mirror of
https://github.com/openappsec/openappsec.git
synced 2025-11-16 17:31:52 +03:00
Compare commits
9 Commits
1.1.29
...
v1beta2-de
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
d9e110292a | ||
|
|
78d1bcf7c4 | ||
|
|
c90862d74c | ||
|
|
b7923dfd8c | ||
|
|
ed4e20b010 | ||
|
|
14159402e2 | ||
|
|
b74957d9d4 | ||
|
|
0c0da6d91b | ||
|
|
ef887dd1c7 |
20
README.md
20
README.md
@@ -6,7 +6,7 @@
|
|||||||
[](https://bestpractices.coreinfrastructure.org/projects/6629)
|
[](https://bestpractices.coreinfrastructure.org/projects/6629)
|
||||||
|
|
||||||
# About
|
# About
|
||||||
[open-appsec](https://www.openappsec.io) (openappsec.io) builds on machine learning to provide preemptive web app & API threat protection against OWASP-Top-10 and zero-day attacks. It can be deployed as an add-on to Kubernetes Ingress, NGINX, Envoy (soon), and API Gateways.
|
[open-appsec](https://www.openappsec.io) (openappsec.io) builds on machine learning to provide preemptive web app & API threat protection against OWASP-Top-10 and zero-day attacks. It can be deployed as an add-on to Linux, Docker or K8s deployments, on NGINX, Kong, APISIX, or Envoy.
|
||||||
|
|
||||||
The open-appsec engine learns how users normally interact with your web application. It then uses this information to automatically detect requests that fall outside of normal operations, and conducts further analysis to decide whether the request is malicious or not.
|
The open-appsec engine learns how users normally interact with your web application. It then uses this information to automatically detect requests that fall outside of normal operations, and conducts further analysis to decide whether the request is malicious or not.
|
||||||
|
|
||||||
@@ -39,13 +39,13 @@ open-appsec can be managed using multiple methods:
|
|||||||
* [Using SaaS Web Management](https://docs.openappsec.io/getting-started/using-the-web-ui-saas)
|
* [Using SaaS Web Management](https://docs.openappsec.io/getting-started/using-the-web-ui-saas)
|
||||||
|
|
||||||
open-appsec Web UI:
|
open-appsec Web UI:
|
||||||
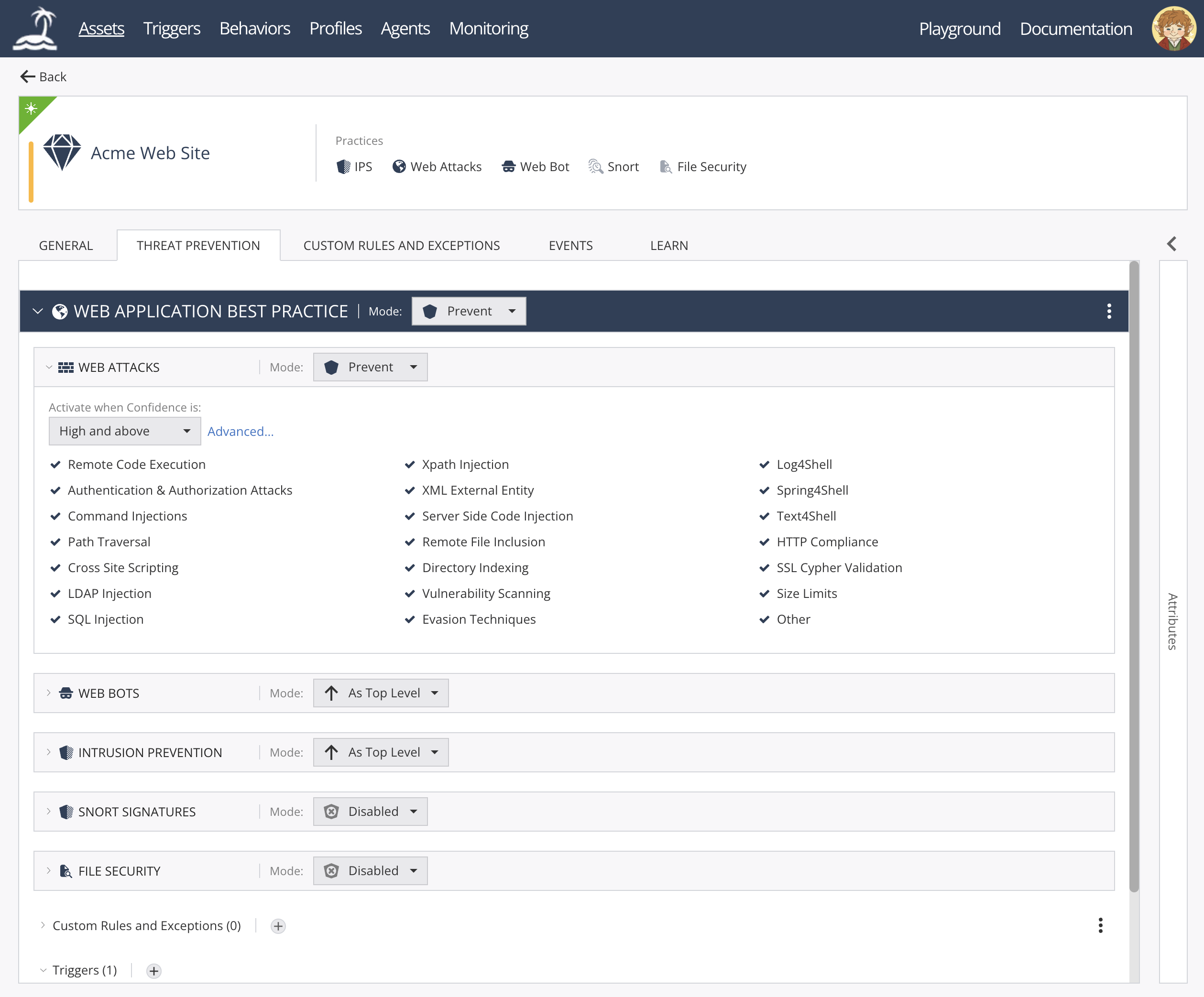
|
<img width="1854" height="775" alt="image" src="https://github.com/user-attachments/assets/4c6f7b0a-14f3-4f02-9ab0-ddadc9979b8d" />
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
## Deployment Playgrounds (Virtual labs)
|
## Deployment Playgrounds (Virtual labs)
|
||||||
You can experiment with open-appsec using [Playgrounds](https://www.openappsec.io/playground)
|
You can experiment with open-appsec using [Playgrounds](https://www.openappsec.io/playground)
|
||||||
|
<img width="781" height="878" alt="image" src="https://github.com/user-attachments/assets/0ddee216-5cdf-4288-8c41-cc28cfbf3297" />
|
||||||
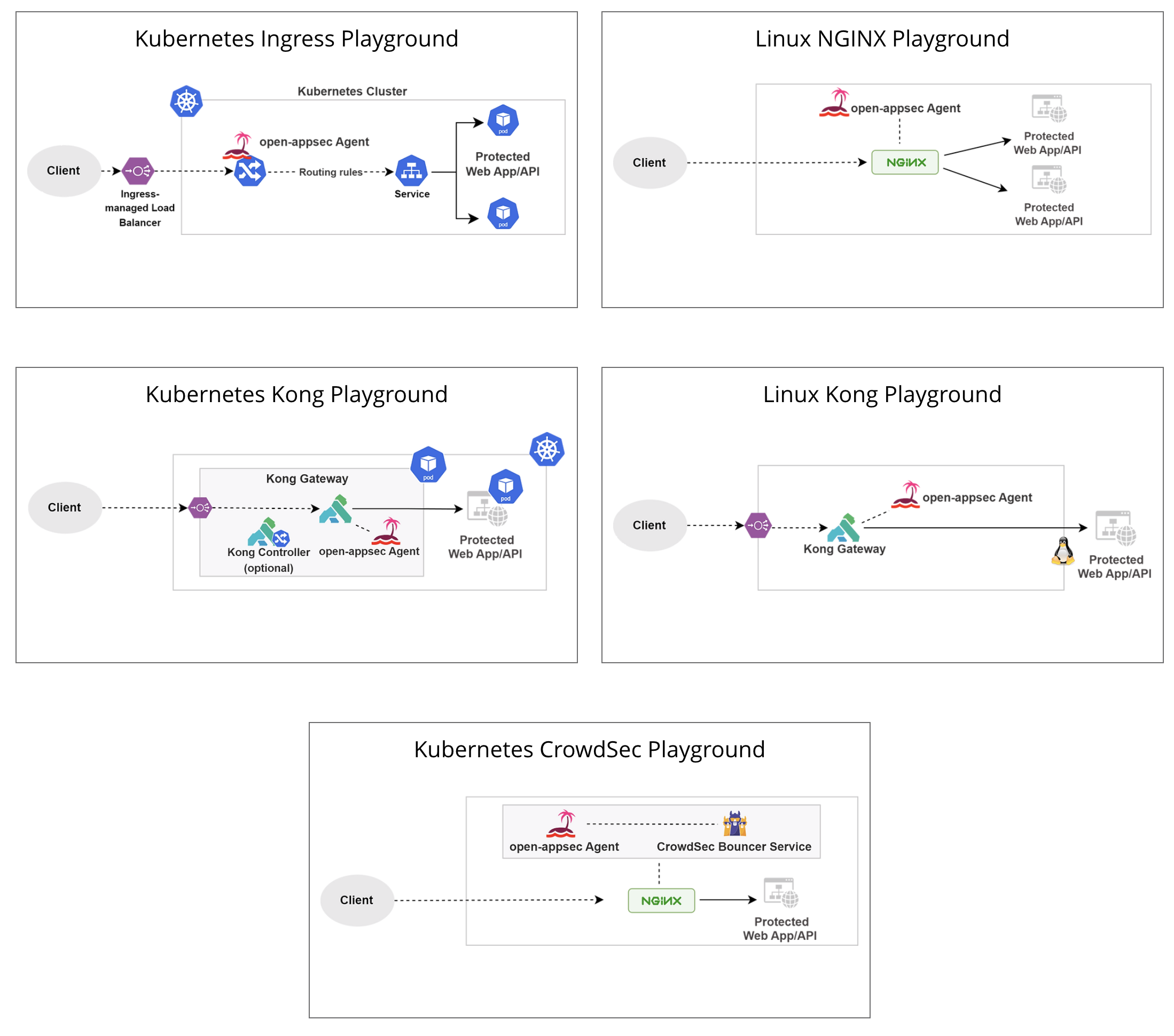
|
|
||||||
|
|
||||||
# Resources
|
# Resources
|
||||||
* [Project Website](https://openappsec.io)
|
* [Project Website](https://openappsec.io)
|
||||||
@@ -54,21 +54,15 @@ You can experiment with open-appsec using [Playgrounds](https://www.openappsec.i
|
|||||||
|
|
||||||
# Installation
|
# Installation
|
||||||
|
|
||||||
For Kubernetes (NGINX Ingress) using the installer:
|
For Kubernetes (NGINX /Kong / APISIX / Istio) using Helm: follow [documentation](https://docs.openappsec.io/getting-started/start-with-kubernetes)
