| livenessProbe | Kong ingress controllers liveness probe | |
|
||||
@@ -735,15 +739,18 @@ section of `values.yaml` file:
|
||||
| admissionWebhook.enabled | Whether to enable the validating admission webhook | true |
|
||||
| admissionWebhook.failurePolicy | How unrecognized errors from the admission endpoint are handled (Ignore or Fail) | Ignore |
|
||||
| admissionWebhook.port | The port the ingress controller will listen on for admission webhooks | 8080 |
|
||||
| admissionWebhook.address | The address the ingress controller will listen on for admission webhooks, if not 0.0.0.0 | |
|
||||
| admissionWebhook.annotations | Annotations for the Validation Webhook Configuration | |
|
||||
| admissionWebhook.certificate.provided | Use a provided certificate. When set to false, the chart will automatically generate a certificate. | false |
|
||||
| admissionWebhook.certificate.secretName | Name of the TLS secret for the provided webhook certificate | |
|
||||
| admissionWebhook.certificate.caBundle | PEM encoded CA bundle which will be used to validate the provided webhook certificate | |
|
||||
| admissionWebhook.namespaceSelector | Add namespaceSelector to the webhook. Please go to [Kubernetes doc for the specs](https://kubernetes.io/docs/reference/access-authn-authz/extensible-admission-controllers/#matching-requests-namespaceselector) | |
|
||||
| admissionWebhook.timeoutSeconds | Kubernetes `apiserver`'s timeout when running this webhook. Default: 10 seconds. | |
|
||||
| userDefinedVolumes | Create volumes. Please go to Kubernetes doc for the spec of the volumes | |
|
||||
| userDefinedVolumeMounts | Create volumeMounts. Please go to Kubernetes doc for the spec of the volumeMounts | |
|
||||
| terminationGracePeriodSeconds | Sets the [termination grace period](https://kubernetes.io/docs/concepts/containers/container-lifecycle-hooks/#hook-handler-execution) for Deployment pod | 30 |
|
||||
| gatewayDiscovery.enabled | Enables Kong instance service discovery (for more details see [gatewayDiscovery section][gd_section]) | false |
|
||||
| gatewayDiscovery.generateAdminApiService | Generate the admin API service name based on the release name (for more details see [gatewayDiscovery section][gd_section]) | false |
|
||||
| gatewayDiscovery.adminApiService.namespace | The namespace of the Kong admin API service (for more details see [gatewayDiscovery section][gd_section]) | `.Release.Namespace` |
|
||||
| gatewayDiscovery.adminApiService.name | The name of the Kong admin API service (for more details see [gatewayDiscovery section][gd_section]) | "" |
|
||||
| konnect.enabled | Enable synchronisation of data plane configuration with Konnect Runtime Group | false |
|
||||
@@ -796,12 +803,16 @@ You'll be able to configure this feature through configuration section under
|
||||
service.
|
||||
(provided under the hood via `CONTROLLER_KONG_ADMIN_SVC` environment variable).
|
||||
|
||||
The following admin API Service flags have to be provided in order for gateway
|
||||
The following admin API Service flags have to be present in order for gateway
|
||||
discovery to work:
|
||||
|
||||
- `ingressController.gatewayDiscovery.adminApiService.name`
|
||||
- `ingressController.gatewayDiscovery.adminApiService.namespace`
|
||||
|
||||
If you set `ingressController.gatewayDiscovery.generateAdminApiService` to `true`,
|
||||
the chart will generate values for `name` and `namespace` based on the current release name and
|
||||
namespace. This is useful when consuming the `kong` chart as a subchart.
|
||||
|
||||
Using this feature requires a split release installation of Gateways and Ingress Controller.
|
||||
For exemplar `values.yaml` files which use this feature please see: [examples README.md](./example-values/README.md).
|
||||
|
||||
@@ -1038,7 +1049,7 @@ must know where other Kong services (namely the admin and files APIs) can be
|
||||
accessed in order to function properly. Kong's default behavior for attempting
|
||||
to locate these absent configuration is unlikely to work in common Kubernetes
|
||||
environments. Because of this, you should set each of `admin_gui_url`,
|
||||
`admin_api_uri`, `proxy_url`, `portal_api_url`, `portal_gui_host`, and
|
||||
`admin_gui_api_url`, `proxy_url`, `portal_api_url`, `portal_gui_host`, and
|
||||
`portal_gui_protocol` under the `.env` key in values.yaml to locations where
|
||||
each of their respective services can be accessed to ensure that Kong services
|
||||
can locate one another and properly set CORS headers. See the
|
||||
@@ -1154,6 +1165,28 @@ admin:
|
||||
enable-metrics: "true"
|
||||
```
|
||||
|
||||
## Argo CD Considerations
|
||||
|
||||
The built-in database subchart (`postgresql.enabled` in values) is not
|
||||
supported when installing the chart via Argo CD.
|
||||
|
||||
Argo CD does not support the full Helm lifecycle. There is no distinction
|
||||
between the initial install and upgrades. Both operations are a "sync" in Argo
|
||||
terms. This affects when migration Jobs execute in database-backed Kong
|
||||
installs.
|
||||
|
||||
The chart sets the `Sync` and `BeforeHookCreation` deletion
|
||||
[hook policies](https://argo-cd.readthedocs.io/en/stable/user-guide/resource_hooks/)
|
||||
on the `init-migrations` and `pre-upgrade-migrations` Jobs.
|
||||
|
||||
The `pre-upgrade-migrations` Job normally uses Helm's `pre-upgrade` policy. Argo
|
||||
translates this to its `PreSync` policy, which would create the Job before all
|
||||
sync phase resources. Doing this before various sync phase resources (such as
|
||||
the ServiceAccount) are in place would prevent the Job from running
|
||||
successfully. Overriding this with Argo's `Sync` policy starts the Job at the
|
||||
same time as the upgraded Deployment Pods. The new Pods may fail to start
|
||||
temporarily, but will eventually start normally once migrations complete.
|
||||
|
||||
## Seeking help
|
||||
|
||||
If you run into an issue, bug or have a question, please reach out to the Kong
|
||||
|
||||
@@ -17,7 +17,8 @@ upgrading from a previous version.
|
||||
## Table of contents
|
||||
|
||||
- [Upgrade considerations for all versions](#upgrade-considerations-for-all-versions)
|
||||
- [2.17.0](#2170)
|
||||
- [2.26.0](#2260)
|
||||
- [2.19.0](#2190)
|
||||
- [2.13.0](#2130)
|
||||
- [2.8.0](#280)
|
||||
- [2.7.0](#270)
|
||||
@@ -83,6 +84,35 @@ https://raw.githubusercontent.com/Kong/charts/kong-<version>/charts/kong/crds/cu
|
||||
For example, if your release is 2.6.4, you would apply
|
||||
`https://raw.githubusercontent.com/Kong/charts/kong-2.6.4/charts/kong/crds/custom-resource-definitions.yaml`.
|
||||
|
||||
## 2.26.0
|
||||
|
||||
If you are using controller version 2.10 or lower and proxy version 3.3 or
|
||||
higher in separate Deployments (such as when using the `ingress` chart), proxy
|
||||
Pods will not become ready unless you override the default readiness endpoint:
|
||||
|
||||
```
|
||||
readinessProbe:
|
||||
httpGet:
|
||||
path: /status
|
||||
```
|
||||
|
||||
This section goes under the `gateway` section when using the `ingress` chart.
|
||||
|
||||
2.26 changes the default proxy readiness endpoint to the `/status/ready`
|
||||
endpoint introduced in Kong 3.3. This endpoint reports true when Kong has
|
||||
configuration available, whereas the previous `/status` endpoint returned true
|
||||
immediately after start, and could result in proxy instances attempting to
|
||||
serve requests before they had configuration.
|
||||
|
||||
The chart has logic to fall back to the older endpoint if the proxy and
|
||||
controller versions do not work well with the new endpoint. However, the chart
|
||||
detection cannot determine the controller version when the controller is in a
|
||||
separate Deployment, and will always use the new endpoint if the Kong image
|
||||
version is 3.3 or higher.
|
||||
|
||||
Kong recommends Kong 3.3 and higher users update to controller 2.11 at their
|
||||
earliest convenience to take advantage of the improved readiness behavior.
|
||||
|
||||
## 2.19.0
|
||||
|
||||
2.19 sets a default [security context](https://kubernetes.io/docs/tasks/configure-pod-container/security-context/)
|
||||
|
||||
@@ -0,0 +1,18 @@
|
||||
admin:
|
||||
enabled: true
|
||||
type: ClusterIP
|
||||
|
||||
# Stub config to make the instance become ready
|
||||
dblessConfig:
|
||||
config: |
|
||||
_format_version: "1.1"
|
||||
services:
|
||||
- name: example.com
|
||||
url: http://example.com
|
||||
routes:
|
||||
- name: example
|
||||
paths:
|
||||
- "/example"
|
||||
|
||||
ingressController:
|
||||
enabled: false
|
||||
@@ -1,6 +1,3 @@
|
||||
|
||||
# install chart with some extra labels
|
||||
|
||||
extraLabels:
|
||||
acme.com/some-key: some-value
|
||||
|
||||
@@ -1,7 +1,4 @@
|
||||
# install chart with default values
|
||||
proxy:
|
||||
type: NodePort
|
||||
|
||||
env:
|
||||
anonymous_reports: "off"
|
||||
ingressController:
|
||||
|
||||
@@ -0,0 +1,15 @@
|
||||
# CI test for empty hostname including tls secret using string
|
||||
proxy:
|
||||
ingress:
|
||||
enabled: true
|
||||
tls: "kong.proxy.example.secret"
|
||||
|
||||
extraObjects:
|
||||
- apiVersion: v1
|
||||
data:
|
||||
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURoakNDQW00Q0NRQ0tyTDdSS1Y0NTBEQU5CZ2txaGtpRzl3MEJBUXNGQURDQmhERUxNQWtHQTFVRUJoTUMKV0ZneEVqQVFCZ05WQkFnTUNWTjBZWFJsVG1GdFpURVJNQThHQTFVRUJ3d0lRMmwwZVU1aGJXVXhGREFTQmdOVgpCQW9NQzBOdmJYQmhibmxPWVcxbE1Sc3dHUVlEVlFRTERCSkRiMjF3WVc1NVUyVmpkR2x2Yms1aGJXVXhHekFaCkJnTlZCQU1NRW5CeWIzaDVMbXR2Ym1jdVpYaGhiWEJzWlRBZUZ3MHlNekEyTWprd09ERTBNekJhRncwek16QTIKTWpZd09ERTBNekJhTUlHRU1Rc3dDUVlEVlFRR0V3SllXREVTTUJBR0ExVUVDQXdKVTNSaGRHVk9ZVzFsTVJFdwpEd1lEVlFRSERBaERhWFI1VG1GdFpURVVNQklHQTFVRUNnd0xRMjl0Y0dGdWVVNWhiV1V4R3pBWkJnTlZCQXNNCkVrTnZiWEJoYm5sVFpXTjBhVzl1VG1GdFpURWJNQmtHQTFVRUF3d1NjSEp2ZUhrdWEyOXVaeTVsZUdGdGNHeGwKTUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUE4Wmd4czI1RXdtaXRsRG1HMitWVwpscUZ4R3lkVHU2dWlCVldFZjNoV0h2R3YvUWpYZHBBWXlkc3ZpNS92b1FtcjNUeVJBb3VaR1lCR3RuVEF0cU5rCnFLUmFVaWppVlN3TTNzeUl1cHluMlRjSjk1N2RLUCtUYTRaL0VNUlRwSCtya1psV01LNVYrNUszTmFIL21leDUKVWRRWkl4WUxNM0xIM0t0cmt2OWZRNlhSZ2dkeXo0MEt2YUV6SW1scEVoQnBoS0g5UWJiL3RFRE0vdFFqbC9FUApmbUF5M2Y5WE1uRDNSeFY3TnFrZktpUjNXZ1JDMnFyNWtPbXlJTGp1YWxERk1Zb3lDZUlmSnd1WmVDaEpGb3ZHClFKUFY2WU9xTG5aRWN3MU9BaVBXQnMycXVmWmlsNXplekRDZUFGZDV3eXVrS1dPZ3pTZ3Q2VzZvN2FBRTBDK3YKclFJREFRQUJNQTBHQ1NxR1NJYjNEUUVCQ3dVQUE0SUJBUUNGZHhFOFVsMVorcWxBbW1lTk5BdlAyZVVxSElTbQpHWXZidzdGdW82bXNJY3V3cjZKeENBWjIwako5UkphalMzWS9TS3BteXM2OXZxU21ic25oeUJzc01mL1ZtenFSClBVLzVkUUZiblNybUJqMnFBNWxtRCtENDVLUEtrTjc1V21NeDRQWkZseEw3WHVLYnZhYVZBUjFFUmRNZy90NisKUXpPV3BVWVZrcFJnQmlxTDBTTjhvTStOTjdScGFESFNkZjlTY1FtUmhNVklNNDdVZ1ZXNWhta21mQjBkUTFhQQo5NWdTQ3E0cGVwUFRzY3NsbVBzM0lOck5BTk45KytyMnM1bXRTWnp5VktRU0cwRjQ0Y1puWjdTdkdTVFJORDlUCnRKVzNTcko3elBwS0JqWi9qVDRRVnpBdGtHN3FSV2ZhYnlWTmVrK29wMTgwSVY5Um9IR1JDU0kyCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
|
||||
tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUV2Z0lCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQktnd2dnU2tBZ0VBQW9JQkFRRHhtREd6YmtUQ2FLMlUKT1liYjVWYVdvWEViSjFPN3E2SUZWWVIvZUZZZThhLzlDTmQya0JqSjJ5K0xuKytoQ2F2ZFBKRUNpNWtaZ0VhMgpkTUMybzJTb3BGcFNLT0pWTEF6ZXpJaTZuS2ZaTnduM250MG8vNU5yaG44UXhGT2tmNnVSbVZZd3JsWDdrcmMxCm9mK1o3SGxSMUJrakZnc3pjc2ZjcTJ1Uy8xOURwZEdDQjNMUGpRcTlvVE1pYVdrU0VHbUVvZjFCdHYrMFFNeisKMUNPWDhROStZRExkLzFjeWNQZEhGWHMycVI4cUpIZGFCRUxhcXZtUTZiSWd1TzVxVU1VeGlqSUo0aDhuQzVsNApLRWtXaThaQWs5WHBnNm91ZGtSekRVNENJOVlHemFxNTltS1huTjdNTUo0QVYzbkRLNlFwWTZETktDM3BicWp0Cm9BVFFMNit0QWdNQkFBRUNnZ0VCQUs3N1I0d3BJcDRZU1JoaGJoN1loWldHQ3JEYkZCZUtZVWd4djB5LzhNaHEKenNlYlhzdGQ1TVpXL2FISVRqdzZFQU9tT1hVNWZNTHVtTWpQMlVDdktWbkg2QzgzczI1ekFFTmlxdWxXUzIvVgpJRi83N1Qwamx6ZTY2MDlPa3pKQzBoWWJsRVNnRUdDc3pBdUpjT0tnVnVLQWwxQkZTQW1VYWRPWFNNdm9NS3lDCkJlekZaVEhOcGRWQ2xwUHVLNGQrWFJJZ1hHWS84RzNmWlFXRWNjV2tTYmRjQUlLdVYvWktHQ0IyT2dXS1VzSHgKTStscEw1TTZ3aXdYOEFNdUVWVHJsMWNwKzAzTjdOaUYwMFpYdCszZzVZUkJmRitYWjZ1b3hmbENQZ3VHdzh6bgpvN2tFRVNKZ2YycHZyZWYveHBjSVFSM090aHZjSzR5RldOcndPbExHQk9FQ2dZRUErNmJBREF0bDAvRlpzV08zCnVvNlBRNXZTL0tqbS9XaUkzeUo5TUdLNzQxTFZpMlRMUGpVZ092SDdkZUVjNVJjUmoxV1Nna3d1bUdzZWE2WkQKWXRWSTRZTDdMM1NUQ3JyZUNFTDRhOUJPcFB0azcxWWw3TmhxZktEaXhzU1FnNmt4dDJ1TlYvZXNSQ1JPeENoWgp5bk9JTmkvN3lOeFpVek4zcndyVjBCMUFNYVVDZ1lFQTljVDBZNkJWRHZLdFFaV1gvR1REZ2pUUzN6QWlPWmFNCjVFM3NleHh6MXY4eDF0N3JvWDV3aHNaVjlzQ05nNlJaNjIyT3hJejhHQnVvMnU1M2h2WFJabmdDaG1PcHYwRjgKcm5STWFNR0tIeGN2TmNrVUZUMW9TdDJCeEhNT1FNZTM2cERVTnZ0S3pvNGJoakpVUU94Mm14RU9TNERscm4rMApRU3FqVFpyWGwya0NnWUJ1UmIyMkNYQ1BsUjBHbkhtd0tEUWpIaTh3UkJza1JDQm1Gc2pnNFFNUU5BWWJWUW15CnNyankyNEtqUHdmWVkybHdjOEVGazdoL1ZjRTR6dHlNZklXNVBCb3h5MVY3eURMdlQ5bG45Um5oTmNBZkdKTDUKM0VPZFpTcTZpdndBbGEyUmdIR3BjSUJ1UTdLNFJpNUNocW5UaE9kQ056eDFOd0psRTh4cHE4ZXJlUUtCZ1FEeQppV3B3UXRLT0ROa0VCdi9WT1E5am1JT2RjOS9pbXZyeGR5RHZvWFdENzVXY3FhTTVYUkRwUUNPbmZnQnBzREI0CjBFWjdHM0xReThNSVF4czcyYXpMaFpWZ1VFdzlEUUJoSFM0bWx4Q2FmQU8vL1c3UFF5bC84RGJXeW9CL1YxamQKcUExMU1PcHpDdlNJcTNSUUdjczJYaytRSFdVTW5zUWhKMVcvQ1JiSE9RS0JnRTVQZ0hrbW1PY1VXZkJBZUtzTApvb2FNNzBINVN1YUNYN1Y1enBhM3hFMW5WVWMxend5aldOdkdWbTA5WkpEOFFMR1ZDV2U0R1o5R1NvV2tqSUMvCklFKzA0M29kUERuL2JwSDlTMDF2a0s1ZDRJSGc3QUcwWXI5SW1zS0paT0djT1dmdUdKSlZ5em1CRXhaSU9pbnoKVFFuaFdhZWs0NE1hdVJYOC9pRjZyZWorCi0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0K