|
||||||
|
|
||||||
```bash
|
For Linux (NGINX / Kong / APISIX) using the installer (list of supported/pre-compiled NGINX attachments is available [here](https://downloads.openappsec.io/packages/supported-nginx.txt)):
|
||||||
$ wget https://downloads.openappsec.io/open-appsec-k8s-install && chmod +x open-appsec-k8s-install
|
|
||||||
$ ./open-appsec-k8s-install
|
|
||||||
```
|
|
||||||
|
|
||||||
For Kubernetes (NGINX or Kong) using Helm: follow [documentation](https://docs.openappsec.io/getting-started/start-with-kubernetes/install-using-helm-ingress-nginx-and-kong) – use this method if you’ve built your own containers.
|
|
||||||
|
|
||||||
For Linux (NGINX or Kong) using the installer (list of supported/pre-compiled NGINX attachments is available [here](https://downloads.openappsec.io/packages/supported-nginx.txt)):
|
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
$ wget https://downloads.openappsec.io/open-appsec-install && chmod +x open-appsec-install
|
$ wget https://downloads.openappsec.io/open-appsec-install && chmod +x open-appsec-install
|
||||||
$ ./open-appsec-install --auto
|
$ ./open-appsec-install --auto
|
||||||
```
|
```
|
||||||
|
For kong Lua Based plug in follow [documentation](https://docs.openappsec.io/getting-started/start-with-linux)
|
||||||
|
|
||||||
For Linux, if you’ve built your own package use the following commands:
|
For Linux, if you’ve built your own package use the following commands:
|
||||||
|
|
||||||
|
|||||||
@@ -13,8 +13,10 @@ RUN apk add --no-cache libunwind
|
|||||||
RUN apk add --no-cache gdb
|
RUN apk add --no-cache gdb
|
||||||
RUN apk add --no-cache libxml2
|
RUN apk add --no-cache libxml2
|
||||||
RUN apk add --no-cache pcre2
|
RUN apk add --no-cache pcre2
|
||||||
|
RUN apk add --no-cache ca-certificates
|
||||||
RUN apk add --update coreutils
|
RUN apk add --update coreutils
|
||||||
|
|
||||||
|
|
||||||
COPY self_managed_openappsec_manifest.json /tmp/self_managed_openappsec_manifest.json
|
COPY self_managed_openappsec_manifest.json /tmp/self_managed_openappsec_manifest.json
|
||||||
|
|
||||||
COPY install*.sh /nano-service-installers/
|
COPY install*.sh /nano-service-installers/
|
||||||
|
|||||||
@@ -15,6 +15,21 @@ var_mode=
|
|||||||
var_token=
|
var_token=
|
||||||
var_ignore=
|
var_ignore=
|
||||||
init=
|
init=
|
||||||
|
active_watchdog_pid=
|
||||||
|
|
||||||
|
cleanup() {
|
||||||
|
local signal="$1"
|
||||||
|
echo "[$(date '+%Y-%m-%d %H:%M:%S')] Signal ${signal} was received, exiting gracefully..." >&2
|
||||||
|
if [ -n "${active_watchdog_pid}" ] && ps -p ${active_watchdog_pid} > /dev/null 2>&1; then
|
||||||
|
kill -TERM ${active_watchdog_pid} 2>/dev/null || true
|
||||||
|
wait ${active_watchdog_pid} 2>/dev/null || true
|
||||||
|
fi
|
||||||
|
echo "Cleanup completed. Exiting now." >&2
|
||||||
|
exit 0
|
||||||
|
}
|
||||||
|
|
||||||
|
trap 'cleanup SIGTERM' SIGTERM
|
||||||
|
trap 'cleanup SIGINT' SIGINT
|
||||||
|
|
||||||
if [ ! -f /nano-service-installers/$ORCHESTRATION_INSTALLATION_SCRIPT ]; then
|
if [ ! -f /nano-service-installers/$ORCHESTRATION_INSTALLATION_SCRIPT ]; then
|
||||||
echo "Error: agent installation package doesn't exist."
|
echo "Error: agent installation package doesn't exist."