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: kong.proxy.example.secret
|
||||
type: kubernetes.io/tls
|
||||
@@ -0,0 +1,16 @@
|
||||
# CI test for hostname including tls secret using string
|
||||
proxy:
|
||||
ingress:
|
||||
enabled: true
|
||||
hostname: "proxy.kong.example"
|
||||
tls: "kong.proxy.example.secret"
|
||||
|
||||
extraObjects:
|
||||
- apiVersion: v1
|
||||
data:
|
||||
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURoakNDQW00Q0NRQ0tyTDdSS1Y0NTBEQU5CZ2txaGtpRzl3MEJBUXNGQURDQmhERUxNQWtHQTFVRUJoTUMKV0ZneEVqQVFCZ05WQkFnTUNWTjBZWFJsVG1GdFpURVJNQThHQTFVRUJ3d0lRMmwwZVU1aGJXVXhGREFTQmdOVgpCQW9NQzBOdmJYQmhibmxPWVcxbE1Sc3dHUVlEVlFRTERCSkRiMjF3WVc1NVUyVmpkR2x2Yms1aGJXVXhHekFaCkJnTlZCQU1NRW5CeWIzaDVMbXR2Ym1jdVpYaGhiWEJzWlRBZUZ3MHlNekEyTWprd09ERTBNekJhRncwek16QTIKTWpZd09ERTBNekJhTUlHRU1Rc3dDUVlEVlFRR0V3SllXREVTTUJBR0ExVUVDQXdKVTNSaGRHVk9ZVzFsTVJFdwpEd1lEVlFRSERBaERhWFI1VG1GdFpURVVNQklHQTFVRUNnd0xRMjl0Y0dGdWVVNWhiV1V4R3pBWkJnTlZCQXNNCkVrTnZiWEJoYm5sVFpXTjBhVzl1VG1GdFpURWJNQmtHQTFVRUF3d1NjSEp2ZUhrdWEyOXVaeTVsZUdGdGNHeGwKTUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUE4Wmd4czI1RXdtaXRsRG1HMitWVwpscUZ4R3lkVHU2dWlCVldFZjNoV0h2R3YvUWpYZHBBWXlkc3ZpNS92b1FtcjNUeVJBb3VaR1lCR3RuVEF0cU5rCnFLUmFVaWppVlN3TTNzeUl1cHluMlRjSjk1N2RLUCtUYTRaL0VNUlRwSCtya1psV01LNVYrNUszTmFIL21leDUKVWRRWkl4WUxNM0xIM0t0cmt2OWZRNlhSZ2dkeXo0MEt2YUV6SW1scEVoQnBoS0g5UWJiL3RFRE0vdFFqbC9FUApmbUF5M2Y5WE1uRDNSeFY3TnFrZktpUjNXZ1JDMnFyNWtPbXlJTGp1YWxERk1Zb3lDZUlmSnd1WmVDaEpGb3ZHClFKUFY2WU9xTG5aRWN3MU9BaVBXQnMycXVmWmlsNXplekRDZUFGZDV3eXVrS1dPZ3pTZ3Q2VzZvN2FBRTBDK3YKclFJREFRQUJNQTBHQ1NxR1NJYjNEUUVCQ3dVQUE0SUJBUUNGZHhFOFVsMVorcWxBbW1lTk5BdlAyZVVxSElTbQpHWXZidzdGdW82bXNJY3V3cjZKeENBWjIwako5UkphalMzWS9TS3BteXM2OXZxU21ic25oeUJzc01mL1ZtenFSClBVLzVkUUZiblNybUJqMnFBNWxtRCtENDVLUEtrTjc1V21NeDRQWkZseEw3WHVLYnZhYVZBUjFFUmRNZy90NisKUXpPV3BVWVZrcFJnQmlxTDBTTjhvTStOTjdScGFESFNkZjlTY1FtUmhNVklNNDdVZ1ZXNWhta21mQjBkUTFhQQo5NWdTQ3E0cGVwUFRzY3NsbVBzM0lOck5BTk45KytyMnM1bXRTWnp5VktRU0cwRjQ0Y1puWjdTdkdTVFJORDlUCnRKVzNTcko3elBwS0JqWi9qVDRRVnpBdGtHN3FSV2ZhYnlWTmVrK29wMTgwSVY5Um9IR1JDU0kyCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
|
||||
tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUV2Z0lCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQktnd2dnU2tBZ0VBQW9JQkFRRHhtREd6YmtUQ2FLMlUKT1liYjVWYVdvWEViSjFPN3E2SUZWWVIvZUZZZThhLzlDTmQya0JqSjJ5K0xuKytoQ2F2ZFBKRUNpNWtaZ0VhMgpkTUMybzJTb3BGcFNLT0pWTEF6ZXpJaTZuS2ZaTnduM250MG8vNU5yaG44UXhGT2tmNnVSbVZZd3JsWDdrcmMxCm9mK1o3SGxSMUJrakZnc3pjc2ZjcTJ1Uy8xOURwZEdDQjNMUGpRcTlvVE1pYVdrU0VHbUVvZjFCdHYrMFFNeisKMUNPWDhROStZRExkLzFjeWNQZEhGWHMycVI4cUpIZGFCRUxhcXZtUTZiSWd1TzVxVU1VeGlqSUo0aDhuQzVsNApLRWtXaThaQWs5WHBnNm91ZGtSekRVNENJOVlHemFxNTltS1huTjdNTUo0QVYzbkRLNlFwWTZETktDM3BicWp0Cm9BVFFMNit0QWdNQkFBRUNnZ0VCQUs3N1I0d3BJcDRZU1JoaGJoN1loWldHQ3JEYkZCZUtZVWd4djB5LzhNaHEKenNlYlhzdGQ1TVpXL2FISVRqdzZFQU9tT1hVNWZNTHVtTWpQMlVDdktWbkg2QzgzczI1ekFFTmlxdWxXUzIvVgpJRi83N1Qwamx6ZTY2MDlPa3pKQzBoWWJsRVNnRUdDc3pBdUpjT0tnVnVLQWwxQkZTQW1VYWRPWFNNdm9NS3lDCkJlekZaVEhOcGRWQ2xwUHVLNGQrWFJJZ1hHWS84RzNmWlFXRWNjV2tTYmRjQUlLdVYvWktHQ0IyT2dXS1VzSHgKTStscEw1TTZ3aXdYOEFNdUVWVHJsMWNwKzAzTjdOaUYwMFpYdCszZzVZUkJmRitYWjZ1b3hmbENQZ3VHdzh6bgpvN2tFRVNKZ2YycHZyZWYveHBjSVFSM090aHZjSzR5RldOcndPbExHQk9FQ2dZRUErNmJBREF0bDAvRlpzV08zCnVvNlBRNXZTL0tqbS9XaUkzeUo5TUdLNzQxTFZpMlRMUGpVZ092SDdkZUVjNVJjUmoxV1Nna3d1bUdzZWE2WkQKWXRWSTRZTDdMM1NUQ3JyZUNFTDRhOUJPcFB0azcxWWw3TmhxZktEaXhzU1FnNmt4dDJ1TlYvZXNSQ1JPeENoWgp5bk9JTmkvN3lOeFpVek4zcndyVjBCMUFNYVVDZ1lFQTljVDBZNkJWRHZLdFFaV1gvR1REZ2pUUzN6QWlPWmFNCjVFM3NleHh6MXY4eDF0N3JvWDV3aHNaVjlzQ05nNlJaNjIyT3hJejhHQnVvMnU1M2h2WFJabmdDaG1PcHYwRjgKcm5STWFNR0tIeGN2TmNrVUZUMW9TdDJCeEhNT1FNZTM2cERVTnZ0S3pvNGJoakpVUU94Mm14RU9TNERscm4rMApRU3FqVFpyWGwya0NnWUJ1UmIyMkNYQ1BsUjBHbkhtd0tEUWpIaTh3UkJza1JDQm1Gc2pnNFFNUU5BWWJWUW15CnNyankyNEtqUHdmWVkybHdjOEVGazdoL1ZjRTR6dHlNZklXNVBCb3h5MVY3eURMdlQ5bG45Um5oTmNBZkdKTDUKM0VPZFpTcTZpdndBbGEyUmdIR3BjSUJ1UTdLNFJpNUNocW5UaE9kQ056eDFOd0psRTh4cHE4ZXJlUUtCZ1FEeQppV3B3UXRLT0ROa0VCdi9WT1E5am1JT2RjOS9pbXZyeGR5RHZvWFdENzVXY3FhTTVYUkRwUUNPbmZnQnBzREI0CjBFWjdHM0xReThNSVF4czcyYXpMaFpWZ1VFdzlEUUJoSFM0bWx4Q2FmQU8vL1c3UFF5bC84RGJXeW9CL1YxamQKcUExMU1PcHpDdlNJcTNSUUdjczJYaytRSFdVTW5zUWhKMVcvQ1JiSE9RS0JnRTVQZ0hrbW1PY1VXZkJBZUtzTApvb2FNNzBINVN1YUNYN1Y1enBhM3hFMW5WVWMxend5aldOdkdWbTA5WkpEOFFMR1ZDV2U0R1o5R1NvV2tqSUMvCklFKzA0M29kUERuL2JwSDlTMDF2a0s1ZDRJSGc3QUcwWXI5SW1zS0paT0djT1dmdUdKSlZ5em1CRXhaSU9pbnoKVFFuaFdhZWs0NE1hdVJYOC9pRjZyZWorCi0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0K
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: kong.proxy.example.secret
|
||||
type: kubernetes.io/tls
|
||||
@@ -0,0 +1,9 @@
|
||||
# CI test for using ingress hosts configuration
|
||||
proxy:
|
||||
ingress:
|
||||
enabled: true
|
||||
hosts:
|
||||
- host: proxy.kong.example
|
||||
paths:
|
||||
- path: /
|
||||
pathType: ImplementationSpecific
|
||||
@@ -0,0 +1,42 @@
|
||||
# CI test for testing combined ingress hostname and hosts configuration including tls configuraion using slice
|
||||
proxy:
|
||||
ingress:
|
||||
enabled: true
|
||||
hostname: "proxy.kong.example"
|
||||
hosts:
|
||||
- host: "proxy2.kong.example"
|
||||
paths:
|
||||
- path: /foo
|
||||
pathType: Prefix
|
||||
- path: /bar
|
||||
pathType: Prefix
|
||||
- host: "proxy3.kong.example"
|
||||
paths:
|
||||
- path: /baz
|
||||
pathType: Prefix
|
||||
tls:
|
||||
- hosts:
|
||||
- "proxy.kong.example"
|
||||
secretName: "proxy.kong.example.secret"
|
||||
- hosts:
|
||||
- "proxy2.kong.example"
|
||||
- "proxy3.kong.example"
|
||||
secretName: "proxy.kong.example.secret2"
|
||||
|
||||
extraObjects:
|
||||
- apiVersion: v1
|
||||
data:
|
||||
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURoakNDQW00Q0NRQ0tyTDdSS1Y0NTBEQU5CZ2txaGtpRzl3MEJBUXNGQURDQmhERUxNQWtHQTFVRUJoTUMKV0ZneEVqQVFCZ05WQkFnTUNWTjBZWFJsVG1GdFpURVJNQThHQTFVRUJ3d0lRMmwwZVU1aGJXVXhGREFTQmdOVgpCQW9NQzBOdmJYQmhibmxPWVcxbE1Sc3dHUVlEVlFRTERCSkRiMjF3WVc1NVUyVmpkR2x2Yms1aGJXVXhHekFaCkJnTlZCQU1NRW5CeWIzaDVMbXR2Ym1jdVpYaGhiWEJzWlRBZUZ3MHlNekEyTWprd09ERTBNekJhRncwek16QTIKTWpZd09ERTBNekJhTUlHRU1Rc3dDUVlEVlFRR0V3SllXREVTTUJBR0ExVUVDQXdKVTNSaGRHVk9ZVzFsTVJFdwpEd1lEVlFRSERBaERhWFI1VG1GdFpURVVNQklHQTFVRUNnd0xRMjl0Y0dGdWVVNWhiV1V4R3pBWkJnTlZCQXNNCkVrTnZiWEJoYm5sVFpXTjBhVzl1VG1GdFpURWJNQmtHQTFVRUF3d1NjSEp2ZUhrdWEyOXVaeTVsZUdGdGNHeGwKTUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUE4Wmd4czI1RXdtaXRsRG1HMitWVwpscUZ4R3lkVHU2dWlCVldFZjNoV0h2R3YvUWpYZHBBWXlkc3ZpNS92b1FtcjNUeVJBb3VaR1lCR3RuVEF0cU5rCnFLUmFVaWppVlN3TTNzeUl1cHluMlRjSjk1N2RLUCtUYTRaL0VNUlRwSCtya1psV01LNVYrNUszTmFIL21leDUKVWRRWkl4WUxNM0xIM0t0cmt2OWZRNlhSZ2dkeXo0MEt2YUV6SW1scEVoQnBoS0g5UWJiL3RFRE0vdFFqbC9FUApmbUF5M2Y5WE1uRDNSeFY3TnFrZktpUjNXZ1JDMnFyNWtPbXlJTGp1YWxERk1Zb3lDZUlmSnd1WmVDaEpGb3ZHClFKUFY2WU9xTG5aRWN3MU9BaVBXQnMycXVmWmlsNXplekRDZUFGZDV3eXVrS1dPZ3pTZ3Q2VzZvN2FBRTBDK3YKclFJREFRQUJNQTBHQ1NxR1NJYjNEUUVCQ3dVQUE0SUJBUUNGZHhFOFVsMVorcWxBbW1lTk5BdlAyZVVxSElTbQpHWXZidzdGdW82bXNJY3V3cjZKeENBWjIwako5UkphalMzWS9TS3BteXM2OXZxU21ic25oeUJzc01mL1ZtenFSClBVLzVkUUZiblNybUJqMnFBNWxtRCtENDVLUEtrTjc1V21NeDRQWkZseEw3WHVLYnZhYVZBUjFFUmRNZy90NisKUXpPV3BVWVZrcFJnQmlxTDBTTjhvTStOTjdScGFESFNkZjlTY1FtUmhNVklNNDdVZ1ZXNWhta21mQjBkUTFhQQo5NWdTQ3E0cGVwUFRzY3NsbVBzM0lOck5BTk45KytyMnM1bXRTWnp5VktRU0cwRjQ0Y1puWjdTdkdTVFJORDlUCnRKVzNTcko3elBwS0JqWi9qVDRRVnpBdGtHN3FSV2ZhYnlWTmVrK29wMTgwSVY5Um9IR1JDU0kyCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
|
||||
tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUV2Z0lCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQktnd2dnU2tBZ0VBQW9JQkFRRHhtREd6YmtUQ2FLMlUKT1liYjVWYVdvWEViSjFPN3E2SUZWWVIvZUZZZThhLzlDTmQya0JqSjJ5K0xuKytoQ2F2ZFBKRUNpNWtaZ0VhMgpkTUMybzJTb3BGcFNLT0pWTEF6ZXpJaTZuS2ZaTnduM250MG8vNU5yaG44UXhGT2tmNnVSbVZZd3JsWDdrcmMxCm9mK1o3SGxSMUJrakZnc3pjc2ZjcTJ1Uy8xOURwZEdDQjNMUGpRcTlvVE1pYVdrU0VHbUVvZjFCdHYrMFFNeisKMUNPWDhROStZRExkLzFjeWNQZEhGWHMycVI4cUpIZGFCRUxhcXZtUTZiSWd1TzVxVU1VeGlqSUo0aDhuQzVsNApLRWtXaThaQWs5WHBnNm91ZGtSekRVNENJOVlHemFxNTltS1huTjdNTUo0QVYzbkRLNlFwWTZETktDM3BicWp0Cm9BVFFMNit0QWdNQkFBRUNnZ0VCQUs3N1I0d3BJcDRZU1JoaGJoN1loWldHQ3JEYkZCZUtZVWd4djB5LzhNaHEKenNlYlhzdGQ1TVpXL2FISVRqdzZFQU9tT1hVNWZNTHVtTWpQMlVDdktWbkg2QzgzczI1ekFFTmlxdWxXUzIvVgpJRi83N1Qwamx6ZTY2MDlPa3pKQzBoWWJsRVNnRUdDc3pBdUpjT0tnVnVLQWwxQkZTQW1VYWRPWFNNdm9NS3lDCkJlekZaVEhOcGRWQ2xwUHVLNGQrWFJJZ1hHWS84RzNmWlFXRWNjV2tTYmRjQUlLdVYvWktHQ0IyT2dXS1VzSHgKTStscEw1TTZ3aXdYOEFNdUVWVHJsMWNwKzAzTjdOaUYwMFpYdCszZzVZUkJmRitYWjZ1b3hmbENQZ3VHdzh6bgpvN2tFRVNKZ2YycHZyZWYveHBjSVFSM090aHZjSzR5RldOcndPbExHQk9FQ2dZRUErNmJBREF0bDAvRlpzV08zCnVvNlBRNXZTL0tqbS9XaUkzeUo5TUdLNzQxTFZpMlRMUGpVZ092SDdkZUVjNVJjUmoxV1Nna3d1bUdzZWE2WkQKWXRWSTRZTDdMM1NUQ3JyZUNFTDRhOUJPcFB0azcxWWw3TmhxZktEaXhzU1FnNmt4dDJ1TlYvZXNSQ1JPeENoWgp5bk9JTmkvN3lOeFpVek4zcndyVjBCMUFNYVVDZ1lFQTljVDBZNkJWRHZLdFFaV1gvR1REZ2pUUzN6QWlPWmFNCjVFM3NleHh6MXY4eDF0N3JvWDV3aHNaVjlzQ05nNlJaNjIyT3hJejhHQnVvMnU1M2h2WFJabmdDaG1PcHYwRjgKcm5STWFNR0tIeGN2TmNrVUZUMW9TdDJCeEhNT1FNZTM2cERVTnZ0S3pvNGJoakpVUU94Mm14RU9TNERscm4rMApRU3FqVFpyWGwya0NnWUJ1UmIyMkNYQ1BsUjBHbkhtd0tEUWpIaTh3UkJza1JDQm1Gc2pnNFFNUU5BWWJWUW15CnNyankyNEtqUHdmWVkybHdjOEVGazdoL1ZjRTR6dHlNZklXNVBCb3h5MVY3eURMdlQ5bG45Um5oTmNBZkdKTDUKM0VPZFpTcTZpdndBbGEyUmdIR3BjSUJ1UTdLNFJpNUNocW5UaE9kQ056eDFOd0psRTh4cHE4ZXJlUUtCZ1FEeQppV3B3UXRLT0ROa0VCdi9WT1E5am1JT2RjOS9pbXZyeGR5RHZvWFdENzVXY3FhTTVYUkRwUUNPbmZnQnBzREI0CjBFWjdHM0xReThNSVF4czcyYXpMaFpWZ1VFdzlEUUJoSFM0bWx4Q2FmQU8vL1c3UFF5bC84RGJXeW9CL1YxamQKcUExMU1PcHpDdlNJcTNSUUdjczJYaytRSFdVTW5zUWhKMVcvQ1JiSE9RS0JnRTVQZ0hrbW1PY1VXZkJBZUtzTApvb2FNNzBINVN1YUNYN1Y1enBhM3hFMW5WVWMxend5aldOdkdWbTA5WkpEOFFMR1ZDV2U0R1o5R1NvV2tqSUMvCklFKzA0M29kUERuL2JwSDlTMDF2a0s1ZDRJSGc3QUcwWXI5SW1zS0paT0djT1dmdUdKSlZ5em1CRXhaSU9pbnoKVFFuaFdhZWs0NE1hdVJYOC9pRjZyZWorCi0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0K
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: kong.proxy.example.secret
|
||||
type: kubernetes.io/tls
|
||||
- apiVersion: v1
|
||||
data:
|
||||
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURmakNDQW1ZQ0NRREVtWjF0cnJwaURqQU5CZ2txaGtpRzl3MEJBUXNGQURDQmdERUxNQWtHQTFVRUJoTUMKV0ZneEVqQVFCZ05WQkFnTUNWTjBZWFJsVG1GdFpURVJNQThHQTFVRUJ3d0lRMmwwZVU1aGJXVXhGREFTQmdOVgpCQW9NQzBOdmJYQmhibmxPWVcxbE1Sc3dHUVlEVlFRTERCSkRiMjF3WVc1NVUyVmpkR2x2Yms1aGJXVXhGekFWCkJnTlZCQU1NRGlvdWEyOXVaeTVsZUdGdGNHeGxNQjRYRFRJek1EWXlPVEE0TVRjek4xb1hEVE16TURZeU5qQTQKTVRjek4xb3dnWUF4Q3pBSkJnTlZCQVlUQWxoWU1SSXdFQVlEVlFRSURBbFRkR0YwWlU1aGJXVXhFVEFQQmdOVgpCQWNNQ0VOcGRIbE9ZVzFsTVJRd0VnWURWUVFLREF0RGIyMXdZVzU1VG1GdFpURWJNQmtHQTFVRUN3d1NRMjl0CmNHRnVlVk5sWTNScGIyNU9ZVzFsTVJjd0ZRWURWUVFEREE0cUxtdHZibWN1WlhoaGJYQnNaVENDQVNJd0RRWUoKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTDlSR1g1VytsRW8wcGg2eTJqeHN6TGZOcjMvNlpFOQpPR0pPMGl1WmpwRml2dHBya24ydDlqYTRaNUdYOGh4NUczS1FsRkhrVFBmV01BWmUzdldINTF0alZzYjZwY2UwCjlkMUo4WXNxWkh5RHVlUzBrS3RUbEFmc0F5MnVjL3ZvUUdmOTdZeUI2TlJ4TEJmNHBnSVJ4eHpGM3o0Q1ZOSTgKTzE5Ym1PYVo1Vkk1QWZpbENSMUI1ekxuN2VoeEJHOHhTQmRtQUg0eWFob2t5RXk2a0ZtRzJCaEtJWjdsL1BZYQpqbU1yQ3cwekRVampvblBublZTWTkxL0EwNUJVTVk5OEZsME00QVV5T1V3enBaajhqMXhLMTNqUVlGeXJwUHQwCklHNUdLR044akVCcnRkdGVlcGZIdFZuekFWYnhoT0hkcXZoUWhrSDJDSGVwOStIQkNIL25VL1VDQXdFQUFUQU4KQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBQkcxVVYyUFRJekhrNEt4cjBHT0NXalhjTTdKUU9hbUJQM3dZSCswRgpyc09YUG9IOHVLV25XYjhSSGE1MDhMenU4MGNzS1lYcnZ4SEhDcmcxdXJjRnl3bnNMaUtMNGhsQklTd2ZMNzFFClVXODhQdGYyWTdjTnJZRzNLc2MvMWVpait1RWd5bVdCbjkraVYzbzE5VERwRjlZZWZwYzNUUDJqMGhNUHcwMlgKa1gzSlh3b250NnBQaDhlQjhXRU1OZkF5NzZmb0lMcytVd0Fjck56QkpjSVZSTERoZWFNMFNFd0xCNUpuaWZ5ZwplRE1aSE56MkhLais0NU1wTzFOSDBtd3ZJRTRLQjNITUNSSlMybmZFbWVMcFdCMWpmZTV6T2o1bWhTeS82M0RVCldDQll1aUhtelFWaGxJS21lQzBlVmd3bGtkMTFrUDRNM1hoWnB6V09aQ1BoaGc9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
|
||||
tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUV2UUlCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQktjd2dnU2pBZ0VBQW9JQkFRQy9VUmwrVnZwUktOS1kKZXN0bzhiTXkzemE5LyttUlBUaGlUdElybVk2UllyN2FhNUo5cmZZMnVHZVJsL0ljZVJ0eWtKUlI1RXozMWpBRwpYdDcxaCtkYlkxYkcrcVhIdFBYZFNmR0xLbVI4Zzdua3RKQ3JVNVFIN0FNdHJuUDc2RUJuL2UyTWdlalVjU3dYCitLWUNFY2NjeGQ4K0FsVFNQRHRmVzVqbW1lVlNPUUg0cFFrZFFlY3k1KzNvY1FSdk1VZ1haZ0IrTW1vYUpNaE0KdXBCWmh0Z1lTaUdlNWZ6MkdvNWpLd3NOTXcxSTQ2Sno1NTFVbVBkZndOT1FWREdQZkJaZERPQUZNamxNTTZXWQovSTljU3RkNDBHQmNxNlQ3ZENCdVJpaGpmSXhBYTdYYlhucVh4N1ZaOHdGVzhZVGgzYXI0VUlaQjlnaDNxZmZoCndRaC81MVAxQWdNQkFBRUNnZ0VCQUlCZ0l3TXJ5ZnY3c0pTd2tSMXlVaFNvdzByckZnZG5WUlppWFpUMERUNXgKVEMrMFR6QVdNMGkwcElxRnN1aDRPM3E4bVVuNkw4dDk1ZXZnYlN2RWJmSmN6alhtcXFjL1BsdW02blcvbEg0WQp4Znc1VFhvcE13Tzkwc1FzYzVkdFdRcHUwWitlN0dUaEsvMUowOXMvb3FRa0FwRFJiNmxDMFhSRE9tNUNoaWFNCi95Z2M2dGUzUHkrRXpzSmRMRm9YWndFQnVQWTB2KzlBclhpNmlUMllaN1ZacE9iZzQxcm1ocHNObTFLNmdJajUKZFZKNGZYa2Z5V0hsSmJBYzVTRDkrVWMrTGFjUEcxSjVJUWx6eTM0WlM0ZG9VQ2lmODZuVHFzSnFVTU1sNXYxcAp3SFFUZFI2MkdnWnRPM1grOU4vdHE3SExqU0tHY0JEd3E4bEM4QXZ0VHdFQ2dZRUErWWpVdzI1em42aWhjaXFpCmo3dDJiQVdLdzdlbng1RXFzU25ZOG1PYzR2TDdNa1YyN2ZhYXp1cW8wUEtOeWJOa1grUlhIMDN4S0NDd0x0N0UKLzRDUlFHMGNkQmhBQ2szMkpadllrQmxESUZ3VmtnMHVnNGk4Snp6VjVCT2hEeWdwZUhJTDVVTkx2eGJDbVh6MAo1bXNYRktPYW1HYkFCbE9KTEZsR1R4WWdzeWtDZ1lFQXhFWWI0dFVmRmhiTmpJTUMyd1hFRXdWZkJYOFJqNzVqCjN6SkwxV3o4YWxUQmxFemZYOTZiNmg3VjFNT1NHcmlabFJ1cGpEaUFsUkhPZytDSXlPbmdISFkwd2xTaHNmemQKSDluL2dOdUZsanFuQkF3OVpaSW9hbE1zUVVER3RLSnVIejhEYzlVNzRFMGM3WldQWk1Ub0pNdFV2Zkl5T0pZSgpQODh1YnYvam4rMENnWUJaNmpzNFhKRmZRNFZCUFNtc2Z4RXg1V0ZXR3RSakxlVGpSNy83djNjbHRBWmQyL2Y1CjBUV0JQNzhxNDJ2QjlWbEMwR1d3U3dhTnZoR2VJZmw4VTVpRFRZM0dLNExQODcyeFdaSFVnclhVY0RuNWtiUmsKQXg1QlNVT05WcUZmYzhwVnMwcWtCdmJCV1hNdm1YNHBsUWNSRWM3QUFhNUoyVW9CWi8zVXU1VjIyUUtCZ0ZnVQpKanQ2N0lKYkpVN2pGQXI1NFcydndWNlVFV3R5UXh0TVZOK29FdlljcHVwSVBRMm10azB3SFVGbnFrODNmQ1IvCnoyeFBodFJlczFCWEdNc2d1U1BNb0F4OU1qclBnT1BrVGxhakxLV29HSDhtaHY3bndoOUV4OTFZbGxORmVTbW8KZTRJbHRNTUpsK3UrYkNVS2dDclMzR3FKSDZScElDbDBiaC85MFVaWkFvR0FaUEsrdldLQ0N6aHNhSnVWak1VSQpiTEJlMi9CM0xxTVBhakFLTjVTNU9GYlpBZm5NeE9BT1lnd25iWmdpZGVkcVk2QkIyLytVVGt4MW1IUjhKcmpGCnRyN20wS2VvRFY4dmQxSENvSkF3b2hqQ1B6SkJhSW9WYWNkRFNsMDNIOVFEck4yd0RFYUxoWFBlVkRoNGZ2NmQKa3d6V3FZWUlETzRKQlp5L21Wa0t4NFU9Ci0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0K
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: kong.proxy.example.secret2
|
||||
type: kubernetes.io/tls
|
||||
@@ -2,9 +2,7 @@
|
||||
# use single image strings instead of repository/tag
|
||||
|
||||
image:
|
||||
unifiedRepoTag: kong:2.6
|
||||
proxy:
|
||||
type: NodePort
|
||||
unifiedRepoTag: kong:3.4
|
||||
|
||||
env:
|
||||
anonymous_reports: "off"
|
||||
@@ -12,4 +10,4 @@ ingressController:
|
||||
env:
|
||||
anonymous_reports: "false"
|
||||
image:
|
||||
unifiedRepoTag: kong/kubernetes-ingress-controller:2.0.2
|
||||
unifiedRepoTag: kong/kubernetes-ingress-controller:2.12
|
||||
@@ -0,0 +1,14 @@
|
||||
ingressController:
|
||||
enabled: false
|
||||
|
||||
image:
|
||||
repository: kong/kong-gateway
|
||||
tag: "3.4.0.0"
|
||||
|
||||
readinessProbe:
|
||||
httpGet:
|
||||
path: "/status"
|
||||
port: status
|
||||
scheme: HTTP
|
||||
initialDelaySeconds: 1
|
||||
periodSeconds: 1
|
||||
@@ -28,19 +28,14 @@ ingressController:
|
||||
podLabels:
|
||||
app: kong
|
||||
environment: test
|
||||
# - podSecurityPolicies are enabled
|
||||
podSecurityPolicy:
|
||||
enabled: true
|
||||
# - ingress resources are created with hosts
|
||||
admin:
|
||||
type: NodePort
|
||||
ingress:
|
||||
enabled: true
|
||||
hostname: admin.kong.example
|
||||
annotations: {}
|
||||
path: /
|
||||
proxy:
|
||||
type: NodePort
|
||||
ingress:
|
||||
enabled: true
|
||||
hostname: proxy.kong.example
|
||||
|
||||
@@ -3,8 +3,12 @@
|
||||
# - stream listens work
|
||||
# - a mixture of controller, Kong, and shared volumes successfully mount
|
||||
# - watchNamespaces is set
|
||||
# - the admission webhook is enabled; has the timeout explicitly set
|
||||
ingressController:
|
||||
enabled: true
|
||||
admissionWebhook:
|
||||
enabled: true
|
||||
timeoutSeconds: 5
|
||||
env:
|
||||
anonymous_reports: "false"
|
||||
customEnv:
|
||||
@@ -21,13 +25,11 @@ env:
|
||||
database: "postgres"
|
||||
# - ingress resources are created without hosts
|
||||
admin:
|
||||
type: NodePort
|
||||
ingress:
|
||||
enabled: true
|
||||
hosts: []
|
||||
path: /
|
||||
proxy:
|
||||
type: NodePort
|
||||
ingress:
|
||||
enabled: true
|
||||
hostname: proxy.kong.example
|
||||
|
||||
@@ -8,8 +8,6 @@ env:
|
||||
database: "off"
|
||||
postgresql:
|
||||
enabled: false
|
||||
proxy:
|
||||
type: NodePort
|
||||
deployment:
|
||||
initContainers:
|
||||
- name: "bash"
|
||||
|
||||
@@ -12,7 +12,6 @@ env:
|
||||
postgresql:
|
||||
enabled: false
|
||||
proxy:
|
||||
type: NodePort
|
||||
# - add stream listens
|
||||
stream:
|
||||
- containerPort: 9000
|
||||
|
||||
@@ -26,13 +26,11 @@ customEnv:
|
||||
client_id: "exampleId"
|
||||
# - ingress resources are created without hosts
|
||||
admin:
|
||||
type: NodePort
|
||||
ingress:
|
||||
enabled: true
|
||||
hosts: []
|
||||
path: /
|
||||
proxy:
|
||||
type: NodePort
|
||||
ingress:
|
||||
enabled: true
|
||||
hostname: proxy.kong.example
|
||||
|
||||
@@ -1,34 +0,0 @@
|
||||
# CI test for testing dbless deployment without ingress controllers
|
||||
# - disable ingress controller
|
||||
# - no static config
|
||||
ingressController:
|
||||
enabled: false
|
||||
# - disable DB for kong
|
||||
env:
|
||||
anonymous_reports: "off"
|
||||
database: "off"
|
||||
postgresql:
|
||||
enabled: false
|
||||
proxy:
|
||||
type: NodePort
|
||||
deployment:
|
||||
initContainers:
|
||||
- name: "bash"
|
||||
image: "bash:latest"
|
||||
command: ["/bin/sh", "-c", "true"]
|
||||
resources:
|
||||
limits:
|
||||
cpu: "100m"
|
||||
memory: "64Mi"
|
||||
requests:
|
||||
cpu: "100m"
|
||||
memory: "64Mi"
|
||||
volumeMounts:
|
||||
- name: "tmpdir"
|
||||
mountPath: "/opt/tmp"
|
||||
userDefinedVolumes:
|
||||
- name: "tmpdir"
|
||||
emptyDir: {}
|
||||
userDefinedVolumeMounts:
|
||||
- name: "tmpdir"
|
||||
mountPath: "/opt/tmp"
|
||||
@@ -1,10 +1,9 @@
|
||||
# generated using: kubectl kustomize github.com/kong/kubernetes-ingress-controller/config/crd?ref=v2.8.1
|
||||
# generated using: kubectl kustomize 'github.com/kong/kubernetes-ingress-controller/config/crd?ref=v2.12.0'
|
||||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
annotations:
|
||||
controller-gen.kubebuilder.io/version: v0.11.1
|
||||
creationTimestamp: null
|
||||
controller-gen.kubebuilder.io/version: v0.13.0
|
||||
name: ingressclassparameterses.configuration.konghq.com
|
||||
spec:
|
||||
group: configuration.konghq.com
|
||||
@@ -56,8 +55,7 @@ apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
annotations:
|
||||
controller-gen.kubebuilder.io/version: v0.11.1
|
||||
creationTimestamp: null
|
||||
controller-gen.kubebuilder.io/version: v0.13.0
|
||||
name: kongclusterplugins.configuration.konghq.com
|
||||
spec:
|
||||
group: configuration.konghq.com
|
||||
@@ -91,6 +89,9 @@ spec:
|
||||
name: Config
|
||||
priority: 1
|
||||
type: string
|
||||
- jsonPath: .status.conditions[?(@.type=="Programmed")].status
|
||||
name: Programmed
|
||||
type: string
|
||||
name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
@@ -142,6 +143,11 @@ spec:
|
||||
disabled:
|
||||
description: Disabled set if the plugin is disabled or not.
|
||||
type: boolean
|
||||
instance_name:
|
||||
description: InstanceName is an optional custom name to identify an instance
|
||||
of the plugin. This is useful when running the same plugin in multiple
|
||||
contexts, for example, on multiple services.
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
@@ -183,6 +189,8 @@ spec:
|
||||
description: Protocols configures plugin to run on requests received on
|
||||
specific protocols.
|
||||
items:
|
||||
description: KongProtocol is a valid Kong protocol. This alias is necessary
|
||||
to deal with https://github.com/kubernetes-sigs/controller-tools/issues/342
|
||||
enum:
|
||||
- http
|
||||
- https
|
||||
@@ -201,6 +209,91 @@ spec:
|
||||
- second
|
||||
- all
|
||||
type: string
|
||||
status:
|
||||
description: Status represents the current status of the KongClusterPlugin
|
||||
resource.
|
||||
properties:
|
||||
conditions:
|
||||
default:
|
||||
- lastTransitionTime: "1970-01-01T00:00:00Z"
|
||||
message: Waiting for controller
|
||||
reason: Pending
|
||||
status: Unknown
|
||||
type: Programmed
|
||||
description: "Conditions describe the current conditions of the KongClusterPluginStatus.
|
||||
\n Known condition types are: \n * \"Programmed\""
|
||||
items:
|
||||
description: "Condition contains details for one aspect of the current
|
||||
state of this API Resource. --- This struct is intended for direct
|
||||
use as an array at the field path .status.conditions. For example,
|
||||
\n type FooStatus struct{ // Represents the observations of a
|
||||
foo's current state. // Known .status.conditions.type are: \"Available\",
|
||||
\"Progressing\", and \"Degraded\" // +patchMergeKey=type // +patchStrategy=merge
|
||||
// +listType=map // +listMapKey=type Conditions []metav1.Condition
|
||||
`json:\"conditions,omitempty\" patchStrategy:\"merge\" patchMergeKey:\"type\"
|
||||
protobuf:\"bytes,1,rep,name=conditions\"` \n // other fields }"
|
||||
properties:
|
||||
lastTransitionTime:
|
||||
description: lastTransitionTime is the last time the condition
|
||||
transitioned from one status to another. This should be when
|
||||
the underlying condition changed. If that is not known, then
|
||||
using the time when the API field changed is acceptable.
|
||||
format: date-time
|
||||
type: string
|
||||
message:
|
||||
description: message is a human readable message indicating
|
||||
details about the transition. This may be an empty string.
|
||||
maxLength: 32768
|
||||
type: string
|
||||
observedGeneration:
|
||||
description: observedGeneration represents the .metadata.generation
|
||||
that the condition was set based upon. For instance, if .metadata.generation
|
||||
is currently 12, but the .status.conditions[x].observedGeneration
|
||||
is 9, the condition is out of date with respect to the current
|
||||
state of the instance.
|
||||
format: int64
|
||||
minimum: 0
|
||||
type: integer
|
||||
reason:
|
||||
description: reason contains a programmatic identifier indicating
|
||||
the reason for the condition's last transition. Producers
|
||||
of specific condition types may define expected values and
|
||||
meanings for this field, and whether the values are considered
|
||||
a guaranteed API. The value should be a CamelCase string.
|
||||
This field may not be empty.
|
||||
maxLength: 1024
|
||||
minLength: 1
|
||||
pattern: ^[A-Za-z]([A-Za-z0-9_,:]*[A-Za-z0-9_])?$
|
||||
type: string
|
||||
status:
|
||||
description: status of the condition, one of True, False, Unknown.
|
||||
enum:
|
||||
- "True"
|
||||
- "False"
|
||||
- Unknown
|
||||
type: string
|
||||
type:
|
||||
description: type of condition in CamelCase or in foo.example.com/CamelCase.
|
||||
--- Many .condition.type values are consistent across resources
|
||||
like Available, but because arbitrary conditions can be useful
|
||||
(see .node.status.conditions), the ability to deconflict is
|
||||
important. The regex it matches is (dns1123SubdomainFmt/)?(qualifiedNameFmt)
|
||||
maxLength: 316
|
||||
pattern: ^([a-z0-9]([-a-z0-9]*[a-z0-9])?(\.[a-z0-9]([-a-z0-9]*[a-z0-9])?)*/)?(([A-Za-z0-9][-A-Za-z0-9_.]*)?[A-Za-z0-9])$
|
||||
type: string
|
||||
required:
|
||||
- lastTransitionTime
|
||||
- message
|
||||
- reason
|
||||
- status
|
||||
- type
|
||||
type: object
|
||||
maxItems: 8
|
||||
type: array
|
||||
x-kubernetes-list-map-keys:
|
||||
- type
|
||||
x-kubernetes-list-type: map
|
||||
type: object
|
||||
required:
|
||||
- plugin
|
||||
type: object
|
||||
@@ -213,8 +306,142 @@ apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
annotations:
|
||||
controller-gen.kubebuilder.io/version: v0.11.1
|
||||
creationTimestamp: null
|
||||
controller-gen.kubebuilder.io/version: v0.13.0
|
||||
name: kongconsumergroups.configuration.konghq.com
|
||||
spec:
|
||||
group: configuration.konghq.com
|
||||
names:
|
||||
categories:
|
||||
- kong-ingress-controller
|
||||
kind: KongConsumerGroup
|
||||
listKind: KongConsumerGroupList
|
||||
plural: kongconsumergroups
|
||||
shortNames:
|
||||
- kcg
|
||||
singular: kongconsumergroup
|
||||
scope: Namespaced
|
||||
versions:
|
||||
- additionalPrinterColumns:
|
||||
- description: Age
|
||||
jsonPath: .metadata.creationTimestamp
|
||||
name: Age
|
||||
type: date
|
||||
- jsonPath: .status.conditions[?(@.type=="Programmed")].status
|
||||
name: Programmed
|
||||
type: string
|
||||
name: v1beta1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
description: KongConsumerGroup is the Schema for the kongconsumergroups API.