|
||||||
|
|||||||
@@ -515,60 +515,63 @@ K8sPolicyUtils::createAppsecPolicyK8sFromV1beta2Crds(
|
|||||||
}
|
}
|
||||||
// LCOV_EXCL_STOP
|
// LCOV_EXCL_STOP
|
||||||
|
|
||||||
std::tuple<Maybe<AppsecLinuxPolicy>, Maybe<V1beta2AppsecLinuxPolicy>>
|
tuple<Maybe<AppsecLinuxPolicy>, Maybe<V1beta2AppsecLinuxPolicy>>
|
||||||
K8sPolicyUtils::createAppsecPolicyK8s(const string &policy_name, const string &ingress_mode) const
|
K8sPolicyUtils::createAppsecPolicyK8s(const string &policy_name, const string &ingress_mode) const
|
||||||
{
|
{
|
||||||
auto maybe_appsec_policy_spec = getObjectFromCluster<AppsecSpecParser<AppsecPolicySpec>>(
|
string ns_suffix = getAppSecScopeType() == "namespaced" ? "ns" : "";
|
||||||
"/apis/openappsec.io/v1beta1/policies/" + policy_name
|
string ns = getAppSecScopeType() == "namespaced" ? "namespaces/" : "";
|
||||||
|
auto maybe_v1beta2_appsec_policy_spec = getObjectFromCluster<AppsecSpecParser<NewAppsecPolicySpec>>(
|
||||||
|
"/apis/openappsec.io/v1beta2/" + ns + agent_ns + "policies" + ns_suffix + "/" + policy_name
|
||||||
);
|
);
|
||||||
|
|
||||||
if (!maybe_appsec_policy_spec.ok() ||
|
if (!maybe_v1beta2_appsec_policy_spec.ok() ||
|
||||||
maybe_appsec_policy_spec.unpack().getApiVersion().find("v1beta1") == std::string::npos
|
maybe_v1beta2_appsec_policy_spec.unpack().getApiVersion().find("v1beta2") == std::string::npos
|
||||||
) {
|
) {
|
||||||
try {
|
try {
|
||||||
std::string v1beta1_error =
|
string policy_error = maybe_v1beta2_appsec_policy_spec.getErr();
|
||||||
maybe_appsec_policy_spec.ok() ? "There is no v1beta1 policy" : maybe_appsec_policy_spec.getErr();
|
string v1beta2_error =
|
||||||
|
maybe_v1beta2_appsec_policy_spec.ok() ? "There is no v1beta2 policy" : policy_error;
|
||||||
dbgWarning(D_LOCAL_POLICY
|
dbgWarning(D_LOCAL_POLICY
|
||||||
) << "Failed to retrieve Appsec policy with crds version: v1beta1, Trying version: v1beta2";
|
) << "Failed to retrieve Appsec policy with crds version: v1beta1, Trying version: v1beta2";
|
||||||
string ns_suffix = getAppSecScopeType() == "namespaced" ? "ns" : "";
|
auto maybe_appsec_policy_spec = getObjectFromCluster<AppsecSpecParser<AppsecPolicySpec>>(
|
||||||
string ns = getAppSecScopeType() == "namespaced" ? "namespaces/" : "";
|
"/apis/openappsec.io/v1beta1/policies/" + policy_name
|
||||||
auto maybe_v1beta2_appsec_policy_spec = getObjectFromCluster<AppsecSpecParser<NewAppsecPolicySpec>>(
|
|
||||||
"/apis/openappsec.io/v1beta2/" + ns + agent_ns + "policies" + ns_suffix + "/" + policy_name
|
|
||||||
);
|
);
|
||||||
|
|
||||||
if (!maybe_v1beta2_appsec_policy_spec.ok()) {
|
if (!maybe_appsec_policy_spec.ok()) {
|
||||||
dbgWarning(D_LOCAL_POLICY)
|
dbgWarning(D_LOCAL_POLICY)
|
||||||
<< "Failed to retrieve AppSec policy. Error: " << maybe_v1beta2_appsec_policy_spec.getErr();
|
<< "Failed to retrieve AppSec policy. Error: " << maybe_appsec_policy_spec.getErr();
|
||||||
return std::make_tuple(
|
return std::make_tuple(
|
||||||
genError("Failed to retrieve AppSec v1beta1 policy. Error: " + v1beta1_error),
|
genError("Failed to retrieve AppSec v1beta1 policy. Error: " + maybe_appsec_policy_spec.getErr()),
|
||||||
genError(
|
genError(
|
||||||
"Failed to retrieve AppSec v1beta2 policy. Error: " + maybe_v1beta2_appsec_policy_spec.getErr()
|
"Failed to retrieve AppSec v1beta2 policy. Error: " + v1beta2_error
|
||||||
)
|
)
|
||||||
);
|
);
|
||||||
}
|
}
|
||||||
return std::make_tuple(
|
return std::make_tuple(
|
||||||
genError("There is no v1beta1 policy"),
|
createAppsecPolicyK8sFromV1beta1Crds(maybe_appsec_policy_spec.unpack(), ingress_mode),
|
||||||
createAppsecPolicyK8sFromV1beta2Crds(maybe_v1beta2_appsec_policy_spec.unpack(), ingress_mode)
|
genError("There is no v1beta2 policy")
|
||||||
);
|
);
|
||||||
|
|
||||||
} catch (const PolicyGenException &e) {
|
} catch (const PolicyGenException &e) {
|
||||||
dbgDebug(D_LOCAL_POLICY) << "Failed in policy generation. Error: " << e.what();
|
dbgDebug(D_LOCAL_POLICY) << "Failed in policy generation. Error: " << e.what();
|
||||||
return std::make_tuple(
|
return make_tuple(
|
||||||
genError("There is no v1beta1 policy"),
|
genError("There is no v1beta1 policy"),
|
||||||
genError("Failed to retrieve AppSec v1beta2 policy. Error: " + string(e.what()))
|
genError("Failed to retrieve AppSec v1beta2 policy. Error: " + string(e.what()))
|
||||||
);
|
);
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
return std::make_tuple(
|
return make_tuple(
|
||||||
createAppsecPolicyK8sFromV1beta1Crds(maybe_appsec_policy_spec.unpack(), ingress_mode),
|
genError("There is no v1beta1 policy"),
|
||||||
genError("There is no v1beta2 policy"));
|
createAppsecPolicyK8sFromV1beta2Crds(maybe_v1beta2_appsec_policy_spec.unpack(), ingress_mode)
|
||||||
|
);
|
||||||
}
|
}
|
||||||
|
|
||||||
template<class T, class K>
|
template<class T, class K>
|
||||||
void
|
void
|
||||||
K8sPolicyUtils::createPolicyFromIngress(
|
K8sPolicyUtils::createPolicyFromIngress(
|
||||||
T &appsec_policy,
|
T &appsec_policy,
|
||||||
map<std::string, T> &policies,
|
map<string, T> &policies,
|
||||||
map<AnnotationKeys, string> &annotations_values,
|
map<AnnotationKeys, string> &annotations_values,
|
||||||
const SingleIngressData &item) const
|
const SingleIngressData &item) const
|
||||||
{
|
{
|
||||||
@@ -608,7 +611,7 @@ template<class T, class K>
|
|||||||
void
|
void
|
||||||
K8sPolicyUtils::createPolicyFromActivation(
|
K8sPolicyUtils::createPolicyFromActivation(
|
||||||
T &appsec_policy,
|
T &appsec_policy,
|
||||||
map<std::string, T> &policies,
|
map<string, T> &policies,
|
||||||
const EnabledPolicy &policy) const
|
const EnabledPolicy &policy) const
|
||||||
{
|
{
|
||||||
if (policies.find(policy.getName()) == policies.end()) {
|
if (policies.find(policy.getName()) == policies.end()) {
|
||||||
|
|||||||
@@ -1522,6 +1522,12 @@ private:
|
|||||||
|
|
||||||
agent_data_report << make_pair("registeredServer", i_agent_details->getRegisteredServer());
|
agent_data_report << make_pair("registeredServer", i_agent_details->getRegisteredServer());
|
||||||
|
|
||||||
|
const char *prometheus_env = getenv("PROMETHEUS");
|
||||||
|
if (prometheus_env != nullptr) {
|
||||||
|
auto enable_prometheus = string(prometheus_env) == "true";
|
||||||
|
agent_data_report << AgentReportFieldWithLabel("enablePrometheus", enable_prometheus ? "true" : "false");
|
||||||
|
}
|
||||||
|
|
||||||
#if defined(gaia) || defined(smb)
|
#if defined(gaia) || defined(smb)
|
||||||
if (i_details_resolver->compareCheckpointVersion(8100, greater_equal<int>())) {
|
if (i_details_resolver->compareCheckpointVersion(8100, greater_equal<int>())) {
|
||||||
agent_data_report << AgentReportFieldWithLabel("isCheckpointVersionGER81", "true");
|
agent_data_report << AgentReportFieldWithLabel("isCheckpointVersionGER81", "true");
|
||||||
@@ -2272,4 +2278,4 @@ OrchestrationComp::preload()
|
|||||||
registerExpectedSetting<uint>("successUpgradeInterval");
|
registerExpectedSetting<uint>("successUpgradeInterval");
|
||||||
registerExpectedConfigFile("orchestration", Config::ConfigFileType::Policy);
|
registerExpectedConfigFile("orchestration", Config::ConfigFileType::Policy);
|
||||||
registerExpectedConfigFile("registration-data", Config::ConfigFileType::Policy);
|
registerExpectedConfigFile("registration-data", Config::ConfigFileType::Policy);
|
||||||
}
|
}
|
||||||
@@ -227,6 +227,11 @@ FogAuthenticator::registerAgent(
|
|||||||
|
|
||||||
request << make_pair("userEdition", getUserEdition());
|
request << make_pair("userEdition", getUserEdition());
|
||||||
|
|
||||||
|
const char *prometheus_env = getenv("PROMETHEUS");
|
||||||
|
if (prometheus_env != nullptr) {
|
||||||
|
request << make_pair("enablePrometheus", string(prometheus_env) == "true" ? "true" : "false");
|
||||||
|
}
|
||||||
|
|
||||||
if (getDeplymentType() == "Docker" || getDeplymentType() == "K8S") {
|
if (getDeplymentType() == "Docker" || getDeplymentType() == "K8S") {
|
||||||
const char *image_version_otp = getenv("IMAGE_VERSION");
|
const char *image_version_otp = getenv("IMAGE_VERSION");
|
||||||
if (image_version_otp) {
|
if (image_version_otp) {
|
||||||
|
|||||||
@@ -12,6 +12,7 @@ add_library(waap_clib
|
|||||||
ParserJson.cc
|
ParserJson.cc
|
||||||
ParserMultipartForm.cc
|
ParserMultipartForm.cc
|
||||||
ParserRaw.cc
|
ParserRaw.cc
|
||||||
|
ParserGzip.cc
|
||||||
ParserUrlEncode.cc
|
ParserUrlEncode.cc
|
||||||
ParserXML.cc
|
ParserXML.cc
|
||||||
ParserDelimiter.cc
|
ParserDelimiter.cc
|
||||||
|
|||||||
@@ -22,6 +22,7 @@
|
|||||||
#include "ParserXML.h"
|
#include "ParserXML.h"
|
||||||
#include "ParserHTML.h"
|
#include "ParserHTML.h"
|
||||||
#include "ParserBinary.h"
|
#include "ParserBinary.h"
|
||||||
|
#include "ParserGzip.h"
|
||||||
#include "ParserMultipartForm.h"
|
#include "ParserMultipartForm.h"
|
||||||
#include "ParserPercentEncode.h"
|
#include "ParserPercentEncode.h"
|
||||||
#include "ParserPairs.h"
|
#include "ParserPairs.h"
|
||||||
@@ -1261,6 +1262,10 @@ DeepParser::createInternalParser(
|
|||||||
dbgTrace(D_WAAP_DEEP_PARSER) << "Starting to parse an HTML file";
|
dbgTrace(D_WAAP_DEEP_PARSER) << "Starting to parse an HTML file";
|
||||||
m_parsersDeque.push_back(std::make_shared<BufferedParser<ParserHTML>>(*this, parser_depth + 1));
|
m_parsersDeque.push_back(std::make_shared<BufferedParser<ParserHTML>>(*this, parser_depth + 1));
|
||||||
offset = 0;
|
offset = 0;
|
||||||
|
} else if (isBodyPayload && Waap::Util::isGzipped(cur_val)){
|
||||||
|
dbgTrace(D_WAAP_DEEP_PARSER) << "Starting to parse a gzip file";
|
||||||
|
m_parsersDeque.push_back(std::make_shared<BufferedParser<ParserGzip>>(*this, parser_depth + 1));
|
||||||
|
offset = 0;
|
||||||
} else if (cur_val.size() > 0 && signatures->php_serialize_identifier.hasMatch(cur_val)) {
|
} else if (cur_val.size() > 0 && signatures->php_serialize_identifier.hasMatch(cur_val)) {
|
||||||
// PHP value detected
|
// PHP value detected
|
||||||
dbgTrace(D_WAAP_DEEP_PARSER) << "Starting to parse phpSerializedData";
|
dbgTrace(D_WAAP_DEEP_PARSER) << "Starting to parse phpSerializedData";
|
||||||
|
|||||||
115
components/security_apps/waap/waap_clib/ParserGzip.cc
Executable file
115
components/security_apps/waap/waap_clib/ParserGzip.cc
Executable file
@@ -0,0 +1,115 @@
|
|||||||
|
// Copyright (C) 2022 Check Point Software Technologies Ltd. All rights reserved.
|
||||||
|
|
||||||
|
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
// You may obtain a copy of the License at
|
||||||
|
//
|
||||||
|
// http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
//
|
||||||
|
// Unless required by applicable law or agreed to in writing, software
|
||||||
|
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
// See the License for the specific language governing permissions and
|
||||||
|
// limitations under the License.