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
status:
|
||||
description: Status represents the current status of the KongConsumer
|
||||
resource.
|
||||
properties:
|
||||
conditions:
|
||||
default:
|
||||
- lastTransitionTime: "1970-01-01T00:00:00Z"
|
||||
message: Waiting for controller
|
||||
reason: Pending
|
||||
status: Unknown
|
||||
type: Programmed
|
||||
description: "Conditions describe the current conditions of the KongConsumerGroup.
|
||||
\n Known condition types are: \n * \"Programmed\""
|
||||
items:
|
||||
description: "Condition contains details for one aspect of the current
|
||||
state of this API Resource. --- This struct is intended for direct
|
||||
use as an array at the field path .status.conditions. For example,
|
||||
\n type FooStatus struct{ // Represents the observations of a
|
||||
foo's current state. // Known .status.conditions.type are: \"Available\",
|
||||
\"Progressing\", and \"Degraded\" // +patchMergeKey=type // +patchStrategy=merge
|
||||
// +listType=map // +listMapKey=type Conditions []metav1.Condition
|
||||
`json:\"conditions,omitempty\" patchStrategy:\"merge\" patchMergeKey:\"type\"
|
||||
protobuf:\"bytes,1,rep,name=conditions\"` \n // other fields }"
|
||||
properties:
|
||||
lastTransitionTime:
|
||||
description: lastTransitionTime is the last time the condition
|
||||
transitioned from one status to another. This should be when
|
||||
the underlying condition changed. If that is not known, then
|
||||
using the time when the API field changed is acceptable.
|
||||
format: date-time
|
||||
type: string
|
||||
message:
|
||||
description: message is a human readable message indicating
|
||||
details about the transition. This may be an empty string.
|
||||
maxLength: 32768
|
||||
type: string
|
||||
observedGeneration:
|
||||
description: observedGeneration represents the .metadata.generation
|
||||
that the condition was set based upon. For instance, if .metadata.generation
|
||||
is currently 12, but the .status.conditions[x].observedGeneration
|
||||
is 9, the condition is out of date with respect to the current
|
||||
state of the instance.
|
||||
format: int64
|
||||
minimum: 0
|
||||
type: integer
|
||||
reason:
|
||||
description: reason contains a programmatic identifier indicating
|
||||
the reason for the condition's last transition. Producers
|
||||
of specific condition types may define expected values and
|
||||
meanings for this field, and whether the values are considered
|
||||
a guaranteed API. The value should be a CamelCase string.
|
||||
This field may not be empty.
|
||||
maxLength: 1024
|
||||
minLength: 1
|
||||
pattern: ^[A-Za-z]([A-Za-z0-9_,:]*[A-Za-z0-9_])?$
|
||||
type: string
|
||||
status:
|
||||
description: status of the condition, one of True, False, Unknown.
|
||||
enum:
|
||||
- "True"
|
||||
- "False"
|
||||
- Unknown
|
||||
type: string
|
||||
type:
|
||||
description: type of condition in CamelCase or in foo.example.com/CamelCase.
|
||||
--- Many .condition.type values are consistent across resources
|
||||
like Available, but because arbitrary conditions can be useful
|
||||
(see .node.status.conditions), the ability to deconflict is
|
||||
important. The regex it matches is (dns1123SubdomainFmt/)?(qualifiedNameFmt)
|
||||
maxLength: 316
|
||||
pattern: ^([a-z0-9]([-a-z0-9]*[a-z0-9])?(\.[a-z0-9]([-a-z0-9]*[a-z0-9])?)*/)?(([A-Za-z0-9][-A-Za-z0-9_.]*)?[A-Za-z0-9])$
|
||||
type: string
|
||||
required:
|
||||
- lastTransitionTime
|
||||
- message
|
||||
- reason
|
||||
- status
|
||||
- type
|
||||
type: object
|
||||
maxItems: 8
|
||||
type: array
|
||||
x-kubernetes-list-map-keys:
|
||||
- type
|
||||
x-kubernetes-list-type: map
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
subresources:
|
||||
status: {}
|
||||
---
|
||||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
annotations:
|
||||
controller-gen.kubebuilder.io/version: v0.13.0
|
||||
name: kongconsumers.configuration.konghq.com
|
||||
spec:
|
||||
group: configuration.konghq.com
|
||||
@@ -238,6 +465,9 @@ spec:
|
||||
jsonPath: .metadata.creationTimestamp
|
||||
name: Age
|
||||
type: date
|
||||
- jsonPath: .status.conditions[?(@.type=="Programmed")].status
|
||||
name: Programmed
|
||||
type: string
|
||||
name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
@@ -248,6 +478,12 @@ spec:
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
consumerGroups:
|
||||
description: ConsumerGroups are references to consumer groups (that consumer
|
||||
wants to be part of) provisioned in Kong.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
credentials:
|
||||
description: Credentials are references to secrets containing a credential
|
||||
to be provisioned in Kong.
|
||||
@@ -265,6 +501,91 @@ spec:
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
status:
|
||||
description: Status represents the current status of the KongConsumer
|
||||
resource.
|
||||
properties:
|
||||
conditions:
|
||||
default:
|
||||
- lastTransitionTime: "1970-01-01T00:00:00Z"
|
||||
message: Waiting for controller
|
||||
reason: Pending
|
||||
status: Unknown
|
||||
type: Programmed
|
||||
description: "Conditions describe the current conditions of the KongConsumer.
|
||||
\n Known condition types are: \n * \"Programmed\""
|
||||
items:
|
||||
description: "Condition contains details for one aspect of the current
|
||||
state of this API Resource. --- This struct is intended for direct
|
||||
use as an array at the field path .status.conditions. For example,
|
||||
\n type FooStatus struct{ // Represents the observations of a
|
||||
foo's current state. // Known .status.conditions.type are: \"Available\",
|
||||
\"Progressing\", and \"Degraded\" // +patchMergeKey=type // +patchStrategy=merge
|
||||
// +listType=map // +listMapKey=type Conditions []metav1.Condition
|
||||
`json:\"conditions,omitempty\" patchStrategy:\"merge\" patchMergeKey:\"type\"
|
||||
protobuf:\"bytes,1,rep,name=conditions\"` \n // other fields }"
|
||||
properties:
|
||||
lastTransitionTime:
|
||||
description: lastTransitionTime is the last time the condition
|
||||
transitioned from one status to another. This should be when
|
||||
the underlying condition changed. If that is not known, then
|
||||
using the time when the API field changed is acceptable.
|
||||
format: date-time
|
||||
type: string
|
||||
message:
|
||||
description: message is a human readable message indicating
|
||||
details about the transition. This may be an empty string.
|
||||
maxLength: 32768
|
||||
type: string
|
||||
observedGeneration:
|
||||
description: observedGeneration represents the .metadata.generation
|
||||
that the condition was set based upon. For instance, if .metadata.generation
|
||||
is currently 12, but the .status.conditions[x].observedGeneration
|
||||
is 9, the condition is out of date with respect to the current
|
||||
state of the instance.
|
||||
format: int64
|
||||
minimum: 0
|
||||
type: integer
|
||||
reason:
|
||||
description: reason contains a programmatic identifier indicating
|
||||
the reason for the condition's last transition. Producers
|
||||
of specific condition types may define expected values and
|
||||
meanings for this field, and whether the values are considered
|
||||
a guaranteed API. The value should be a CamelCase string.
|
||||
This field may not be empty.
|
||||
maxLength: 1024
|
||||
minLength: 1
|
||||
pattern: ^[A-Za-z]([A-Za-z0-9_,:]*[A-Za-z0-9_])?$
|
||||
type: string
|
||||
status:
|
||||
description: status of the condition, one of True, False, Unknown.
|
||||
enum:
|
||||
- "True"
|
||||
- "False"
|
||||
- Unknown
|
||||
type: string
|
||||
type:
|
||||
description: type of condition in CamelCase or in foo.example.com/CamelCase.
|
||||
--- Many .condition.type values are consistent across resources
|
||||
like Available, but because arbitrary conditions can be useful
|
||||
(see .node.status.conditions), the ability to deconflict is
|
||||
important. The regex it matches is (dns1123SubdomainFmt/)?(qualifiedNameFmt)
|
||||
maxLength: 316
|
||||
pattern: ^([a-z0-9]([-a-z0-9]*[a-z0-9])?(\.[a-z0-9]([-a-z0-9]*[a-z0-9])?)*/)?(([A-Za-z0-9][-A-Za-z0-9_.]*)?[A-Za-z0-9])$
|
||||
type: string
|
||||
required:
|
||||
- lastTransitionTime
|
||||
- message
|
||||
- reason
|
||||
- status
|
||||
- type
|
||||
type: object
|
||||
maxItems: 8
|
||||
type: array
|
||||
x-kubernetes-list-map-keys:
|
||||
- type
|
||||
x-kubernetes-list-type: map
|
||||
type: object
|
||||
username:
|
||||
description: Username is a Kong cluster-unique username of the consumer.
|
||||
type: string
|
||||
@@ -278,8 +599,7 @@ apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
annotations:
|
||||
controller-gen.kubebuilder.io/version: v0.11.1
|
||||
creationTimestamp: null
|
||||
controller-gen.kubebuilder.io/version: v0.13.0
|
||||
name: kongingresses.configuration.konghq.com
|
||||
spec:
|
||||
group: configuration.konghq.com
|
||||
@@ -381,8 +701,7 @@ spec:
|
||||
type: integer
|
||||
methods:
|
||||
description: 'Methods is a list of HTTP methods that match this Route.
|
||||
Deprecated: use Ingress'' "konghq.com/override-protocols" annotation
|
||||
instead.'
|
||||
Deprecated: use Ingress'' "konghq.com/methods" annotation instead.'
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
@@ -407,6 +726,8 @@ spec:
|
||||
allow. Deprecated: use Ingress'' "konghq.com/protocols" annotation
|
||||
instead.'
|
||||
items:
|
||||
description: KongProtocol is a valid Kong protocol. This alias is
|
||||
necessary to deal with https://github.com/kubernetes-sigs/controller-tools/issues/342
|
||||
enum:
|
||||
- http
|
||||
- https
|
||||
@@ -448,8 +769,8 @@ spec:
|
||||
type: object
|
||||
upstream:
|
||||
description: Upstream represents a virtual hostname and can be used to
|
||||
load balance incoming requests over multiple targets (e.g. Kubernetes
|
||||
Services can be a target, or URLs can be targets).
|
||||
loadbalance incoming requests over multiple targets (e.g. Kubernetes
|
||||
`Services` can be a target, OR `Endpoints` can be targets).
|
||||
properties:
|
||||
algorithm:
|
||||
description: Algorithm is the load balancing algorithm to use.
|
||||
@@ -457,6 +778,7 @@ spec:
|
||||
- round-robin
|
||||
- consistent-hashing
|
||||
- least-connections
|
||||
- latency
|
||||
type: string
|
||||
hash_fallback:
|
||||
description: 'HashFallback defines What to use as hashing input if
|
||||
@@ -512,6 +834,12 @@ spec:
|
||||
concurrency:
|
||||
minimum: 1
|
||||
type: integer
|
||||
headers:
|
||||
additionalProperties:
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
type: object
|
||||
healthy:
|
||||
description: Healthy configures thresholds and HTTP status
|
||||
codes to mark targets healthy for an upstream.
|
||||
@@ -626,8 +954,7 @@ apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
annotations:
|
||||
controller-gen.kubebuilder.io/version: v0.11.1
|
||||
creationTimestamp: null
|
||||
controller-gen.kubebuilder.io/version: v0.13.0
|
||||
name: kongplugins.configuration.konghq.com
|
||||
spec:
|
||||
group: configuration.konghq.com
|
||||
@@ -661,6 +988,9 @@ spec:
|
||||
name: Config
|
||||
priority: 1
|
||||
type: string
|
||||
- jsonPath: .status.conditions[?(@.type=="Programmed")].status
|
||||
name: Programmed
|
||||
type: string
|
||||
name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
@@ -708,6 +1038,11 @@ spec:
|
||||
disabled:
|
||||
description: Disabled set if the plugin is disabled or not.
|
||||
type: boolean
|
||||
instance_name:
|
||||
description: InstanceName is an optional custom name to identify an instance
|
||||
of the plugin. This is useful when running the same plugin in multiple
|
||||
contexts, for example, on multiple services.
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
@@ -749,6 +1084,8 @@ spec:
|
||||
description: Protocols configures plugin to run on requests received on
|
||||
specific protocols.
|
||||
items:
|
||||
description: KongProtocol is a valid Kong protocol. This alias is necessary
|
||||
to deal with https://github.com/kubernetes-sigs/controller-tools/issues/342
|
||||
enum:
|
||||
- http
|
||||
- https
|
||||
@@ -767,6 +1104,90 @@ spec:
|
||||
- second
|
||||
- all
|
||||
type: string
|
||||
status:
|
||||
description: Status represents the current status of the KongPlugin resource.
|
||||
properties:
|
||||
conditions:
|
||||
default:
|
||||
- lastTransitionTime: "1970-01-01T00:00:00Z"
|
||||
message: Waiting for controller
|
||||
reason: Pending
|
||||
status: Unknown
|
||||
type: Programmed
|
||||
description: "Conditions describe the current conditions of the KongPluginStatus.
|
||||
\n Known condition types are: \n * \"Programmed\""
|
||||
items:
|
||||
description: "Condition contains details for one aspect of the current
|
||||
state of this API Resource. --- This struct is intended for direct
|
||||
use as an array at the field path .status.conditions. For example,
|
||||
\n type FooStatus struct{ // Represents the observations of a
|
||||
foo's current state. // Known .status.conditions.type are: \"Available\",
|
||||
\"Progressing\", and \"Degraded\" // +patchMergeKey=type // +patchStrategy=merge
|
||||
// +listType=map // +listMapKey=type Conditions []metav1.Condition
|
||||
`json:\"conditions,omitempty\" patchStrategy:\"merge\" patchMergeKey:\"type\"
|
||||
protobuf:\"bytes,1,rep,name=conditions\"` \n // other fields }"
|
||||
properties:
|
||||
lastTransitionTime:
|
||||
description: lastTransitionTime is the last time the condition
|
||||
transitioned from one status to another. This should be when
|
||||
the underlying condition changed. If that is not known, then
|
||||
using the time when the API field changed is acceptable.
|
||||
format: date-time
|
||||
type: string
|
||||
message:
|
||||
description: message is a human readable message indicating
|
||||
details about the transition. This may be an empty string.
|
||||
maxLength: 32768
|
||||
type: string
|
||||
observedGeneration:
|
||||
description: observedGeneration represents the .metadata.generation
|
||||
that the condition was set based upon. For instance, if .metadata.generation
|
||||
is currently 12, but the .status.conditions[x].observedGeneration
|
||||
is 9, the condition is out of date with respect to the current
|
||||
state of the instance.
|
||||
format: int64
|
||||
minimum: 0
|
||||
type: integer
|
||||
reason:
|
||||
description: reason contains a programmatic identifier indicating
|
||||
the reason for the condition's last transition. Producers
|
||||
of specific condition types may define expected values and
|
||||
meanings for this field, and whether the values are considered
|
||||
a guaranteed API. The value should be a CamelCase string.
|
||||
This field may not be empty.
|
||||
maxLength: 1024
|
||||
minLength: 1
|
||||
pattern: ^[A-Za-z]([A-Za-z0-9_,:]*[A-Za-z0-9_])?$
|
||||
type: string
|
||||
status:
|
||||
description: status of the condition, one of True, False, Unknown.
|
||||
enum:
|
||||
- "True"
|
||||
- "False"
|
||||
- Unknown
|
||||
type: string
|
||||
type:
|
||||
description: type of condition in CamelCase or in foo.example.com/CamelCase.