|
||||||
|
|
||||||
|
#include "ParserGzip.h"
|
||||||
|
#include "debug.h"
|
||||||
|
|
||||||
|
USE_DEBUG_FLAG(D_WAAP_PARSER_GZIP);
|
||||||
|
|
||||||
|
const std::string ParserGzip::m_parserName = "ParserGzip";
|
||||||
|
|
||||||
|
ParserGzip::ParserGzip(IParserStreamReceiver &receiver, size_t parser_depth)
|
||||||
|
:m_receiver(receiver), m_key("gzip"), m_state(s_start), m_stream(nullptr) {
|
||||||
|
}
|
||||||
|
|
||||||
|
ParserGzip::~ParserGzip() {
|
||||||
|
if (m_stream != nullptr) {
|
||||||
|
finiCompressionStream(m_stream);
|
||||||
|
m_stream = nullptr;
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
size_t ParserGzip::push(const char *buf, size_t len) {
|
||||||
|
dbgTrace(D_WAAP_PARSER_GZIP) << "len=" << (unsigned long int)len << ")";
|
||||||
|
|
||||||
|
if (len == 0) {
|
||||||
|
dbgTrace(D_WAAP_PARSER_GZIP) << "end of data signal! m_state=" << m_state;
|
||||||
|
|
||||||
|
// flush
|
||||||
|
if (m_state != s_start) { // only emit if at least something was pushed
|
||||||
|
if (m_receiver.onKvDone() != 0) {
|
||||||
|
m_state = s_error;
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
return 0;
|
||||||
|
}
|
||||||
|
DecompressionResult res;
|
||||||
|
switch (m_state) {
|
||||||
|
case s_start:
|
||||||
|
dbgTrace(D_WAAP_PARSER_GZIP) << "s_start";
|
||||||
|
if (m_receiver.onKey(m_key.data(), m_key.size()) != 0) {
|
||||||
|
m_state = s_error;
|
||||||
|
return 0;
|
||||||
|
}
|
||||||
|
m_stream = initCompressionStream();
|
||||||
|
m_state = s_forward;
|
||||||
|
// fallthrough //
|
||||||
|
CP_FALL_THROUGH;
|
||||||
|
case s_forward:
|
||||||
|
dbgTrace(D_WAAP_PARSER_GZIP) << "s_forward";
|
||||||
|
res = decompressData(
|
||||||
|
m_stream,
|
||||||
|
len,
|
||||||
|
reinterpret_cast<const unsigned char *>(buf));
|
||||||
|
dbgTrace(D_WAAP_PARSER_GZIP) << "res: " << res.ok
|
||||||
|
<< ", size: " << res.num_output_bytes
|
||||||
|
<< ", is last: " << res.is_last_chunk;
|
||||||
|
|
||||||
|
if (!res.ok) {
|
||||||
|
m_state = s_error;
|
||||||
|
break;
|
||||||
|
}
|
||||||
|
|
||||||
|
if (res.num_output_bytes != 0 &&
|
||||||
|
m_receiver.onValue(reinterpret_cast<const char *>(res.output), res.num_output_bytes) != 0) {
|
||||||
|
m_state = s_error;
|
||||||
|
break;
|
||||||
|
}
|
||||||
|
|
||||||
|
if (res.is_last_chunk) {
|
||||||
|
m_state = s_done;
|
||||||
|
break;
|
||||||
|
}
|
||||||
|
break;
|
||||||
|
case s_done:
|
||||||
|
if (len > 0) {
|
||||||
|
dbgTrace(D_WAAP_PARSER_GZIP) << " unexpected data after completion, len=" << len;
|
||||||
|
m_state = s_error;
|
||||||
|
return 0; // Return 0 to indicate error
|
||||||
|
}
|
||||||
|
break;
|
||||||
|
case s_error:
|
||||||
|
dbgTrace(D_WAAP_PARSER_GZIP) << "s_error";
|
||||||
|
return 0;
|
||||||
|
}
|
||||||
|
|
||||||
|
return len;
|
||||||
|
}
|
||||||
|
|
||||||
|
void ParserGzip::finish() {
|
||||||
|
push(NULL, 0);
|
||||||
|
if (m_state != s_done) {
|
||||||
|
m_state = s_error;
|
||||||
|
return;
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
const std::string &
|
||||||
|
ParserGzip::name() const {
|
||||||
|
return m_parserName;
|
||||||
|
}
|
||||||
|
|
||||||
|
bool ParserGzip::error() const {
|
||||||
|
return m_state == s_error;
|
||||||
|
}
|
||||||
46
components/security_apps/waap/waap_clib/ParserGzip.h
Executable file
46
components/security_apps/waap/waap_clib/ParserGzip.h
Executable file
@@ -0,0 +1,46 @@
|
|||||||
|
// Copyright (C) 2022 Check Point Software Technologies Ltd. All rights reserved.
|
||||||
|
|
||||||
|
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
// You may obtain a copy of the License at
|
||||||
|
//
|
||||||
|
// http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
//
|
||||||
|
// Unless required by applicable law or agreed to in writing, software
|
||||||
|
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
// See the License for the specific language governing permissions and
|
||||||
|
// limitations under the License.
|
||||||
|
|
||||||
|
#ifndef __PARSER_GZIP_H_
|
||||||
|
#define __PARSER_GZIP_H_
|
||||||
|
|
||||||
|
#include "ParserBase.h"
|
||||||
|
#include <string.h>
|
||||||
|
#include "compression_utils.h"
|
||||||
|
|
||||||
|
class ParserGzip : public ParserBase {
|
||||||
|
public:
|
||||||
|
ParserGzip(IParserStreamReceiver &receiver, size_t parser_depth);
|
||||||
|
virtual ~ParserGzip();
|
||||||
|
size_t push(const char *data, size_t data_len);
|
||||||
|
void finish();
|
||||||
|
virtual const std::string &name() const;
|
||||||
|
bool error() const;
|
||||||
|
virtual size_t depth() { return 1; }
|
||||||
|
private:
|
||||||
|
enum state {
|
||||||
|
s_start,
|
||||||
|
s_forward,
|
||||||
|
s_done,
|
||||||
|
s_error
|
||||||
|
};
|
||||||
|
|
||||||
|
IParserStreamReceiver &m_receiver;
|
||||||
|
std::string m_key;
|
||||||
|
state m_state;
|
||||||
|
CompressionStream * m_stream;
|
||||||
|
|
||||||
|
static const std::string m_parserName;
|
||||||
|
};
|
||||||
|
|
||||||
|
#endif // __PARSER_GZIP_H_
|
||||||
@@ -44,14 +44,6 @@ static const string defaultSharedStorageHost = "appsec-shared-storage-svc";
|
|||||||
#define SHARED_STORAGE_HOST_ENV_NAME "SHARED_STORAGE_HOST"
|
#define SHARED_STORAGE_HOST_ENV_NAME "SHARED_STORAGE_HOST"
|
||||||
#define LEARNING_HOST_ENV_NAME "LEARNING_HOST"
|
#define LEARNING_HOST_ENV_NAME "LEARNING_HOST"
|
||||||
|
|
||||||
static bool
|
|
||||||
isGZipped(const string &stream)
|
|
||||||
{
|
|
||||||
if (stream.size() < 2) return false;
|
|
||||||
auto unsinged_stream = reinterpret_cast<const u_char *>(stream.data());
|
|
||||||
return unsinged_stream[0] == 0x1f && unsinged_stream[1] == 0x8b;
|
|
||||||
}
|
|
||||||
|
|
||||||
void yieldIfPossible(const string& func, int line)
|
void yieldIfPossible(const string& func, int line)
|
||||||
{
|
{
|
||||||
// Check if we are in the main loop
|
// Check if we are in the main loop
|
||||||
@@ -73,7 +65,7 @@ bool RestGetFile::loadJson(const string& json)
|
|||||||
string json_str;
|
string json_str;
|
||||||
|
|
||||||
json_str = json;
|
json_str = json;
|
||||||
if (!isGZipped(json_str))
|
if (!Waap::Util::isGzipped(json_str))
|
||||||
{
|
{
|
||||||
return ClientRest::loadJson(json_str);
|
return ClientRest::loadJson(json_str);
|
||||||
}
|
}
|
||||||
@@ -343,7 +335,7 @@ void SerializeToFileBase::saveData()
|
|||||||
}
|
}
|
||||||
|
|
||||||
string decompress(string fileContent) {
|
string decompress(string fileContent) {
|
||||||
if (!isGZipped(fileContent)) {
|
if (!Waap::Util::isGzipped(fileContent)) {
|
||||||
dbgTrace(D_WAAP_SERIALIZE) << "file note zipped";
|
dbgTrace(D_WAAP_SERIALIZE) << "file note zipped";
|
||||||
return fileContent;
|
return fileContent;
|
||||||
}
|
}
|
||||||
|
|||||||
@@ -103,7 +103,7 @@ ValueStatsAnalyzer::ValueStatsAnalyzer(const std::string &cur_val)
|
|||||||
bool lastNul = false; // whether last processed character was ASCII NUL
|
bool lastNul = false; // whether last processed character was ASCII NUL
|
||||||
size_t curValLength = cur_val.length();
|
size_t curValLength = cur_val.length();
|
||||||
|
|
||||||
if (curValLength == 0) {
|
if (curValLength == 0 || Waap::Util::isGzipped(cur_val)) {
|
||||||
canSplitSemicolon = false;
|
canSplitSemicolon = false;
|
||||||
canSplitPipe = false;
|
canSplitPipe = false;
|
||||||
return;
|
return;
|
||||||
|
|||||||
@@ -1912,6 +1912,17 @@ base64Decode(const string &input)
|
|||||||
return out;
|
return out;
|
||||||
}
|
}
|
||||||
|
|
||||||
|
bool
|
||||||
|
isGzipped(const string &stream)
|
||||||
|
{
|
||||||
|
if (stream.size() < 2) return false;
|
||||||
|
auto unsinged_stream = reinterpret_cast<const u_char *>(stream.data());
|
||||||
|
dbgTrace(D_WAAP) << "isGzipped: first two bytes: "
|
||||||
|
<< std::hex << static_cast<int>(unsinged_stream[0]) << " "
|
||||||
|
<< std::hex << static_cast<int>(unsinged_stream[1]);
|
||||||
|
return unsinged_stream[0] == 0x1f && unsinged_stream[1] == 0x8b;
|
||||||
|
}
|
||||||
|
|
||||||
bool
|
bool
|
||||||
containsInvalidUtf8(const string &payload)
|
containsInvalidUtf8(const string &payload)
|
||||||
{
|
{
|
||||||
|
|||||||
@@ -1135,6 +1135,7 @@ namespace Util {
|
|||||||
std::string obfuscateXor(const std::string& toEncrypt);
|
std::string obfuscateXor(const std::string& toEncrypt);
|
||||||
std::string obfuscateXorBase64(const std::string& toEncrypt);
|
std::string obfuscateXorBase64(const std::string& toEncrypt);
|
||||||
|
|
||||||
|
bool isGzipped(const std::string &stream);
|
||||||
bool containsInvalidUtf8(const std::string &payload);
|
bool containsInvalidUtf8(const std::string &payload);
|
||||||
|
|
||||||
bool containsPercentEncoding(const std::string &payload);
|
bool containsPercentEncoding(const std::string &payload);
|
||||||
|
|||||||
@@ -40,7 +40,7 @@ spec:
|
|||||||
stdout:
|
stdout:
|
||||||
format: json
|
format: json
|
||||||
cef-service: []
|
cef-service: []
|
||||||
--
|
---
|
||||||
apiVersion: openappsec.io/v1beta1
|
apiVersion: openappsec.io/v1beta1
|
||||||
kind: Practice
|
kind: Practice
|
||||||
metadata:
|
metadata:
|
||||||
@@ -56,7 +56,7 @@ spec:
|
|||||||
web-attacks:
|
web-attacks:
|
||||||
minimum-confidence: high
|
minimum-confidence: high
|
||||||
override-mode: detect-learn
|
override-mode: detect-learn
|
||||||
--
|
---
|
||||||
apiVersion: openappsec.io/v1beta1
|
apiVersion: openappsec.io/v1beta1
|
||||||
kind: CustomResponse
|
kind: CustomResponse
|
||||||
metadata:
|
metadata:
|
||||||
|
|||||||
@@ -40,7 +40,7 @@ spec:
|
|||||||
stdout:
|
stdout:
|
||||||
format: json
|
format: json
|
||||||
cef-service: []
|
cef-service: []
|
||||||
--
|
---
|
||||||
apiVersion: openappsec.io/v1beta1
|
apiVersion: openappsec.io/v1beta1
|
||||||
kind: Practice
|
kind: Practice
|
||||||
metadata:
|
metadata:
|
||||||
@@ -56,7 +56,7 @@ spec:
|
|||||||
web-attacks:
|
web-attacks:
|
||||||
minimum-confidence: high
|
minimum-confidence: high
|
||||||
override-mode: prevent-learn
|
override-mode: prevent-learn
|
||||||
--
|
---
|
||||||
apiVersion: openappsec.io/v1beta1
|
apiVersion: openappsec.io/v1beta1
|
||||||
kind: CustomResponse
|
kind: CustomResponse
|
||||||
metadata:
|
metadata:
|
||||||
|
|||||||
@@ -106,6 +106,7 @@ DEFINE_FLAG(D_COMPONENT, D_ALL)
|
|||||||
DEFINE_FLAG(D_WAAP_PARSER_GQL, D_WAAP_PARSER)
|
DEFINE_FLAG(D_WAAP_PARSER_GQL, D_WAAP_PARSER)
|
||||||
DEFINE_FLAG(D_WAAP_PARSER_MULTIPART_FORM, D_WAAP_PARSER)
|
DEFINE_FLAG(D_WAAP_PARSER_MULTIPART_FORM, D_WAAP_PARSER)
|
||||||
DEFINE_FLAG(D_WAAP_PARSER_RAW, D_WAAP_PARSER)
|
DEFINE_FLAG(D_WAAP_PARSER_RAW, D_WAAP_PARSER)
|
||||||
|
DEFINE_FLAG(D_WAAP_PARSER_GZIP, D_WAAP_PARSER)
|
||||||
DEFINE_FLAG(D_WAAP_PARSER_URLENCODE, D_WAAP_PARSER)
|
DEFINE_FLAG(D_WAAP_PARSER_URLENCODE, D_WAAP_PARSER)
|
||||||
DEFINE_FLAG(D_WAAP_PARSER_PHPSERIALIZE, D_WAAP_PARSER)
|
DEFINE_FLAG(D_WAAP_PARSER_PHPSERIALIZE, D_WAAP_PARSER)
|
||||||
DEFINE_FLAG(D_WAAP_PARSER_PERCENT, D_WAAP_PARSER)
|
DEFINE_FLAG(D_WAAP_PARSER_PERCENT, D_WAAP_PARSER)
|
||||||
|
|||||||
@@ -262,6 +262,29 @@ public:
|
|||||||
}
|
}
|
||||||
|
|
||||||
private:
|
private:
|
||||||
|
string
|
||||||
|
getCertificateDirectory()
|
||||||
|
{
|
||||||
|
auto details_ssl_dir = Singleton::Consume<I_AgentDetails>::by<Messaging>()->getOpenSSLDir();
|
||||||
|
|
||||||
|
if (details_ssl_dir.ok()) {
|
||||||
|
return *details_ssl_dir;
|
||||||
|
}
|
||||||
|
|
||||||
|
// Use detail_resolver to determine platform-specific certificate directory
|
||||||
|
#if defined(alpine)
|
||||||
|
string platform = "alpine";
|
||||||
|
#else
|
||||||
|
string platform = "linux";
|
||||||
|
#endif
|
||||||
|
|