|
||||
--- Many .condition.type values are consistent across resources
|
||||
like Available, but because arbitrary conditions can be useful
|
||||
(see .node.status.conditions), the ability to deconflict is
|
||||
important. The regex it matches is (dns1123SubdomainFmt/)?(qualifiedNameFmt)
|
||||
maxLength: 316
|
||||
pattern: ^([a-z0-9]([-a-z0-9]*[a-z0-9])?(\.[a-z0-9]([-a-z0-9]*[a-z0-9])?)*/)?(([A-Za-z0-9][-A-Za-z0-9_.]*)?[A-Za-z0-9])$
|
||||
type: string
|
||||
required:
|
||||
- lastTransitionTime
|
||||
- message
|
||||
- reason
|
||||
- status
|
||||
- type
|
||||
type: object
|
||||
maxItems: 8
|
||||
type: array
|
||||
x-kubernetes-list-map-keys:
|
||||
- type
|
||||
x-kubernetes-list-type: map
|
||||
type: object
|
||||
required:
|
||||
- plugin
|
||||
type: object
|
||||
@@ -779,8 +1200,7 @@ apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
annotations:
|
||||
controller-gen.kubebuilder.io/version: v0.11.1
|
||||
creationTimestamp: null
|
||||
controller-gen.kubebuilder.io/version: v0.13.0
|
||||
name: tcpingresses.configuration.konghq.com
|
||||
spec:
|
||||
group: configuration.konghq.com
|
||||
@@ -966,8 +1386,7 @@ apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
annotations:
|
||||
controller-gen.kubebuilder.io/version: v0.11.1
|
||||
creationTimestamp: null
|
||||
controller-gen.kubebuilder.io/version: v0.13.0
|
||||
name: udpingresses.configuration.konghq.com
|
||||
spec:
|
||||
group: configuration.konghq.com
|
||||
|
||||
@@ -88,7 +88,7 @@ enterprise:
|
||||
enabled: true
|
||||
env:
|
||||
admin_access_log: /dev/stdout
|
||||
admin_api_uri: https://kong.127-0-0-1.nip.io/api
|
||||
admin_gui_api_url: https://kong.127-0-0-1.nip.io/api
|
||||
admin_error_log: /dev/stdout
|
||||
admin_gui_access_log: /dev/stdout
|
||||
admin_gui_error_log: /dev/stdout
|
||||
@@ -146,7 +146,7 @@ extraLabels:
|
||||
konghq.com/component: quickstart
|
||||
image:
|
||||
repository: kong/kong-gateway
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
ingressController:
|
||||
enabled: true
|
||||
env:
|
||||
@@ -162,7 +162,7 @@ ingressController:
|
||||
publish_service: kong/quickstart-kong-proxy
|
||||
image:
|
||||
repository: docker.io/kong/kubernetes-ingress-controller
|
||||
tag: "2.8"
|
||||
tag: "2.10"
|
||||
ingressClass: default
|
||||
installCRDs: false
|
||||
manager:
|
||||
@@ -278,8 +278,4 @@ status:
|
||||
tls:
|
||||
containerPort: 8543
|
||||
enabled: false
|
||||
updateStrategy:
|
||||
rollingUpdate:
|
||||
maxSurge: 100%
|
||||
maxUnavailable: 100%
|
||||
type: RollingUpdate
|
||||
|
||||
|
||||
@@ -12,7 +12,7 @@
|
||||
|
||||
image:
|
||||
repository: kong/kong-gateway
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
|
||||
env:
|
||||
prefix: /kong_prefix/
|
||||
|
||||
@@ -9,7 +9,7 @@
|
||||
|
||||
image:
|
||||
repository: kong/kong-gateway
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
|
||||
admin:
|
||||
enabled: true
|
||||
|
||||
@@ -2,7 +2,7 @@
|
||||
|
||||
image:
|
||||
repository: kong
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
|
||||
env:
|
||||
prefix: /kong_prefix/
|
||||
|
||||
@@ -4,7 +4,7 @@
|
||||
|
||||
image:
|
||||
repository: kong/kong-gateway
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
|
||||
enterprise:
|
||||
enabled: true
|
||||
|
||||
@@ -14,7 +14,7 @@
|
||||
|
||||
image:
|
||||
repository: kong/kong-gateway
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
|
||||
env:
|
||||
database: postgres
|
||||
|
||||
@@ -12,7 +12,7 @@
|
||||
|
||||
image:
|
||||
repository: kong/kong-gateway
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
|
||||
env:
|
||||
role: data_plane
|
||||
@@ -43,4 +43,3 @@ portal:
|
||||
|
||||
portalapi:
|
||||
enabled: false
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@
|
||||
|
||||
image:
|
||||
repository: kong
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
|
||||
env:
|
||||
prefix: /kong_prefix/
|
||||
|
||||
@@ -11,7 +11,7 @@
|
||||
|
||||
image:
|
||||
repository: kong
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
|
||||
env:
|
||||
prefix: /kong_prefix/
|
||||
|
||||
@@ -6,7 +6,7 @@
|
||||
|
||||
image:
|
||||
repository: kong
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
|
||||
env:
|
||||
prefix: /kong_prefix/
|
||||
|
||||
@@ -32,7 +32,7 @@ app.kubernetes.io/instance: "{{ .Release.Name }}"
|
||||
app.kubernetes.io/managed-by: "{{ .Release.Service }}"
|
||||
app.kubernetes.io/version: {{ .Chart.AppVersion | quote }}
|
||||
{{- range $key, $value := .Values.extraLabels }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{ $key }}: {{ include "kong.renderTpl" (dict "value" $value "context" $) | quote }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
@@ -78,13 +78,16 @@ Create Ingress resource for a Kong service
|
||||
{{- $path := .ingress.path -}}
|
||||
{{- $hostname := .ingress.hostname -}}
|
||||
{{- $pathType := .ingress.pathType -}}
|
||||
apiVersion: {{ .ingressVersion }}
|
||||
apiVersion: networking.k8s.io/v1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: {{ .fullName }}-{{ .serviceName }}
|
||||
namespace: {{ .namespace }}
|
||||
labels:
|
||||
{{- .metaLabels | nindent 4 }}
|
||||
{{- range $key, $value := .ingress.labels }}
|
||||
{{- $key | nindent 4 }}: {{ $value | quote }}
|
||||
{{- end }}
|
||||
{{- if .ingress.annotations }}
|
||||
annotations:
|
||||
{{- range $key, $value := .ingress.annotations }}
|
||||
@@ -92,33 +95,74 @@ metadata:
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if (and (not (eq .ingressVersion "extensions/v1beta1")) .ingress.ingressClassName) }}
|
||||
{{- if .ingress.ingressClassName }}
|
||||
ingressClassName: {{ .ingress.ingressClassName }}
|
||||
{{- end }}
|
||||
rules:
|
||||
- host: {{ $hostname | quote }}
|
||||
http:
|
||||
{{- if ( not (or $hostname .ingress.hosts)) }}
|
||||
- http:
|
||||
paths:
|
||||
- backend:
|
||||
{{- if (not (eq .ingressVersion "networking.k8s.io/v1")) }}
|
||||
serviceName: {{ .fullName }}-{{ .serviceName }}
|
||||
servicePort: {{ $servicePort }}
|
||||
{{- else }}
|
||||
service:
|
||||
name: {{ .fullName }}-{{ .serviceName }}
|
||||
port:
|
||||
number: {{ $servicePort }}
|
||||
{{- end }}
|
||||
path: {{ $path }}
|
||||
{{- if (not (eq .ingressVersion "extensions/v1beta1")) }}
|
||||
pathType: {{ $pathType }}
|
||||
{{- else if $hostname }}
|
||||
- host: {{ $hostname | quote }}
|
||||
http:
|
||||
paths:
|
||||
- backend:
|
||||
service:
|
||||
name: {{ .fullName }}-{{ .serviceName }}
|
||||
port:
|
||||
number: {{ $servicePort }}
|
||||
path: {{ $path }}
|
||||
pathType: {{ $pathType }}
|
||||
{{- end }}
|
||||
{{- range .ingress.hosts }}
|
||||
- host: {{ .host | quote }}
|
||||
http:
|
||||
paths:
|
||||
{{- range .paths }}
|
||||
- backend:
|
||||
{{- if .backend -}}
|
||||
{{ .backend | toYaml | nindent 12 }}
|
||||
{{- else }}
|
||||
service:
|
||||
name: {{ $.fullName }}-{{ $.serviceName }}
|
||||
port:
|
||||
number: {{ $servicePort }}
|
||||
{{- end }}
|
||||
{{- if (and $hostname (and (eq $path .path))) }}
|
||||
{{- fail "duplication of specified ingress path" }}
|
||||
{{- end }}
|
||||
path: {{ .path }}
|
||||
pathType: {{ .pathType }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if (hasKey .ingress "tls") }}
|
||||
tls:
|
||||
- hosts:
|
||||
- {{ $hostname | quote }}
|
||||
secretName: {{ .ingress.tls }}
|
||||
{{- end -}}
|
||||
{{- if (kindIs "string" .ingress.tls) }}
|
||||
- hosts:
|
||||
{{- range .ingress.hosts }}
|
||||
- {{ .host | quote }}
|
||||
{{- end }}
|
||||
{{- if $hostname }}
|
||||
- {{ $hostname | quote }}
|
||||
{{- end }}
|
||||
secretName: {{ .ingress.tls }}
|
||||
{{- else if (kindIs "slice" .ingress.tls) }}
|
||||
{{- range .ingress.tls }}
|
||||
- hosts:
|
||||
{{- range .hosts }}
|
||||
- {{ . | quote }}
|
||||
{{- end }}
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
@@ -286,10 +330,11 @@ Create KONG_STREAM_LISTEN string
|
||||
*/}}
|
||||
{{- define "kong.streamListen" -}}
|
||||
{{- $unifiedListen := list -}}
|
||||
{{- $address := (default "0.0.0.0" .address) -}}
|
||||
{{- range .stream -}}
|
||||
{{- $listenConfig := dict -}}
|
||||
{{- $listenConfig := merge $listenConfig . -}}
|
||||
{{- $_ := set $listenConfig "address" "0.0.0.0" -}}
|
||||
{{- $_ := set $listenConfig "address" $address -}}
|
||||
{{/* You set NGINX stream listens to UDP using a parameter due to historical reasons.
|
||||
Our configuration is dual-purpose, for both the Service and listen string, so we
|
||||
forcibly inject this parameter if that's the Service protocol. The default handles
|
||||
@@ -326,7 +371,18 @@ Return the admin API service name for service discovery
|
||||
{{- $gatewayDiscovery := .Values.ingressController.gatewayDiscovery -}}
|
||||
{{- if $gatewayDiscovery.enabled -}}
|
||||
{{- $adminApiService := $gatewayDiscovery.adminApiService -}}
|
||||
{{- $_ := required ".ingressController.gatewayDiscovery.adminApiService has to be provided when .Values.ingressController.gatewayDiscovery.enabled is set to true" $adminApiService -}}
|
||||
{{- $adminApiServiceName := $gatewayDiscovery.adminApiService.name -}}
|
||||
{{- $generateAdminApiService := $gatewayDiscovery.generateAdminApiService -}}
|
||||
|
||||
{{- if and $generateAdminApiService $adminApiService.name -}}
|
||||
{{- fail (printf ".Values.ingressController.gatewayDiscovery.adminApiService and .Values.ingressController.gatewayDiscovery.generateAdminApiService must not be provided at the same time") -}}
|
||||
{{- end -}}
|
||||
|
||||
{{- if $generateAdminApiService -}}
|
||||
{{- $adminApiServiceName = (printf "%s-%s" .Release.Name "gateway-admin") -}}
|
||||
{{- else }}
|
||||
{{- $_ := required ".ingressController.gatewayDiscovery.adminApiService.name has to be provided when .Values.ingressController.gatewayDiscovery.enabled is set to true" $adminApiServiceName -}}
|
||||
{{- end }}
|
||||
|
||||
{{- if (semverCompare "< 2.9.0" (include "kong.effectiveVersion" .Values.ingressController.image)) }}
|
||||
{{- fail (printf "Gateway discovery is available in controller versions 2.9 and up. Detected %s" (include "kong.effectiveVersion" .Values.ingressController.image)) }}
|
||||
@@ -337,9 +393,7 @@ Return the admin API service name for service discovery
|
||||
{{- end }}
|
||||
|
||||
{{- $namespace := $adminApiService.namespace | default ( include "kong.namespace" . ) -}}
|
||||
{{- $name := $adminApiService.name -}}
|
||||
{{- $_ := required ".ingressController.gatewayDiscovery.adminApiService.name has to be provided when .Values.ingressController.gatewayDiscovery.enabled is set to true" $name -}}
|
||||
{{- printf "%s/%s" $namespace $name -}}
|
||||
{{- printf "%s/%s" $namespace $adminApiServiceName -}}
|
||||
{{- else -}}
|
||||
{{- fail "Can't use gateway discovery when .Values.ingressController.gatewayDiscovery.enabled is set to false." -}}
|
||||
{{- end -}}
|
||||
@@ -405,7 +459,8 @@ The name of the service used for the ingress controller's validation webhook
|
||||
{{- $_ := set $autoEnv "CONTROLLER_ELECTION_ID" (printf "kong-ingress-controller-leader-%s" .Values.ingressController.ingressClass) -}}
|
||||
|
||||
{{- if .Values.ingressController.admissionWebhook.enabled }}
|
||||
{{- $_ := set $autoEnv "CONTROLLER_ADMISSION_WEBHOOK_LISTEN" (printf "0.0.0.0:%d" (int64 .Values.ingressController.admissionWebhook.port)) -}}
|
||||
{{- $address := (default "0.0.0.0" .Values.ingressController.admissionWebhook.address) -}}
|
||||
{{- $_ := set $autoEnv "CONTROLLER_ADMISSION_WEBHOOK_LISTEN" (printf "%s:%d" $address (int64 .Values.ingressController.admissionWebhook.port)) -}}
|
||||
{{- end }}
|
||||
{{- if (not (eq (len .Values.ingressController.watchNamespaces) 0)) }}
|
||||
{{- $_ := set $autoEnv "CONTROLLER_WATCH_NAMESPACE" (.Values.ingressController.watchNamespaces | join ",") -}}
|
||||
@@ -499,6 +554,41 @@ The name of the service used for the ingress controller's validation webhook
|
||||
- name: {{ template "kong.fullname" . }}-tmp
|
||||
emptyDir:
|
||||
sizeLimit: {{ .Values.deployment.tmpDir.sizeLimit }}
|
||||
{{- if (and (not .Values.deployment.serviceAccount.automountServiceAccountToken) (or .Values.deployment.serviceAccount.create .Values.deployment.serviceAccount.name)) }}
|
||||
- name: {{ template "kong.serviceAccountTokenName" . }}
|
||||
{{- /* Due to GKE versions (e.g. v1.23.15-gke.1900) we need to handle pre-release part of the version as well.
|
||||
See the related documentation of semver module that Helm depends on for semverCompare:
|
||||
https://github.com/Masterminds/semver#working-with-prerelease-versions
|
||||
Related Helm issue: https://github.com/helm/helm/issues/3810 */}}
|
||||
{{- if semverCompare ">=1.20.0-0" .Capabilities.KubeVersion.Version }}
|
||||
projected:
|
||||
sources:
|
||||
- serviceAccountToken:
|
||||
expirationSeconds: 3607
|
||||
path: token
|
||||
- configMap:
|
||||
items:
|
||||
- key: ca.crt
|
||||
path: ca.crt
|
||||
name: kube-root-ca.crt
|
||||
- downwardAPI:
|
||||
items:
|
||||
- fieldRef:
|
||||
apiVersion: v1
|
||||
fieldPath: metadata.namespace
|
||||
path: namespace
|
||||
{{- else }}
|
||||
secret:
|
||||
secretName: {{ template "kong.serviceAccountTokenName" . }}
|
||||
items:
|
||||
- key: token
|
||||
path: token
|
||||
- key: ca.crt
|
||||
path: ca.crt
|
||||
- key: namespace
|
||||
path: namespace
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if and ( .Capabilities.APIVersions.Has "cert-manager.io/v1" ) .Values.certificates.enabled -}}
|
||||
{{- if .Values.certificates.cluster.enabled }}
|
||||
- name: {{ include "kong.fullname" . }}-cluster-cert
|
||||
@@ -733,10 +823,22 @@ The name of the service used for the ingress controller's validation webhook
|
||||
|
||||
{{/* effectiveVersion takes an image dict from values.yaml. if .effectiveSemver is set, it returns that, else it returns .tag */}}
|
||||
{{- define "kong.effectiveVersion" -}}
|
||||
{{- /* Because Kong Gateway enterprise uses versions with 4 segments and not 3 */ -}}
|
||||
{{- /* as semver does, we need to account for that here by extracting */ -}}
|
||||
{{- /* first 3 segments for comparison */ -}}
|
||||
{{- if .effectiveSemver -}}
|
||||
{{- .effectiveSemver -}}
|
||||
{{- if regexMatch "^[0-9]+.[0-9]+.[0-9]+" .effectiveSemver -}}
|
||||
{{- regexFind "^[0-9]+.[0-9]+.[0-9]+" .effectiveSemver -}}
|
||||
{{- else -}}
|
||||
{{- .effectiveSemver -}}
|
||||
{{- end -}}
|
||||
{{- else -}}
|
||||
{{- (trimSuffix "-redhat" .tag) -}}
|
||||
{{- $tag := (trimSuffix "-redhat" .tag) -}}
|
||||
{{- if regexMatch "^[0-9]+.[0-9]+.[0-9]+" .tag -}}
|
||||
{{- regexFind "^[0-9]+.[0-9]+.[0-9]+" .tag -}}
|
||||
{{- else -}}
|
||||
{{- .tag -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
@@ -855,7 +957,7 @@ the template that it itself is using form the above sections.
|
||||
{{- end -}}
|
||||
{{- $listenConfig := dict -}}
|
||||
{{- $listenConfig := merge $listenConfig . -}}
|
||||
{{- $_ := set $listenConfig "address" $address -}}
|
||||
{{- $_ := set $listenConfig "address" (default $address .address) -}}
|
||||
{{- $_ := set $autoEnv "KONG_ADMIN_LISTEN" (include "kong.listen" $listenConfig) -}}
|
||||
|
||||
{{- if or .tls.client.secretName .tls.client.caBundle -}}
|
||||
@@ -899,6 +1001,7 @@ the template that it itself is using form the above sections.
|
||||
{{- end -}}
|
||||
|
||||
{{- if .Values.admin.ingress.enabled }}
|
||||
{{- $_ := set $autoEnv "KONG_ADMIN_GUI_API_URL" (include "kong.ingress.serviceUrl" .Values.admin.ingress) -}}
|
||||
{{- $_ := set $autoEnv "KONG_ADMIN_API_URI" (include "kong.ingress.serviceUrl" .Values.admin.ingress) -}}
|
||||
{{- end -}}
|
||||
|
||||
@@ -1150,6 +1253,24 @@ resource roles into their separate templates.
|
||||
- namespaces
|
||||
verbs:
|
||||
- list
|
||||
{{- if (semverCompare ">= 2.11.0" (include "kong.effectiveVersion" .Values.ingressController.image)) }}
|
||||
- apiGroups:
|
||||
- configuration.konghq.com
|
||||
resources:
|
||||
- kongconsumergroups
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- configuration.konghq.com
|
||||
resources:
|
||||
- kongconsumergroups/status
|
||||
verbs:
|
||||
- get
|
||||
- patch
|
||||
- update
|
||||
{{- end }}
|
||||
{{- if (semverCompare "< 2.10.0" (include "kong.effectiveVersion" .Values.ingressController.image)) }}
|
||||
- apiGroups:
|
||||
- ""
|
||||
@@ -1526,22 +1647,54 @@ Kubernetes Cluster-scoped resources it uses to build Kong configuration.
|
||||
- watch
|
||||
{{- end -}}
|
||||
|
||||
{{- define "kong.autoscalingVersion" -}}
|
||||
{{- if (.Capabilities.APIVersions.Has "autoscaling/v2") -}}
|
||||
autoscaling/v2
|
||||
{{- else if (.Capabilities.APIVersions.Has "autoscaling/v2beta2") -}}
|
||||
autoscaling/v2beta2
|
||||
{{- else -}}
|
||||
autoscaling/v1
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{- define "kong.policyVersion" -}}
|
||||
{{- if (.Capabilities.APIVersions.Has "policy/v1beta1" ) -}}
|
||||
policy/v1beta1
|
||||
{{- else -}}
|
||||
{{- fail (printf "Cluster doesn't have policy/v1beta1 API." ) }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{- define "kong.renderTpl" -}}
|
||||
{{- if typeIs "string" .value }}
|
||||
{{- tpl .value .context }}
|
||||
{{- else }}
|
||||
{{- tpl (.value | toYaml) .context }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
{{- define "kong.ingressVersion" -}}
|
||||
{{- if (.Capabilities.APIVersions.Has "networking.k8s.io/v1/Ingress") -}}
|
||||
{{- if (.Capabilities.APIVersions.Has "networking.k8s.io/v1") -}}
|
||||
networking.k8s.io/v1
|
||||
{{- else if (.Capabilities.APIVersions.Has "networking.k8s.io/v1beta1/Ingress") -}}
|
||||
{{- else if (.Capabilities.APIVersions.Has "networking.k8s.io/v1beta1") -}}
|
||||
networking.k8s.io/v1beta1
|
||||
{{- else -}}
|
||||
extensions/v1beta1
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{- define "kong.autoscalingVersion" -}}
|
||||
{{- if (.Capabilities.APIVersions.Has "autoscaling/v2/HorizontalPodAutoscaler") -}}
|
||||
autoscaling/v2
|
||||
{{- else if (.Capabilities.APIVersions.Has "autoscaling/v2beta2/HorizontalPodAutoscaler") -}}
|
||||
autoscaling/v2beta2
|
||||
{{- else -}}
|
||||
autoscaling/v1
|
||||
{{- define "kong.proxy.compatibleReadiness" -}}
|
||||
{{- $proxyReadiness := .Values.readinessProbe -}}
|
||||
{{- if (or (semverCompare "< 3.3.0" (include "kong.effectiveVersion" .Values.image)) (and .Values.ingressController.enabled (semverCompare "< 2.11.0" (include "kong.effectiveVersion" .Values.ingressController.image)))) -}}
|
||||
{{- if (eq $proxyReadiness.httpGet.path "/status/ready") -}}
|
||||
{{- $_ := set $proxyReadiness.httpGet "path" "/status" -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
{{- (toYaml $proxyReadiness) -}}
|
||||
{{- end -}}
|
||||
{{/*
|
||||
appsec labels
|
||||
*/}}
|
||||
{{- define "appsec.labels" -}}
|
||||
{{- end -}}
|
||||
|
||||
|
||||
@@ -46,6 +46,9 @@ webhooks:
|
||||
namespaceSelector:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- with .Values.ingressController.admissionWebhook.timeoutSeconds }}
|
||||
timeoutSeconds: {{ . }}
|
||||
{{- end }}
|
||||
objectSelector:
|
||||
matchExpressions:
|
||||
- key: owner
|
||||
@@ -80,6 +83,28 @@ webhooks:
|
||||
- UPDATE
|
||||
resources:
|
||||
- secrets
|
||||
{{- if (semverCompare ">= 2.12.0" (include "kong.effectiveVersion" .Values.ingressController.image)) }}
|
||||
- apiGroups:
|
||||
- networking.k8s.io
|
||||
apiVersions:
|
||||
- 'v1'
|
||||
operations:
|
||||
- CREATE
|
||||
- UPDATE
|
||||
resources:
|
||||
- ingresses
|
||||
- apiGroups:
|
||||
- gateway.networking.k8s.io
|
||||
apiVersions:
|
||||
- 'v1alpha2'
|
||||
- 'v1beta1'
|
||||
operations:
|
||||
- CREATE
|
||||
- UPDATE
|
||||
resources:
|
||||
- gateways
|
||||
- httproutes
|
||||
{{- end }}
|
||||
clientConfig:
|
||||
{{- if not .Values.ingressController.admissionWebhook.certificate.provided }}
|
||||
caBundle: {{ b64enc $caCert }}
|
||||
|
||||
@@ -1,3 +1,4 @@
|
||||
{{- if not (eq .Values.kind "Vanilla") -}}
|
||||
{{- if and (eq "standalone" .Values.appsec.mode) (eq .Values.appsec.persistence.enabled true) -}}
|
||||
kind: PersistentVolumeClaim
|
||||
apiVersion: v1
|
||||
@@ -18,3 +19,4 @@ spec:
|
||||
storageClassName: {{ required "A storage class for learning data is required" .Values.appsec.persistence.learning.storageClass.name }}
|
||||
{{- end -}}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@@ -1,4 +1,4 @@
|
||||
{{- if (eq .Values.kind "AppSecStateful") -}}
|
||||
{{- if (and (eq .Values.kind "AppSec") .Values.appsec.persistence.enabled) }}
|
||||
kind: PersistentVolumeClaim
|
||||
apiVersion: v1
|
||||
metadata:
|
||||
|
||||
@@ -0,0 +1,32 @@
|
||||
{{- if not (eq .Values.kind "Vanilla") -}}
|
||||
{{- if .Values.appsec.configMapContent }}
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: {{ .Values.appsec.configMapName | default "appsec-settings-configmap" | quote }}
|
||||
data:
|
||||
{{- if .Values.appsec.configMapContent.crowdsec }}
|
||||
CROWDSEC_ENABLED: {{ .Values.appsec.configMapContent.crowdsec.enabled | default "false" | quote }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.api }}
|
||||
CROWDSEC_API_URL: {{ .Values.appsec.configMapContent.crowdsec.api.url | default "http://crowdsec-service:8080/v1/decisions/stream" }}
|
||||
{{- else }}
|
||||
CROWDSEC_API_URL: "http://crowdsec-service:8080/v1/decisions/stream"
|
||||
{{- end }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.auth }}
|
||||
CROWDSEC_AUTH_METHOD: {{ .Values.appsec.configMapContent.crowdsec.auth.method | default "apikey" }}
|
||||
{{- else }}
|
||||
CROWDSEC_AUTH_METHOD: "apikey"
|
||||
{{- end }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.mode }}
|
||||
CROWDSEC_MODE: {{ .Values.appsec.configMapContent.crowdsec.mode | default "prevent" }}
|
||||
{{- else }}
|
||||
CROWDSEC_MODE: "prevent"
|
||||
{{- end }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.logging }}
|
||||
CROWDSEC_LOGGING: {{ .Values.appsec.configMapContent.crowdsec.logging | default "enabled" }}
|
||||
{{- else }}
|
||||
CROWDSEC_LOGGING: "enabled"
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@@ -0,0 +1,12 @@
|
||||
{{- if not (eq .Values.kind "Vanilla") -}}
|
||||
{{ if .Values.appsec.secretContent }}
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: {{ .Values.appsec.secretName | default "appsec-settings-secret" | quote }}
|
||||
data:
|
||||
{{- if and .Values.appsec.secretContent.crowdsec .Values.appsec.secretContent.crowdsec.auth }}
|
||||
CROWDSEC_AUTH_DATA: {{ .Values.appsec.secretContent.crowdsec.auth.data | b64enc }}
|
||||
{{- end }}
|
||||
{{ end }}
|
||||
{{ end }}
|
||||
@@ -8,7 +8,7 @@ kind: Deployment
|
||||
{{- end }}
|
||||
{{- else if eq .Values.kind "AppSecStateful" }}
|
||||
kind: StatefulSet
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
metadata:
|
||||
name: {{ template "kong.fullname" . }}
|
||||
namespace: {{ template "kong.namespace" . }}
|
||||
@@ -18,13 +18,13 @@ metadata:
|
||||
{{- if .Values.deploymentAnnotations }}
|
||||
annotations:
|
||||
{{- range $key, $value := .Values.deploymentAnnotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{ $key }}: {{ include "kong.renderTpl" (dict "value" $value "context" $) | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if not .Values.autoscaling.enabled }}
|
||||
{{- if eq .Values.kind "AppSecStateful" }}
|
||||
serviceName: "cp-appsec-stateful-set"
|
||||
serviceName: "open-appsec-stateful-set"
|
||||
{{- end }}
|
||||
{{- if or (not .Values.deployment.daemonset) (and (eq .Values.kind "AppSecStateful") ( .Values.deployment.daemonset )) }}
|
||||
replicas: {{ .Values.replicaCount }}
|
||||
@@ -58,7 +58,7 @@ spec:
|
||||
{{- end }}
|
||||
{{- if .Values.podAnnotations }}
|
||||
{{- range $key, $value := .Values.podAnnotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{ $key }}: {{ include "kong.renderTpl" (dict "value" $value "context" $) | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
labels:
|
||||
@@ -67,7 +67,7 @@ spec:
|
||||
app: {{ template "kong.fullname" . }}
|
||||
version: {{ .Chart.AppVersion | quote }}
|
||||
{{- if .Values.podLabels }}
|
||||
{{ toYaml .Values.podLabels | nindent 8 }}
|
||||
{{ include "kong.renderTpl" (dict "value" .Values.podLabels "context" $) | nindent 8 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.deployment.hostNetwork }}
|
||||
@@ -90,6 +90,7 @@ spec:
|
||||
- name: {{ . }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.deployment.kong.enabled }}
|
||||
initContainers:
|
||||
- name: clear-stale-pid
|
||||
image: {{ include "kong.getRepoTag" .Values.image }}
|
||||
@@ -112,6 +113,7 @@ spec:
|
||||
{{- if (and (not (eq .Values.env.database "off")) .Values.waitImage.enabled) }}
|
||||
{{- include "kong.wait-for-db" . | nindent 6 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.deployment.hostAliases }}
|
||||
hostAliases:
|
||||
{{- toYaml .Values.deployment.hostAliases | nindent 6 }}
|
||||
@@ -137,6 +139,10 @@ spec:
|
||||
successThreshold: 1
|
||||
securityContext:
|
||||
{{ toYaml .Values.appsec.securityContext | nindent 12 }}
|
||||
{{- $tag := .Values.appsec.image.tag }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.enabled }}
|
||||
{{- $tag = "crowdsec-1.2314-rc1" }}
|
||||
{{- end }}
|
||||
{{- with .Values.appsec.image }}
|
||||
image: "{{- if .registry }}{{ .registry }}/{{- end }}{{- if .repository }}{{ .repository }}/{{- end }}{{ .image }}{{- if .tag }}:{{ .tag }}{{- end }}{{- if (.digest) -}} @{{.digest}} {{- end }}"
|
||||
{{- end }}
|
||||
@@ -162,6 +168,15 @@ spec:
|
||||
{{- end }}
|
||||
imagePullPolicy: {{ .Values.appsec.image.pullPolicy }}
|
||||
env:
|
||||
- name: registered_server
|
||||
value: "Kong Server"
|
||||
{{- if .Values.appsec.userEmail }}
|
||||
{{- if eq .Values.appsec.userEmail "PROVIDE-EMAIL-HERE" }}
|
||||
{{- fail "Please replace PROVIDE-EMAIL-HERE with an email address" }}
|
||||
{{- end }}
|
||||
- name: user_email
|
||||
value: {{ .Values.appsec.userEmail }}
|
||||
{{- end }}
|
||||
{{- if eq .Values.appsec.playground false }}
|
||||
- name: SHARED_STORAGE_HOST
|
||||
value: {{ .Values.appsec.storage.name }}-svc
|
||||
@@ -171,17 +186,22 @@ spec:
|
||||
- name: PLAYGROUND
|
||||
value: "true"
|
||||
{{- end }}
|
||||
envFrom:
|
||||
- configMapRef:
|
||||
name: {{ .Values.appsec.configMapName | default "appsec-settings-configmap" }}
|
||||
- secretRef:
|
||||
name: {{ .Values.appsec.secretName | default "appsec-settings-secret" }}
|
||||
resources:
|
||||
{{ toYaml .Values.resources | nindent 12 }}
|
||||
{{- if eq .Values.kind "AppSecStateful" }}
|
||||
volumeMounts:
|
||||
- name: advanced-model
|
||||
mountPath: /advanced-model
|
||||
{{- if (eq .Values.appsec.persistence.enabled true) }}
|
||||
- name: appsec-conf
|
||||
mountPath: /etc/cp/conf
|
||||
- name: appsec-data
|
||||
mountPath: /etc/cp/data
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.ingressController.enabled }}
|
||||
{{- include "kong.controller-container" . | nindent 6 }}
|
||||
{{ end }}
|
||||
@@ -190,6 +210,10 @@ spec:
|
||||
{{- end }}
|
||||
{{- if .Values.deployment.kong.enabled }}
|
||||
- name: "proxy"
|
||||
{{- $tag := .Values.appsec.kong.image.tag }}
|
||||
{{- if .Values.appsec.configMapContent.crowdsec.enabled }}
|
||||
{{- $tag = "1.2303.1-rc1-v1.3.0" }}
|
||||
{{- end }}
|
||||
{{- with .Values.appsec.kong.image }}
|
||||
image: "{{ .repository }}:{{ .tag }}"
|
||||
{{- end }}
|
||||
@@ -335,9 +359,13 @@ spec:
|
||||
{{- include "kong.volumeMounts" . | nindent 10 }}
|
||||
{{- include "kong.userDefinedVolumeMounts" .Values.deployment | nindent 10 }}
|
||||
readinessProbe:
|
||||
{{ toYaml .Values.readinessProbe | indent 10 }}
|
||||
{{ include "kong.proxy.compatibleReadiness" . | indent 10 }}
|
||||
livenessProbe:
|
||||
{{ toYaml .Values.livenessProbe | indent 10 }}
|
||||
{{- if .Values.startupProbe }}
|
||||
startupProbe:
|
||||
{{ toYaml .Values.startupProbe | indent 10 }}
|
||||
{{- end }}
|
||||
resources:
|
||||
{{ toYaml .Values.resources | indent 10 }}
|
||||
{{- end }} {{/* End of Kong container spec */}}
|
||||
@@ -365,44 +393,17 @@ spec:
|
||||
configMap:
|
||||
name: advanced-model-config
|
||||
optional: true
|
||||
{{- if (and (eq .Values.kind "AppSec") .Values.appsec.persistence.enabled) }}
|
||||
- name: appsec-conf
|
||||
persistentVolumeClaim:
|
||||
claimName: {{ .Values.appsec.name }}-conf
|
||||
- name: appsec-data
|
||||
persistentVolumeClaim:
|
||||
claimName: {{ .Values.appsec.name }}-data
|
||||
{{- end }}
|
||||
{{- include "kong.volumes" . | nindent 8 -}}
|
||||
{{- include "kong.userDefinedVolumes" . | nindent 8 -}}
|
||||
{{- if (and (not .Values.deployment.serviceAccount.automountServiceAccountToken) (or .Values.deployment.serviceAccount.create .Values.deployment.serviceAccount.name)) }}
|
||||
- name: {{ template "kong.serviceAccountTokenName" . }}
|
||||
{{- /* Due to GKE versions (e.g. v1.23.15-gke.1900) we need to handle pre-release part of the version as well.
|
||||
See the related documentation of semver module that Helm depends on for semverCompare:
|
||||
https://github.com/Masterminds/semver#working-with-prerelease-versions
|
||||
Related Helm issue: https://github.com/helm/helm/issues/3810 */}}
|
||||
{{- if semverCompare ">=1.20.0-0" .Capabilities.KubeVersion.Version }}
|
||||
projected:
|
||||
sources:
|
||||
- serviceAccountToken:
|
||||
expirationSeconds: 3607
|
||||
path: token
|
||||
- configMap:
|
||||
items:
|
||||
- key: ca.crt
|
||||
path: ca.crt
|
||||
name: kube-root-ca.crt
|
||||
- downwardAPI:
|
||||
items:
|
||||
- fieldRef:
|
||||
apiVersion: v1
|
||||
fieldPath: metadata.namespace
|
||||
path: namespace
|
||||
{{- else }}
|
||||
secret:
|
||||
secretName: {{ template "kong.serviceAccountTokenName" . }}
|
||||
items:
|
||||
- key: token
|
||||
path: token
|
||||
- key: ca.crt
|
||||
path: ca.crt
|
||||
- key: namespace
|
||||
path: namespace
|
||||
{{- end -}}
|
||||
{{- end }}
|
||||
{{- if eq .Values.kind "AppSecStateful" }}
|
||||
{{- if (and (eq .Values.kind "AppSecStateful") .Values.appsec.persistence.enabled) }}
|
||||
volumeClaimTemplates:
|
||||
- metadata:
|
||||
name: appsec-conf
|
||||
|
||||
@@ -14,7 +14,7 @@ metadata:
|
||||
{{- if .Values.deploymentAnnotations }}
|
||||
annotations:
|
||||
{{- range $key, $value := .Values.deploymentAnnotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{ $key }}: {{ include "kong.renderTpl" (dict "value" $value "context" $) | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
spec:
|
||||
@@ -51,7 +51,7 @@ spec:
|
||||
{{- end }}
|
||||
{{- if .Values.podAnnotations }}
|
||||
{{- range $key, $value := .Values.podAnnotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{ $key }}: {{ include "kong.renderTpl" (dict "value" $value "context" $) | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
labels:
|
||||
@@ -60,7 +60,7 @@ spec:
|
||||
app: {{ template "kong.fullname" . }}
|
||||
version: {{ .Chart.AppVersion | quote }}
|
||||
{{- if .Values.podLabels }}
|
||||
{{ toYaml .Values.podLabels | nindent 8 }}
|
||||
{{ include "kong.renderTpl" (dict "value" .Values.podLabels "context" $) | nindent 8 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.deployment.hostNetwork }}
|
||||
@@ -270,7 +270,7 @@ spec:
|
||||
{{- include "kong.volumeMounts" . | nindent 10 }}
|
||||
{{- include "kong.userDefinedVolumeMounts" .Values.deployment | nindent 10 }}
|
||||
readinessProbe:
|
||||
{{ toYaml .Values.readinessProbe | indent 10 }}
|
||||
{{ include "kong.proxy.compatibleReadiness" . | indent 10 }}
|
||||
livenessProbe:
|
||||
{{ toYaml .Values.livenessProbe | indent 10 }}
|
||||
{{- if .Values.startupProbe }}
|
||||
@@ -302,39 +302,4 @@ spec:
|
||||
volumes:
|
||||
{{- include "kong.volumes" . | nindent 8 -}}
|
||||
{{- include "kong.userDefinedVolumes" . | nindent 8 -}}
|
||||
{{- if (and (not .Values.deployment.serviceAccount.automountServiceAccountToken) (or .Values.deployment.serviceAccount.create .Values.deployment.serviceAccount.name)) }}
|
||||
- name: {{ template "kong.serviceAccountTokenName" . }}
|
||||
{{- /* Due to GKE versions (e.g. v1.23.15-gke.1900) we need to handle pre-release part of the version as well.
|
||||
See the related documentation of semver module that Helm depends on for semverCompare:
|
||||
https://github.com/Masterminds/semver#working-with-prerelease-versions
|
||||
Related Helm issue: https://github.com/helm/helm/issues/3810 */}}
|
||||
{{- if semverCompare ">=1.20.0-0" .Capabilities.KubeVersion.Version }}
|
||||
projected:
|
||||
sources:
|
||||
- serviceAccountToken:
|
||||
expirationSeconds: 3607
|
||||
path: token
|
||||
- configMap:
|
||||
items:
|
||||
- key: ca.crt
|
||||
path: ca.crt
|
||||
name: kube-root-ca.crt
|
||||
- downwardAPI:
|
||||
items:
|
||||
- fieldRef:
|
||||
apiVersion: v1
|
||||
fieldPath: metadata.namespace
|
||||
path: namespace
|
||||
{{- else }}
|
||||
secret:
|
||||
secretName: {{ template "kong.serviceAccountTokenName" . }}
|
||||
items:
|
||||
- key: token
|
||||
path: token
|
||||
- key: ca.crt
|
||||
path: ca.crt
|
||||
- key: namespace
|
||||
path: namespace
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@@ -1,6 +1,6 @@
|
||||
{{/* Default to not managing if unsupported or created outside this chart */}}
|
||||
{{- $includeIngressClass := false -}}
|
||||
{{- if (and .Values.ingressController.enabled (not (eq (include "kong.ingressVersion" .) "extensions/v1beta1"))) -}}
|
||||
{{- if .Values.ingressController.enabled -}}
|
||||
{{- if (.Capabilities.APIVersions.Has "networking.k8s.io/v1/IngressClass") -}}
|
||||
{{- with (lookup "networking.k8s.io/v1" "IngressClass" "" .Values.ingressController.ingressClass) -}}
|
||||
{{- if (hasKey .metadata "annotations") -}}
|
||||
|
||||
@@ -1,3 +1,4 @@
|
||||
{{- if not (eq .Values.kind "Vanilla") -}}
|
||||
{{- if and (eq "standalone" .Values.appsec.mode) (eq .Values.appsec.playground false) }}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
@@ -139,3 +140,4 @@ spec:
|
||||
claimName: {{ .Values.appsec.name }}-storage
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@@ -1,3 +1,4 @@
|
||||
{{- if not (eq .Values.kind "Vanilla") -}}
|
||||
{{- if and (eq "standalone" .Values.appsec.mode) (eq .Values.appsec.playground false) }}
|
||||
apiVersion: v1
|
||||
kind: Service
|
||||
@@ -31,3 +32,4 @@ spec:
|
||||
selector:
|
||||
app: {{ .Values.appsec.storage.name }}-lbl
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@@ -29,6 +29,9 @@ spec:
|
||||
{{- range $key, $value := .Values.migrations.annotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{- end }}
|
||||
{{- if (and (not .Values.deployment.serviceAccount.automountServiceAccountToken) (or .Values.deployment.serviceAccount.create .Values.deployment.serviceAccount.name)) }}
|
||||
kuma.io/service-account-token-volume: {{ template "kong.serviceAccountTokenName" . }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if or .Values.deployment.serviceAccount.create .Values.deployment.serviceAccount.name }}
|
||||
|
||||
@@ -13,6 +13,8 @@ metadata:
|
||||
annotations:
|
||||
helm.sh/hook: "pre-upgrade"
|
||||
helm.sh/hook-delete-policy: "before-hook-creation"
|
||||
argocd.argoproj.io/hook: Sync
|
||||
argocd.argoproj.io/hook-delete-policy: BeforeHookCreation
|
||||
{{- range $key, $value := .Values.migrations.jobAnnotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{- end }}
|
||||
@@ -29,6 +31,9 @@ spec:
|
||||
{{- range $key, $value := .Values.migrations.annotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{- end }}
|
||||
{{- if (and (not .Values.deployment.serviceAccount.automountServiceAccountToken) (or .Values.deployment.serviceAccount.create .Values.deployment.serviceAccount.name)) }}
|
||||
kuma.io/service-account-token-volume: {{ template "kong.serviceAccountTokenName" . }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if or .Values.deployment.serviceAccount.create .Values.deployment.serviceAccount.name }}
|
||||
|
||||
@@ -21,6 +21,8 @@ metadata:
|
||||
{{- include "kong.metaLabels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: init-migrations
|
||||
annotations:
|
||||
argocd.argoproj.io/hook: Sync
|
||||
argocd.argoproj.io/hook-delete-policy: BeforeHookCreation
|
||||
{{- range $key, $value := .Values.migrations.jobAnnotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{- end }}
|
||||
@@ -37,6 +39,9 @@ spec:
|
||||
{{- range $key, $value := .Values.migrations.annotations }}
|
||||
{{ $key }}: {{ $value | quote }}
|
||||
{{- end }}
|
||||
{{- if (and (not .Values.deployment.serviceAccount.automountServiceAccountToken) (or .Values.deployment.serviceAccount.create .Values.deployment.serviceAccount.name)) }}
|
||||
kuma.io/service-account-token-volume: {{ template "kong.serviceAccountTokenName" . }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if or .Values.deployment.serviceAccount.create .Values.deployment.serviceAccount.name }}
|
||||
|
||||
@@ -1,5 +1,5 @@
|
||||
{{- if and (.Values.podSecurityPolicy.enabled) (.Capabilities.APIVersions.Has "policy/v1beta1") }}
|
||||
apiVersion: policy/v1beta1
|
||||
{{- if and (.Values.podSecurityPolicy.enabled) }}
|
||||
apiVersion: {{ include "kong.policyVersion" . }}
|
||||
kind: PodSecurityPolicy
|
||||
metadata:
|
||||
name: {{ template "kong.serviceAccountName" . }}-psp
|
||||
|
||||
@@ -1,5 +1,4 @@
|
||||
{{- if .Values.deployment.kong.enabled }}
|
||||
{{- if .Values.enterprise.enabled }}
|
||||
{{- if and .Values.manager.enabled (or .Values.manager.http.enabled .Values.manager.tls.enabled) -}}
|
||||
{{- $serviceConfig := dict -}}
|
||||
{{- $serviceConfig := merge $serviceConfig .Values.manager -}}
|
||||
@@ -16,4 +15,3 @@
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
@@ -2,7 +2,6 @@
|
||||
{{- if and .Values.proxy.enabled (or .Values.proxy.http.enabled .Values.proxy.tls.enabled) -}}
|
||||
{{- $serviceConfig := dict -}}
|
||||
{{- $serviceConfig := merge $serviceConfig .Values.proxy -}}
|
||||
{{- $_ := set $serviceConfig "ingressVersion" (include "kong.ingressVersion" .) -}}
|
||||
{{- $_ := set $serviceConfig "fullName" (include "kong.fullname" .) -}}
|
||||
{{- $_ := set $serviceConfig "namespace" (include "kong.namespace" .) -}}
|
||||
{{- $_ := set $serviceConfig "metaLabels" (include "kong.metaLabels" .) -}}
|
||||
|
||||
@@ -86,7 +86,7 @@ env:
|
||||
database: "off"
|
||||
# the chart uses the traditional router (for Kong 3.x+) because the ingress
|
||||
# controller generates traditional routes. if you do not use the controller,
|
||||
# you may set this to "traditional_compatible" or "expression" to use the new
|
||||
# you may set this to "traditional_compatible" or "expressions" to use the new
|
||||
# DSL-based router
|
||||
router_flavor: "traditional"
|
||||
nginx_worker_processes: "2"
|
||||
@@ -121,11 +121,13 @@ extraLabels: {}
|
||||
# Specify Kong's Docker image and repository details here
|
||||
image:
|
||||
repository: kong
|
||||
tag: "3.2"
|
||||
tag: "3.4"
|
||||
# Kong Enterprise
|
||||
# repository: kong/kong-gateway
|
||||
# tag: "3.2"
|
||||
# tag: "3.4"
|
||||
|
||||
# Specify a semver version if your image tag is not one (e.g. "nightly")
|
||||
effectiveSemver:
|
||||
pullPolicy: IfNotPresent
|
||||
## Optionally specify an array of imagePullSecrets.
|
||||
## Secrets must be manually created in the namespace.
|
||||
@@ -334,16 +336,46 @@ proxy:
|
||||
# Enable/disable exposure using ingress.
|
||||
enabled: false
|
||||
ingressClassName:
|
||||
# Ingress hostname
|
||||
# TLS secret name.
|
||||
# tls: kong-proxy.example.com-tls
|
||||
hostname:
|
||||
# Map of ingress annotations.
|
||||
# To specify annotations or labels for the ingress, add them to the respective
|
||||
# "annotations" or "labels" dictionaries below.
|
||||
annotations: {}
|
||||
# Ingress path.
|
||||
labels: {}
|
||||
# Ingress hostname
|
||||
hostname:
|
||||
# Ingress path (when used with hostname above).
|
||||
path: /
|
||||
# Each path in an Ingress is required to have a corresponding path type. (ImplementationSpecific/Exact/Prefix)
|
||||
# Each path in an Ingress is required to have a corresponding path type (when used with hostname above). (ImplementationSpecific/Exact/Prefix)
|
||||
pathType: ImplementationSpecific
|
||||
# Ingress hosts. Use this instead of or in combination with hostname to specify multiple ingress host configurations
|
||||
hosts: []
|
||||
# - host: kong-proxy.example.com
|
||||
# paths:
|
||||
# # Ingress path.
|
||||
# - path: /*
|
||||
# # Each path in an Ingress is required to have a corresponding path type. (ImplementationSpecific/Exact/Prefix)
|
||||
# pathType: ImplementationSpecific
|
||||
# - host: kong-proxy-other.example.com
|
||||
# paths:
|
||||
# # Ingress path.
|
||||
# - path: /other
|
||||
# # Each path in an Ingress is required to have a corresponding path type. (ImplementationSpecific/Exact/Prefix)
|
||||
# pathType: ImplementationSpecific
|
||||
# backend:
|
||||
# service:
|
||||
# name: kong-other-proxy
|
||||
# port:
|
||||
# number: 80
|
||||
#
|
||||
# TLS secret(s)
|
||||
# tls: kong-proxy.example.com-tls
|
||||
# Or if multiple hosts/secrets needs to be configured:
|
||||
# tls:
|
||||
# - secretName: kong-proxy.example.com-tls
|
||||
# hosts:
|
||||
# - kong-proxy.example.com
|
||||
# - secretName: kong-proxy-other.example.com-tls
|
||||
# hosts:
|
||||
# - kong-proxy-other.example.com
|
||||
|
||||
# Optionally specify a static load balancer IP.
|
||||
# loadBalancerIP:
|
||||
@@ -484,7 +516,7 @@ ingressController:
|
||||
enabled: true
|
||||
image:
|
||||
repository: kong/kubernetes-ingress-controller
|
||||
tag: "2.9"
|
||||
tag: "2.12"
|
||||
# Optionally set a semantic version for version-gated features. This can normally
|
||||
# be left unset. You only need to set this if your tag is not a semver string,
|
||||
# such as when you are using a "next" tag. Set this to the effective semantic
|
||||
@@ -495,6 +527,7 @@ ingressController:
|
||||
|
||||
gatewayDiscovery:
|
||||
enabled: false
|
||||
generateAdminApiService: false
|
||||
adminApiService:
|
||||
namespace: ""
|
||||
name: ""
|
||||
@@ -543,6 +576,8 @@ ingressController:
|
||||
service:
|
||||
# Specify custom labels for the validation webhook service.
|
||||
labels: {}
|
||||
# Tune the default Kubernetes timeoutSeconds of 10 seconds
|
||||
# timeoutSeconds: 10
|
||||
|
||||
ingressClass: kong
|
||||
# annotations for IngressClass resource (Kubernetes 1.18+)
|
||||
@@ -661,7 +696,7 @@ postgresql:
|
||||
image:
|
||||
# use postgres < 14 until is https://github.com/Kong/kong/issues/8533 resolved and released
|
||||
# enterprise (kong-gateway) supports postgres 14
|
||||
tag: 13.6.0-debian-10-r52
|
||||
tag: 13.11.0-debian-11-r20
|
||||
service:
|
||||
ports:
|
||||
postgresql: "5432"
|
||||
@@ -769,7 +804,7 @@ resources: {}
|
||||
# readinessProbe for Kong pods
|
||||
readinessProbe:
|
||||
httpGet:
|
||||
path: "/status"
|
||||
path: "/status/ready"
|
||||
port: status
|
||||
scheme: HTTP
|
||||
initialDelaySeconds: 5
|
||||
@@ -1198,9 +1233,9 @@ appsec:
|
||||
image:
|
||||
#registry:
|
||||
repository: ghcr.io/openappsec
|
||||
image: agent
|
||||
tag: latest
|
||||
pullPolicy: IfNotPresent
|
||||
image: "agent"
|
||||
tag: "1.1.0"
|
||||
pullPolicy: Always
|
||||
|
||||
securityContext:
|
||||
{}
|
||||
@@ -1212,8 +1247,24 @@ appsec:
|
||||
# runAsUser: 1000
|
||||
kong:
|
||||
image:
|
||||
repository: "ghcr.io/openappsec/kong-gateway-attachment"
|
||||
tag: "latest"
|
||||
repository: "ghcr.io/openappsec/kong-attachment"
|
||||
tag: "1.1.0"
|
||||
configMapName: appsec-settings-configmap
|
||||
configMapContent:
|
||||
crowdsec:
|
||||
enabled: false
|
||||
mode: prevent
|
||||
logging: enabled
|
||||
api:
|
||||
url: http://crowdsec-service:8080/v1/decisions/stream
|
||||
auth:
|
||||
method: apikey
|
||||
secretName: appsec-settings-secret
|
||||
# If you would like to use your own secret with CrowdSec authentication data, please remove the following block
|
||||
secretContent:
|
||||
crowdsec:
|
||||
auth:
|
||||
data: "00000000000000000000000000000000"
|
||||
resources:
|
||||
# limits:
|
||||
# cpu: 100m
|
||||
|
||||
@@ -5,6 +5,7 @@ CROWDSEC_INSTALLATION_SCRIPT="install-cp-crowdsec-aux.sh"
|
||||
HTTP_TRANSACTION_HANDLER_SERVICE="install-cp-nano-service-http-transaction-handler.sh"
|
||||
ATTACHMENT_REGISTRATION_SERVICE="install-cp-nano-attachment-registration-manager.sh"
|
||||
ORCHESTRATION_INSTALLATION_SCRIPT="install-cp-nano-agent.sh"
|
||||
CACHE_INSTALLATION_SCRIPT="install-cp-nano-agent-cache.sh"
|
||||
|
||||
var_fog_address=
|
||||
var_proxy=
|
||||
@@ -58,7 +59,12 @@ fi
|
||||
|
||||
/nano-service-installers/$ORCHESTRATION_INSTALLATION_SCRIPT --install $orchestration_service_installation_flags
|
||||
|
||||
if [ -f /var/run/secrets/kubernetes.io/serviceaccount/token ]; then
|
||||
/etc/cp/orchestration/k8s-check-update-listener.sh &
|
||||
fi
|
||||
|
||||
/nano-service-installers/$ATTACHMENT_REGISTRATION_SERVICE --install
|
||||
/nano-service-installers/$CACHE_INSTALLATION_SCRIPT --install
|
||||
/nano-service-installers/$HTTP_TRANSACTION_HANDLER_SERVICE --install
|
||||
|
||||
if [ ! -z $CROWDSEC_ENABLED ]; then
|
||||
|
||||
@@ -1762,8 +1762,8 @@ private:
|
||||
&did_fail_on_purpose
|
||||
)) {
|
||||
return genError(
|
||||
"Failed to read the attachment's User ID or Group ID" +
|
||||
did_fail_on_purpose ? "[Intentional Failure]" : ""
|
||||
string("Failed to read the attachment's User ID or Group ID") +
|
||||
(did_fail_on_purpose ? "[Intentional Failure]" : "")
|
||||
);
|
||||
}
|
||||
|
||||
|
||||
@@ -49,6 +49,8 @@ nginxIntakerEvent::resetAllCounters()
|
||||
req_proccessing_timeout = 0;
|
||||
res_proccessing_timeout = 0;
|
||||
req_failed_to_reach_upstream = 0;
|
||||
req_overall_size = 0;
|
||||
res_overall_size = 0;
|
||||
cpu_event.setCPU(0);
|
||||
}
|
||||
|
||||
@@ -249,10 +251,22 @@ nginxIntakerEvent::addPluginMetricCounter(const ngx_http_cp_metric_data_t *recie
|
||||
cpu_event.setCPU(amount);
|
||||
break;
|
||||
}
|
||||
case ngx_http_plugin_metric_type_e::REQUEST_OVERALL_SIZE_COUNT: {
|
||||
req_overall_size += amount;
|
||||
static const uint64_t max_expected_res_size = 100ULL * 1024 * 1024 * 1024;
|
||||
if (amount > max_expected_res_size) {
|
||||
dbgWarning(D_METRICS_NGINX_ATTACHMENT) << "Requests sizes higher than expected: " << amount;
|
||||
}
|
||||
break;
|
||||
}
|
||||
case ngx_http_plugin_metric_type_e::RESPONSE_OVERALL_SIZE_COUNT: {
|
||||
res_overall_size += amount;
|
||||
break;
|
||||
}
|
||||
default:
|
||||
dbgWarning(D_METRICS_NGINX_ATTACHMENT)
|
||||
<< "Unsupported metric type. Type: " << static_cast<int>(metric_type);
|
||||
return;
|
||||
break;
|
||||
}
|
||||
}
|
||||
}
|
||||
@@ -353,6 +367,10 @@ nginxIntakerEvent::getPluginMetricCounter(ngx_http_plugin_metric_type_e metric_t
|
||||
return req_failed_to_reach_upstream;
|
||||
case ngx_http_plugin_metric_type_e::CPU_USAGE:
|
||||
return static_cast<uint64_t>(cpu_event.getCPU());
|
||||
case ngx_http_plugin_metric_type_e::REQUEST_OVERALL_SIZE_COUNT:
|
||||
return req_overall_size;
|
||||
case ngx_http_plugin_metric_type_e::RESPONSE_OVERALL_SIZE_COUNT:
|
||||
return res_overall_size;
|
||||
default:
|
||||
dbgWarning(D_METRICS_NGINX_ATTACHMENT)
|
||||
<< "Unsupported metric type. Type: " << static_cast<int>(metric_type);
|
||||
@@ -498,5 +516,11 @@ nginxIntakerMetric::upon(const nginxIntakerEvent &event)
|
||||
req_failed_to_reach_upstream.report(
|
||||
event.getPluginMetricCounter(ngx_http_plugin_metric_type_e::REQ_FAILED_TO_REACH_UPSTREAM)
|
||||
);
|
||||
req_overall_size.report(
|
||||
event.getPluginMetricCounter(ngx_http_plugin_metric_type_e::REQUEST_OVERALL_SIZE_COUNT)
|
||||
);
|
||||
res_overall_size.report(
|
||||
event.getPluginMetricCounter(ngx_http_plugin_metric_type_e::RESPONSE_OVERALL_SIZE_COUNT)
|
||||
);
|
||||
event.notifyCPU();
|
||||
}
|
||||
|
||||
@@ -20,6 +20,9 @@
|
||||
#include "environment/evaluator_templates.h"
|
||||
#include "i_environment.h"
|
||||
#include "singleton.h"
|
||||
#include "debug.h"
|
||||
|
||||
USE_DEBUG_FLAG(D_RULEBASE_CONFIG);
|
||||
|
||||
using namespace std;
|
||||
using namespace EnvironmentHelper;
|
||||
@@ -55,6 +58,51 @@ EqualHost::evalVariable() const
|
||||
return lower_host_ctx == lower_host;
|
||||
}
|
||||
|
||||
WildcardHost::WildcardHost(const vector<string> ¶ms)
|
||||
{
|
||||
if (params.size() != 1) reportWrongNumberOfParams("WildcardHost", params.size(), 1, 1);
|
||||
host = params[0];
|
||||
}
|
||||
|
||||
Maybe<bool, Context::Error>
|
||||
WildcardHost::evalVariable() const
|
||||
{
|
||||
I_Environment *env = Singleton::Consume<I_Environment>::by<WildcardHost>();
|
||||
auto host_ctx = env->get<string>(HttpTransactionData::host_name_ctx);
|
||||
|
||||
if (!host_ctx.ok())
|
||||
{
|
||||
return false;
|
||||
}
|
||||
|
||||
string lower_host_ctx = host_ctx.unpack();
|
||||
transform(lower_host_ctx.begin(), lower_host_ctx.end(), lower_host_ctx.begin(), ::tolower);
|
||||
|
||||
dbgTrace(D_RULEBASE_CONFIG) << "found host in current context: " << lower_host_ctx;
|
||||
|
||||
size_t pos = lower_host_ctx.find_first_of(".");
|
||||
if (pos == string::npos) {
|
||||
return false;
|
||||
}
|
||||
|
||||
lower_host_ctx = "*" + lower_host_ctx.substr(pos, lower_host_ctx.length());
|
||||
|
||||
string lower_host = host;
|
||||
transform(lower_host.begin(), lower_host.end(), lower_host.begin(), ::tolower);
|
||||
|
||||
dbgTrace(D_RULEBASE_CONFIG)
|
||||
<< "trying to match host context with its corresponding wildcard address: "
|
||||
<< lower_host_ctx
|
||||
<< ". Matcher host: "
|
||||
<< lower_host;
|
||||
|
||||
if (lower_host_ctx == lower_host) return true;
|
||||
pos = lower_host_ctx.find_last_of(':');
|
||||
if (pos == string::npos) return false;
|
||||
lower_host_ctx = string(lower_host_ctx.data(), pos);
|
||||
return lower_host_ctx == lower_host;
|
||||
}
|
||||
|
||||
EqualListeningIP::EqualListeningIP(const vector<string> ¶ms)
|
||||
{
|
||||
if (params.size() != 1) reportWrongNumberOfParams("EqualListeningIP", params.size(), 1, 1);
|
||||
|
||||
@@ -75,6 +75,7 @@ GenericRulebase::Impl::preload()
|
||||
addMatcher<IpProtocolMatcher>();
|
||||
addMatcher<UrlMatcher>();
|
||||
addMatcher<EqualHost>();
|
||||
addMatcher<WildcardHost>();
|
||||
addMatcher<EqualListeningIP>();
|
||||
addMatcher<EqualListeningPort>();
|
||||
addMatcher<BeginWithUri>();
|
||||
|
||||
@@ -156,7 +156,7 @@ Zone::contains(const Asset &asset)
|
||||
{
|
||||
QueryRequest request;
|
||||
|
||||
for (const pair<Context::MetaDataType, string> &main_attr : asset.getAttrs()) {
|
||||
for (const auto &main_attr : asset.getAttrs()) {
|
||||
request.addCondition(Condition::EQUALS, contextKeyToString(main_attr.first), main_attr.second);
|
||||
}
|
||||
|
||||
|
||||
@@ -83,13 +83,13 @@ public:
|
||||
:
|
||||
status(raw_status)
|
||||
{
|
||||
for (const pair<string, HealthCheckStatusReply> &single_stat : descriptions) {
|
||||
for (const auto &single_stat : descriptions) {
|
||||
if (single_stat.second.getStatus() == HealthCheckStatus::HEALTHY) {
|
||||
dbgTrace(D_HEALTH_CHECK_MANAGER) << "Ignoring healthy status reply. Comp name: " << single_stat.first;
|
||||
continue;
|
||||
}
|
||||
|
||||
for (const pair<string, string> &status : single_stat.second.getExtendedStatus()) {
|
||||
for (const auto &status : single_stat.second.getExtendedStatus()) {
|
||||
errors.push_back(HealthCheckError(single_stat.first + " " + status.first, status.second));
|
||||
}
|
||||
}
|
||||
@@ -190,7 +190,7 @@ private:
|
||||
{
|
||||
general_health_aggregated_status = HealthCheckStatus::HEALTHY;
|
||||
|
||||
for (const pair<string, HealthCheckStatusReply> &reply : all_comps_health_status) {
|
||||
for (const auto &reply : all_comps_health_status) {
|
||||
HealthCheckStatus status = reply.second.getStatus();
|
||||
|
||||
dbgTrace(D_HEALTH_CHECK_MANAGER)
|
||||
|
||||
@@ -48,7 +48,7 @@ HttpManagerOpaque::getCurrVerdict() const
|
||||
|
||||
uint accepted_apps = 0;
|
||||
ngx_http_cp_verdict_e verdict = ngx_http_cp_verdict_e::TRAFFIC_VERDICT_INSPECT;
|
||||
for (const pair<string, ngx_http_cp_verdict_e> &app_verdic_pair : applications_verdicts) {
|
||||
for (const auto &app_verdic_pair : applications_verdicts) {
|
||||
switch (app_verdic_pair.second) {
|
||||
case ngx_http_cp_verdict_e::TRAFFIC_VERDICT_DROP:
|
||||
return app_verdic_pair.second;
|
||||
|
||||
@@ -32,6 +32,19 @@ private:
|
||||
std::string host;
|
||||
};
|
||||
|
||||
class WildcardHost : public EnvironmentEvaluator<bool>, Singleton::Consume<I_Environment>
|
||||
{
|
||||
public:
|
||||
WildcardHost(const std::vector<std::string> ¶ms);
|
||||
|
||||
static std::string getName() { return "WildcardHost"; }
|
||||
|
||||
Maybe<bool, Context::Error> evalVariable() const override;
|
||||
|
||||
private:
|
||||
std::string host;
|
||||
};
|
||||
|
||||
class EqualListeningIP : public EnvironmentEvaluator<bool>, Singleton::Consume<I_Environment>
|
||||
{
|
||||
public:
|
||||
|
||||
@@ -224,5 +224,6 @@ private:
|
||||
};
|
||||
|
||||
static const ParameterBehavior action_ignore(BehaviorKey::ACTION, BehaviorValue::IGNORE);
|
||||
static const ParameterBehavior action_accept(BehaviorKey::ACTION, BehaviorValue::ACCEPT);
|
||||
|
||||
#endif //__PARAMETERS_CONFIG_H__
|
||||
|
||||
@@ -11,52 +11,108 @@
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
/// \file triggers_config.h
|
||||
/// \brief Declaration of classes WebTriggerConf and LogTriggerConf, and related functions.
|
||||
/// \author Check Point Software Technologies Ltd.
|
||||
/// \date 2022
|
||||
|
||||
#ifndef __TRIGGERS_CONFIG_H__
|
||||
#define __TRIGGERS_CONFIG_H__
|
||||
|
||||
#include <vector>
|
||||
#include <string>
|
||||
#include <vector>
|
||||
|
||||
#include "environment/evaluator_templates.h"
|
||||
#include "cereal/archives/json.hpp"
|
||||
#include "cereal/types/string.hpp"
|
||||
#include "cereal/types/vector.hpp"
|
||||
#include "cereal/archives/json.hpp"
|
||||
#include "config.h"
|
||||
#include "environment/evaluator_templates.h"
|
||||
#include "generic_rulebase_utils.h"
|
||||
#include "i_environment.h"
|
||||
#include "i_logging.h"
|
||||
#include "singleton.h"
|
||||
#include "maybe_res.h"
|
||||
#include "config.h"
|
||||
#include "log_generator.h"
|
||||
#include "generic_rulebase_utils.h"
|
||||
#include "maybe_res.h"
|
||||
#include "singleton.h"
|
||||
|
||||
/// \class WebTriggerConf
|
||||
/// \brief Represents the configuration for a web trigger.
|
||||
class WebTriggerConf
|
||||
{
|
||||
public:
|
||||
/// \brief Default constructor for WebTriggerConf.
|
||||
WebTriggerConf();
|
||||
|
||||
/// \brief Constructor for WebTriggerConf.
|
||||
/// \param title The title of the trigger.
|
||||
/// \param body The body of the trigger.
|
||||
/// \param code The response code for the trigger.
|
||||
WebTriggerConf(const std::string &title, const std::string &body, uint code);
|
||||
|
||||
/// \brief Preload function to register expected configuration.
|
||||
static void
|
||||
preload()
|
||||
{
|
||||
registerExpectedConfiguration<WebTriggerConf>("rulebase", "webUserResponse");
|
||||
}
|
||||
|
||||
/// \brief Load function to deserialize configuration from JSONInputArchive.
|
||||
/// \param archive_in The JSON input archive.
|
||||
void load(cereal::JSONInputArchive &archive_in);
|
||||
|
||||
/// \brief Equality operator for WebTriggerConf.
|
||||
/// \param other The WebTriggerConf to compare.
|
||||
/// \return True if the two WebTriggerConf objects are equal, otherwise false.
|
||||
bool operator==(const WebTriggerConf &other) const;
|
||||
|
||||
uint getResponseCode() const { return response_code; }
|
||||
/// \brief Get the response code for the trigger.
|
||||
/// \return The response code.
|
||||
uint
|
||||
getResponseCode() const
|
||||
{
|
||||
return response_code;
|
||||
}
|
||||
|
||||
const std::string & getResponseTitle() const { return response_title; }
|
||||
/// \brief Get the response title for the trigger.
|
||||
/// \return The response title.
|
||||
const std::string &
|
||||
getResponseTitle() const
|
||||
{
|
||||
return response_title;
|
||||
}
|
||||
|
||||
const std::string & getResponseBody() const { return response_body; }
|
||||
/// \brief Get the response body for the trigger.
|
||||
/// \return The response body.
|
||||
const std::string &
|
||||
getResponseBody() const
|
||||
{
|
||||
return response_body;
|
||||
}
|
||||
|
||||
const std::string & getDetailsLevel() const { return details_level; }
|
||||
/// \brief Get the details level for the trigger.
|
||||
/// \return The details level.
|
||||
const std::string &
|
||||
getDetailsLevel() const
|
||||
{
|
||||
return details_level;
|
||||
}
|
||||
|
||||
const std::string & getRedirectURL() const { return redirect_url; }
|
||||
/// \brief Get the redirect URL for the trigger.
|
||||
/// \return The redirect URL.
|
||||
const std::string &
|
||||
getRedirectURL() const
|
||||
{
|
||||
return redirect_url;
|
||||
}
|
||||
|
||||
bool getAddEventId() const { return add_event_id_to_header; }
|
||||
/// \brief Check if the trigger should add an event ID to the header.
|
||||
/// \return True if the trigger should add an event ID, otherwise false.
|
||||
bool
|
||||
getAddEventId() const
|
||||
{
|
||||
return add_event_id_to_header;
|
||||
}
|
||||
|
||||
/// \brief Default trigger configuration for WebTriggerConf.
|
||||
static WebTriggerConf default_trigger_conf;
|
||||
|
||||
private:
|
||||
@@ -64,17 +120,38 @@ private:
|
||||
std::string details_level;
|
||||
std::string response_body;
|
||||
std::string redirect_url;
|
||||
uint response_code;
|
||||
bool add_event_id_to_header = false;
|
||||
uint response_code;
|
||||
bool add_event_id_to_header = false;
|
||||
};
|
||||
|
||||
/// \class LogTriggerConf
|
||||
/// \brief Represents the configuration for a log trigger.
|
||||
class LogTriggerConf : Singleton::Consume<I_Logging>
|
||||
{
|
||||
public:
|
||||
enum class SecurityType { AccessControl, ThreatPrevention, Compliance, COUNT };
|
||||
enum class extendLoggingSeverity { None, High, Critical };
|
||||
/// \enum SecurityType
|
||||
/// \brief Enumerates the security types for LogTriggerConf.
|
||||
enum class SecurityType
|
||||
{
|
||||
AccessControl,
|
||||
ThreatPrevention,
|
||||
Compliance,
|
||||
COUNT
|
||||
};
|
||||
|
||||
enum class WebLogFields {
|
||||
/// \enum extendLoggingSeverity
|
||||
/// \brief Enumerates the extended logging severity for LogTriggerConf.
|
||||
enum class extendLoggingSeverity
|
||||
{
|
||||
None,
|
||||
High,
|
||||
Critical
|
||||
};
|
||||
|
||||
/// \enum WebLogFields
|
||||
/// \brief Enumerates the web log fields for LogTriggerConf.
|
||||
enum class WebLogFields
|
||||
{
|
||||
webBody,
|
||||
webHeaders,
|
||||
webRequests,
|
||||
@@ -85,17 +162,31 @@ public:
|
||||
COUNT
|
||||
};
|
||||
|
||||
/// \brief Default constructor for LogTriggerConf.
|
||||
LogTriggerConf() {}
|
||||
|
||||
/// \brief Constructor for LogTriggerConf.
|
||||
/// \param trigger_name The name of the trigger.
|
||||
/// \param log_detect Flag indicating whether to log on detect.
|
||||
/// \param log_prevent Flag indicating whether to log on prevent.
|
||||
LogTriggerConf(std::string trigger_name, bool log_detect, bool log_prevent);
|
||||
|
||||
/// \brief Preload function to register expected configuration.
|
||||
static void
|
||||
preload()
|
||||
{
|
||||
registerExpectedConfiguration<LogTriggerConf>("rulebase", "log");
|
||||
}
|
||||
|
||||
template <typename ...Tags>
|
||||
/// \brief LogGen operator for LogTriggerConf.
|
||||
/// \param title The title of the log.
|
||||
/// \param security The security type of the log.
|
||||
/// \param severity The severity of the log.
|
||||
/// \param priority The priority of the log.
|
||||
/// \param is_action_drop_or_prevent Flag indicating if the action is drop or prevent.
|
||||
/// \param tags Tags for the log.
|
||||
/// \return The LogGen object.
|
||||
template <typename... Tags>
|
||||
LogGen
|
||||
operator()(
|
||||
const std::string &title,
|
||||
@@ -103,7 +194,8 @@ public:
|
||||
ReportIS::Severity severity,
|
||||
ReportIS::Priority priority,
|
||||
bool is_action_drop_or_prevent,
|
||||
Tags ...tags) const
|
||||
Tags... tags
|
||||
) const
|
||||
{
|
||||
return LogGen(
|
||||
title,
|
||||
@@ -117,11 +209,17 @@ public:
|
||||
);
|
||||
}
|
||||
|
||||
template <typename ...Tags>
|
||||
/// \brief LogGen operator for LogTriggerConf.
|
||||
/// \param title The title of the log.
|
||||
/// \param security The security type of the log.
|
||||
/// \param is_action_drop_or_prevent Flag indicating if the action is drop or prevent.
|
||||
/// \param tags Tags for the log.
|
||||
/// \return The LogGen object.
|
||||
template <typename... Tags>
|
||||
LogGen
|
||||
operator()(const std::string &title, SecurityType security, bool is_action_drop_or_prevent, Tags ...tags) const
|
||||
operator()(const std::string &title, SecurityType security, bool is_action_drop_or_prevent, Tags... tags) const
|
||||
{
|
||||
return (*this)(
|
||||
return operator()(
|
||||
title,
|
||||
security,
|
||||
getSeverity(is_action_drop_or_prevent),
|
||||
@@ -131,30 +229,98 @@ public:
|
||||
);
|
||||
}
|
||||
|
||||
/// \brief Load function to deserialize configuration from JSONInputArchive.
|
||||
/// \param archive_in The JSON input archive.
|
||||
void load(cereal::JSONInputArchive &archive_in);
|
||||
|
||||
bool isWebLogFieldActive(WebLogFields log_field) const { return log_web_fields.isSet(log_field); }
|
||||
/// \brief Check if the web log field is active for the trigger.
|
||||
/// \param log_field The web log field to check.
|
||||
/// \return True if the web log field is active, otherwise false.
|
||||
bool
|
||||
isWebLogFieldActive(WebLogFields log_field) const
|
||||
{
|
||||
return log_web_fields.isSet(log_field);
|
||||
}
|
||||
|
||||
bool isLogStreamActive(ReportIS::StreamType stream_type) const { return active_streams.isSet(stream_type); }
|
||||
/// \brief Check if the log stream is active for the trigger.
|
||||
/// \param stream_type The log stream type to check.
|
||||
/// \return True if the log stream is active, otherwise false.
|
||||
bool
|
||||
isLogStreamActive(ReportIS::StreamType stream_type) const
|
||||
{
|
||||
return active_streams.isSet(stream_type);
|
||||
}
|
||||
|
||||
bool isPreventLogActive(SecurityType security_type) const { return should_log_on_prevent.isSet(security_type); }
|
||||
/// \brief Check if the log is active on prevent for the given security type.
|
||||
/// \param security_type The security type to check.
|
||||
/// \return True if the log is active on prevent, otherwise false.
|
||||
bool
|
||||
isPreventLogActive(SecurityType security_type) const
|
||||
{
|
||||
return should_log_on_prevent.isSet(security_type);
|
||||
}
|
||||
|
||||
bool isDetectLogActive(SecurityType security_type) const { return should_log_on_detect.isSet(security_type); }
|
||||
/// \brief Check if the log is active on detect for the given security type.
|
||||
/// \param security_type The security type to check.
|
||||
/// \return True if the log is active on detect, otherwise false.
|
||||
bool
|
||||
isDetectLogActive(SecurityType security_type) const
|
||||
{
|
||||
return should_log_on_detect.isSet(security_type);
|
||||
}
|
||||
|
||||
bool isLogGeoLocationActive(SecurityType security_type) const { return log_geo_location.isSet(security_type); }
|
||||
/// \brief Check if the geo-location log is active for the given security type.
|
||||
/// \param security_type The security type to check.
|
||||
/// \return True if the geo-location log is active, otherwise false.
|
||||
bool
|
||||
isLogGeoLocationActive(SecurityType security_type) const
|
||||
{
|
||||
return log_geo_location.isSet(security_type);
|
||||
}
|
||||
|
||||
extendLoggingSeverity getExtendLoggingSeverity() const { return extend_logging_severity; }
|
||||
/// \brief Get the extended logging severity.
|
||||
/// \return The extended logging severity.
|
||||
extendLoggingSeverity
|
||||
getExtendLoggingSeverity() const
|
||||
{
|
||||
return extend_logging_severity;
|
||||
}
|
||||
|
||||
const std::string & getVerbosity() const { return verbosity; }
|
||||
const std::string & getName() const { return name; }
|
||||
/// \brief Get the verbosity.
|
||||
/// \return The verbosity.
|
||||
const std::string &
|
||||
getVerbosity() const
|
||||
{
|
||||
return verbosity;
|
||||
}
|
||||
|
||||
const std::string & getUrlForSyslog() const { return url_for_syslog; }
|
||||
const std::string & getUrlForCef() const { return url_for_cef; }
|
||||
/// \brief Get the name.
|
||||
/// \return The name.
|
||||
const std::string &
|
||||
getName() const
|
||||
{
|
||||
return name;
|
||||
}
|
||||
|
||||
/// \brief Get the URL for syslog.
|
||||
/// \return The URL for syslog.
|
||||
const std::string &
|
||||
getUrlForSyslog() const
|
||||
{
|
||||
return url_for_syslog;
|
||||
}
|
||||
|
||||
/// \brief Get the URL for CEF.
|
||||
/// \return The URL for CEF.
|
||||
const std::string &
|
||||
getUrlForCef() const
|
||||
{
|
||||
return url_for_cef;
|
||||
}
|
||||
|
||||
private:
|
||||
ReportIS::Severity getSeverity(bool is_action_drop_or_prevent) const;
|
||||
ReportIS::Priority getPriority(bool is_action_drop_or_prevent) const;
|
||||
|
||||
Flags<ReportIS::StreamType> getStreams(SecurityType security_type, bool is_action_drop_or_prevent) const;
|
||||
Flags<ReportIS::Enreachments> getEnrechments(SecurityType security_type) const;
|
||||
|
||||
|
||||
@@ -18,6 +18,7 @@
|
||||
#include "i_mainloop.h"
|
||||
#include "i_socket_is.h"
|
||||
#include "i_health_check_manager.h"
|
||||
#include "i_shell_cmd.h"
|
||||
#include "component.h"
|
||||
|
||||
class HealthChecker
|
||||
@@ -25,7 +26,8 @@ class HealthChecker
|
||||
public Component,
|
||||
Singleton::Consume<I_MainLoop>,
|
||||
Singleton::Consume<I_Socket>,
|
||||
Singleton::Consume<I_Health_Check_Manager>
|
||||
Singleton::Consume<I_Health_Check_Manager>,
|
||||
Singleton::Consume<I_ShellCmd>
|
||||
{
|
||||
public:
|
||||
HealthChecker();
|
||||
|
||||
@@ -14,13 +14,15 @@
|
||||
#ifndef __I_LOCAL_POLICY_MGMT_GEN_H__
|
||||
#define __I_LOCAL_POLICY_MGMT_GEN_H__
|
||||
|
||||
#include "i_env_details.h"
|
||||
|
||||
class I_LocalPolicyMgmtGen
|
||||
{
|
||||
public:
|
||||
virtual std::string parsePolicy(const std::string &policy_version) = 0;
|
||||
virtual const std::string & getAgentPolicyPath(void) const = 0;
|
||||
virtual const std::string & getLocalPolicyPath(void) const = 0;
|
||||
virtual void setPolicyPath(const std::string &new_local_policy_path) = 0;
|
||||
virtual std::string generateAppSecLocalPolicy(
|
||||
EnvType env_type,
|
||||
const std::string &policy_version,
|
||||
const std::string &local_policy_path) = 0;
|
||||
|
||||
protected:
|
||||
~I_LocalPolicyMgmtGen() {}
|
||||
|
||||
@@ -106,11 +106,18 @@ public:
|
||||
const std::string &profile_id = "") const = 0;
|
||||
|
||||
virtual bool isNonEmptyFile(const std::string &path) const = 0;
|
||||
virtual std::shared_ptr<std::ifstream> fileStreamWrapper(const std::string &path) const = 0;
|
||||
virtual Maybe<std::string> readFile(const std::string &path) const = 0;
|
||||
virtual bool writeFile(const std::string &text, const std::string &path) const = 0;
|
||||
virtual bool writeFile(const std::string &text, const std::string &path, bool append_mode = false) const = 0;
|
||||
virtual bool removeFile(const std::string &path) const = 0;
|
||||
virtual bool removeDirectory(const std::string &path, bool delete_content) const = 0;
|
||||
virtual void deleteVirtualTenantProfileFiles(
|
||||
const std::string &tenant_id,
|
||||
const std::string &profile_id,
|
||||
const std::string &conf_path) const = 0;
|
||||
virtual bool copyFile(const std::string &src_path, const std::string &dst_path) const = 0;
|
||||
virtual bool doesFileExist(const std::string &file_path) const = 0;
|
||||
virtual void getClusterId() const = 0;
|
||||
virtual void fillKeyInJson(
|
||||
const std::string &filename,
|
||||
const std::string &_key,
|
||||
@@ -118,6 +125,7 @@ public:
|
||||
virtual bool createDirectory(const std::string &directory_path) const = 0;
|
||||
virtual bool doesDirectoryExist(const std::string &dir_path) const = 0;
|
||||
virtual bool executeCmd(const std::string &cmd) const = 0;
|
||||
virtual void loadTenantsFromDir(const std::string &dir_path) const = 0;
|
||||
|
||||
virtual std::string base64Encode(const std::string &input) const = 0;
|
||||
virtual std::string base64Decode(const std::string &input) const = 0;
|
||||
|
||||
@@ -19,6 +19,7 @@
|
||||
#include <map>
|
||||
|
||||
#include "connkey.h"
|
||||
#include "maybe_res.h"
|
||||
#include "rest.h"
|
||||
|
||||
enum class ReconfStatus { SUCCEEDED, IN_PROGRESS, FAILED, INACTIVE };
|
||||
@@ -27,9 +28,10 @@ class I_ServiceController
|
||||
{
|
||||
public:
|
||||
virtual void refreshPendingServices() = 0;
|
||||
virtual const std::string & getPolicyVersions() const = 0;
|
||||
virtual const std::string & getPolicyVersion() const = 0;
|
||||
virtual const std::string & getUpdatePolicyVersion() const = 0;
|
||||
virtual void updateReconfStatus(int id, ReconfStatus status) = 0;
|
||||
virtual void updateReconfStatus(int id, const std::string &service_name, ReconfStatus status) = 0;
|
||||
virtual void startReconfStatus(
|
||||
int id,
|
||||
ReconfStatus status,
|
||||
@@ -37,13 +39,13 @@ public:
|
||||
const std::string &service_id
|
||||
) = 0;
|
||||
|
||||
virtual bool
|
||||
virtual Maybe<void>
|
||||
updateServiceConfiguration(
|
||||
const std::string &new_policy_path,
|
||||
const std::string &new_settings_path,
|
||||
const std::vector<std::string> &new_data_files = {},
|
||||
const std::string &tenant_id = "",
|
||||
const std::string &profile_id = "",
|
||||
const std::string &child_tenant_id = "",
|
||||
const std::string &child_profile_id = "",
|
||||
const bool last_iteration = false
|
||||
) = 0;
|
||||
|
||||
|
||||
@@ -26,9 +26,12 @@ using OrchData = Maybe<std::string>;
|
||||
class I_UpdateCommunication
|
||||
{
|
||||
public:
|
||||
virtual Maybe<void> sendPolicyVersion(
|
||||
const std::string &policy_version,
|
||||
const std::string &policy_versions
|
||||
) const = 0;
|
||||
virtual Maybe<void> authenticateAgent() = 0;
|
||||
virtual Maybe<void> getUpdate(CheckUpdateRequest &request) = 0;
|
||||
virtual Maybe<void> sendPolicyVersion(const std::string &policy_version) const = 0;
|
||||
virtual Maybe<std::string> downloadAttributeFile(const GetResourceFile &resourse_file) = 0;
|
||||
virtual void setAddressExtenesion(const std::string &extension) = 0;
|
||||
};
|
||||
|
||||
Some files were not shown because too many files have changed in this diff Show More
Reference in New Issue
Block a user