||||||
|
if (platform == "alpine") {
|
||||||
|
return "/etc/ssl/certs/";
|
||||||
|
}
|
||||||
|
|
||||||
|
return "/usr/lib/ssl/certs/";
|
||||||
|
}
|
||||||
|
|
||||||
Maybe<void>
|
Maybe<void>
|
||||||
setSSLContext()
|
setSSLContext()
|
||||||
{
|
{
|
||||||
@@ -296,10 +319,11 @@ private:
|
|||||||
}
|
}
|
||||||
|
|
||||||
dbgTrace(D_CONNECTION) << "Setting CA authentication";
|
dbgTrace(D_CONNECTION) << "Setting CA authentication";
|
||||||
auto details_ssl_dir = Singleton::Consume<I_AgentDetails>::by<Messaging>()->getOpenSSLDir();
|
|
||||||
auto openssl_dir = details_ssl_dir.ok() ? *details_ssl_dir : "/usr/lib/ssl/certs/";
|
auto default_ssl_dir = getCertificateDirectory();
|
||||||
auto configured_ssl_dir = getConfigurationWithDefault(openssl_dir, "message", "Trusted CA directory");
|
auto configured_ssl_dir =
|
||||||
const char *ca_dir = configured_ssl_dir.empty() ? nullptr : configured_ssl_dir.c_str();
|
getProfileAgentSettingWithDefault<string>(default_ssl_dir, "agent.config.message.capath");
|
||||||
|
const char *ca_dir = configured_ssl_dir.empty() ? "/usr/lib/ssl/certs/" : configured_ssl_dir.c_str();
|
||||||
|
|
||||||
if (SSL_CTX_load_verify_locations(ssl_ctx.get(), ca_path.c_str(), ca_dir) != 1) {
|
if (SSL_CTX_load_verify_locations(ssl_ctx.get(), ca_path.c_str(), ca_dir) != 1) {
|
||||||
return genError("Failed to load certificate locations");
|
return genError("Failed to load certificate locations");
|
||||||
|
|||||||
@@ -23,6 +23,7 @@ APPSEC_DB_PASSWORD=pass
|
|||||||
APPSEC_DB_USER=postgres
|
APPSEC_DB_USER=postgres
|
||||||
APPSEC_DB_HOST=appsec-db
|
APPSEC_DB_HOST=appsec-db
|
||||||
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
||||||
|
APPSEC_POSTGRES_VERSION=18
|
||||||
|
|
||||||
## Make sure to have a valid apisix configuration for APISIX in standalone mode in the following file:
|
## Make sure to have a valid apisix configuration for APISIX in standalone mode in the following file:
|
||||||
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
||||||
|
|||||||
@@ -103,14 +103,14 @@ services:
|
|||||||
appsec-db:
|
appsec-db:
|
||||||
profiles:
|
profiles:
|
||||||
- standalone
|
- standalone
|
||||||
image: postgres
|
image: postgres:${APPSEC_POSTGRES_VERSION}
|
||||||
container_name: appsec-db
|
container_name: appsec-db
|
||||||
restart: always
|
restart: always
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
||||||
- POSTGRES_USER=${APPSEC_DB_USER}
|
- POSTGRES_USER=${APPSEC_DB_USER}
|
||||||
volumes:
|
volumes:
|
||||||
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql/data
|
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql
|
||||||
|
|
||||||
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
||||||
juiceshop-backend:
|
juiceshop-backend:
|
||||||
|
|||||||
@@ -23,6 +23,7 @@ APPSEC_DB_PASSWORD=pass
|
|||||||
APPSEC_DB_USER=postgres
|
APPSEC_DB_USER=postgres
|
||||||
APPSEC_DB_HOST=appsec-db
|
APPSEC_DB_HOST=appsec-db
|
||||||
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
||||||
|
APPSEC_POSTGRES_VERSION=18
|
||||||
|
|
||||||
## Make sure to have a valid envoy.yaml Envoy configuration file present in the path below.
|
## Make sure to have a valid envoy.yaml Envoy configuration file present in the path below.
|
||||||
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
||||||
|
|||||||
@@ -109,14 +109,14 @@ services:
|
|||||||
appsec-db:
|
appsec-db:
|
||||||
profiles:
|
profiles:
|
||||||
- standalone
|
- standalone
|
||||||
image: postgres
|
image: postgres:${APPSEC_POSTGRES_VERSION}
|
||||||
container_name: appsec-db
|
container_name: appsec-db
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
||||||
- POSTGRES_USER=${APPSEC_DB_USER}
|
- POSTGRES_USER=${APPSEC_DB_USER}
|
||||||
volumes:
|
volumes:
|
||||||
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql/data
|
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql
|
||||||
|
|
||||||
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
||||||
juiceshop-backend:
|
juiceshop-backend:
|
||||||
|
|||||||
@@ -23,6 +23,7 @@ APPSEC_DB_PASSWORD=pass
|
|||||||
APPSEC_DB_USER=postgres
|
APPSEC_DB_USER=postgres
|
||||||
APPSEC_DB_HOST=appsec-db
|
APPSEC_DB_HOST=appsec-db
|
||||||
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
||||||
|
APPSEC_POSTGRES_VERSION=18
|
||||||
|
|
||||||
## Make sure to have a valid Kong declarative configuration file kong.yaml in the folder specified for KONG_CONFIG.
|
## Make sure to have a valid Kong declarative configuration file kong.yaml in the folder specified for KONG_CONFIG.
|
||||||
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
||||||
|
|||||||
@@ -28,7 +28,7 @@ services:
|
|||||||
- user_email=${APPSEC_USER_EMAIL}
|
- user_email=${APPSEC_USER_EMAIL}
|
||||||
- AGENT_TOKEN=${APPSEC_AGENT_TOKEN}
|
- AGENT_TOKEN=${APPSEC_AGENT_TOKEN}
|
||||||
- autoPolicyLoad=${APPSEC_AUTO_POLICY_LOAD}
|
- autoPolicyLoad=${APPSEC_AUTO_POLICY_LOAD}
|
||||||
- registered_server=Kong
|
- registered_server=KongLua
|
||||||
ipc: shareable
|
ipc: shareable
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
volumes:
|
volumes:
|
||||||
@@ -106,14 +106,14 @@ services:
|
|||||||
appsec-db:
|
appsec-db:
|
||||||
profiles:
|
profiles:
|
||||||
- standalone
|
- standalone
|
||||||
image: postgres
|
image: postgres:${APPSEC_POSTGRES_VERSION}
|
||||||
container_name: appsec-db
|
container_name: appsec-db
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
||||||
- POSTGRES_USER=${APPSEC_DB_USER}
|
- POSTGRES_USER=${APPSEC_DB_USER}
|
||||||
volumes:
|
volumes:
|
||||||
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql/data
|
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql
|
||||||
|
|
||||||
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
||||||
juiceshop-backend:
|
juiceshop-backend:
|
||||||
|
|||||||
@@ -23,6 +23,7 @@ APPSEC_DB_PASSWORD=pass
|
|||||||
APPSEC_DB_USER=postgres
|
APPSEC_DB_USER=postgres
|
||||||
APPSEC_DB_HOST=appsec-db
|
APPSEC_DB_HOST=appsec-db
|
||||||
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
||||||
|
APPSEC_POSTGRES_VERSION=18
|
||||||
|
|
||||||
## Make sure to have a valid Kong declarative configuration file kong.yaml in the folder specified for KONG_CONFIG.
|
## Make sure to have a valid Kong declarative configuration file kong.yaml in the folder specified for KONG_CONFIG.
|
||||||
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
||||||
|
|||||||
@@ -106,14 +106,14 @@ services:
|
|||||||
appsec-db:
|
appsec-db:
|
||||||
profiles:
|
profiles:
|
||||||
- standalone
|
- standalone
|
||||||
image: postgres
|
image: postgres:${APPSEC_POSTGRES_VERSION}
|
||||||
container_name: appsec-db
|
container_name: appsec-db
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
||||||
- POSTGRES_USER=${APPSEC_DB_USER}
|
- POSTGRES_USER=${APPSEC_DB_USER}
|
||||||
volumes:
|
volumes:
|
||||||
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql/data
|
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql
|
||||||
|
|
||||||
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
||||||
juiceshop-backend:
|
juiceshop-backend:
|
||||||
|
|||||||
@@ -23,6 +23,7 @@ APPSEC_DB_PASSWORD=pass
|
|||||||
APPSEC_DB_USER=postgres
|
APPSEC_DB_USER=postgres
|
||||||
APPSEC_DB_HOST=appsec-db
|
APPSEC_DB_HOST=appsec-db
|
||||||
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
||||||
|
APPSEC_POSTGRES_VERSION=18
|
||||||
|
|
||||||
# Volume mounts for NGINX Proxy Manager have been moved here as well allowing configuration via .env file
|
# Volume mounts for NGINX Proxy Manager have been moved here as well allowing configuration via .env file
|
||||||
NPM_DATA=./data
|
NPM_DATA=./data
|
||||||
|
|||||||
@@ -103,14 +103,14 @@ services:
|
|||||||
appsec-db:
|
appsec-db:
|
||||||
profiles:
|
profiles:
|
||||||
- standalone
|
- standalone
|
||||||
image: postgres
|
image: postgres:${APPSEC_POSTGRES_VERSION}
|
||||||
container_name: appsec-db
|
container_name: appsec-db
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
||||||
- POSTGRES_USER=${APPSEC_DB_USER}
|
- POSTGRES_USER=${APPSEC_DB_USER}
|
||||||
volumes:
|
volumes:
|
||||||
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql/data
|
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql
|
||||||
|
|
||||||
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
||||||
juiceshop-backend:
|
juiceshop-backend:
|
||||||
|
|||||||
@@ -21,6 +21,7 @@ APPSEC_DB_PASSWORD=pass
|
|||||||
APPSEC_DB_USER=postgres
|
APPSEC_DB_USER=postgres
|
||||||
APPSEC_DB_HOST=appsec-db
|
APPSEC_DB_HOST=appsec-db
|
||||||
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
||||||
|
APPSEC_POSTGRES_VERSION=18
|
||||||
|
|
||||||
# Volume mounts for NGINX Proxy Manager have been moved here as well allowing configuration via .env file
|
# Volume mounts for NGINX Proxy Manager have been moved here as well allowing configuration via .env file
|
||||||
NPM_DATA=./data
|
NPM_DATA=./data
|
||||||
|
|||||||
@@ -106,14 +106,14 @@ services:
|
|||||||
appsec-db:
|
appsec-db:
|
||||||
profiles:
|
profiles:
|
||||||
- standalone
|
- standalone
|
||||||
image: postgres
|
image: postgres:${APPSEC_POSTGRES_VERSION}
|
||||||
container_name: appsec-db
|
container_name: appsec-db
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
||||||
- POSTGRES_USER=${APPSEC_DB_USER}
|
- POSTGRES_USER=${APPSEC_DB_USER}
|
||||||
volumes:
|
volumes:
|
||||||
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql/data
|
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql
|
||||||
|
|
||||||
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
||||||
juiceshop-backend:
|
juiceshop-backend:
|
||||||
|
|||||||
@@ -23,6 +23,7 @@ APPSEC_DB_PASSWORD=pass
|
|||||||
APPSEC_DB_USER=postgres
|
APPSEC_DB_USER=postgres
|
||||||
APPSEC_DB_HOST=appsec-db
|
APPSEC_DB_HOST=appsec-db
|
||||||
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
||||||
|
APPSEC_POSTGRES_VERSION=18
|
||||||
|
|
||||||
## Make sure to have a valid NGINX configuration file default.conf in the folder specified for NGINX_CONFIG.
|
## Make sure to have a valid NGINX configuration file default.conf in the folder specified for NGINX_CONFIG.
|
||||||
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
||||||
|
|||||||
@@ -96,14 +96,14 @@ services:
|
|||||||
appsec-db:
|
appsec-db:
|
||||||
profiles:
|
profiles:
|
||||||
- standalone
|
- standalone
|
||||||
image: postgres
|
image: postgres:${APPSEC_POSTGRES_VERSION}
|
||||||
container_name: appsec-db
|
container_name: appsec-db
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
||||||
- POSTGRES_USER=${APPSEC_DB_USER}
|
- POSTGRES_USER=${APPSEC_DB_USER}
|
||||||
volumes:
|
volumes:
|
||||||
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql/data
|
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql
|
||||||
|
|
||||||
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
||||||
juiceshop-backend:
|
juiceshop-backend:
|
||||||
|
|||||||
@@ -23,6 +23,7 @@ APPSEC_DB_PASSWORD=pass
|
|||||||
APPSEC_DB_USER=postgres
|
APPSEC_DB_USER=postgres
|
||||||
APPSEC_DB_HOST=appsec-db
|
APPSEC_DB_HOST=appsec-db
|
||||||
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
||||||
|
APPSEC_POSTGRES_VERSION=18
|
||||||
|
|
||||||
## Make sure to have a valid NGINX configuration file default.conf in the folder specified for NGINX_CONFIG.
|
## Make sure to have a valid NGINX configuration file default.conf in the folder specified for NGINX_CONFIG.
|
||||||
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
## For deployment of a simple lab testing environment, you can deploy the example configuration provided
|
||||||
|
|||||||
@@ -108,14 +108,14 @@ services:
|
|||||||
appsec-db:
|
appsec-db:
|
||||||
profiles:
|
profiles:
|
||||||
- standalone
|
- standalone
|
||||||
image: postgres
|
image: postgres:${APPSEC_POSTGRES_VERSION}
|
||||||
container_name: appsec-db
|
container_name: appsec-db
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
||||||
- POSTGRES_USER=${APPSEC_DB_USER}
|
- POSTGRES_USER=${APPSEC_DB_USER}
|
||||||
volumes:
|
volumes:
|
||||||
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql/data
|
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql
|
||||||
|
|
||||||
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
||||||
juiceshop-backend:
|
juiceshop-backend:
|
||||||
|
|||||||
@@ -23,6 +23,7 @@ APPSEC_DB_PASSWORD=pass
|
|||||||
APPSEC_DB_USER=postgres
|
APPSEC_DB_USER=postgres
|
||||||
APPSEC_DB_HOST=appsec-db
|
APPSEC_DB_HOST=appsec-db
|
||||||
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
APPSEC_POSTGRES_STORAGE=./appsec-postgres-data
|
||||||
|
APPSEC_POSTGRES_VERSION=18
|
||||||
|
|
||||||
## Most relevant SWAG parameters have been moved here as well allowing configuration via .env file
|
## Most relevant SWAG parameters have been moved here as well allowing configuration via .env file
|
||||||
SWAG_CONFIG=./swag-config
|
SWAG_CONFIG=./swag-config
|
||||||
|
|||||||
@@ -117,14 +117,14 @@ services:
|
|||||||
appsec-db:
|
appsec-db:
|
||||||
profiles:
|
profiles:
|
||||||
- standalone
|
- standalone
|
||||||
image: postgres
|
image: postgres:${APPSEC_POSTGRES_VERSION}
|
||||||
container_name: appsec-db
|
container_name: appsec-db
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
- POSTGRES_PASSWORD=${APPSEC_DB_PASSWORD}
|
||||||
- POSTGRES_USER=${APPSEC_DB_USER}
|
- POSTGRES_USER=${APPSEC_DB_USER}
|
||||||
volumes:
|
volumes:
|
||||||
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql/data
|
- ${APPSEC_POSTGRES_STORAGE}:/var/lib/postgresql
|
||||||
|
|
||||||
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
||||||
juiceshop-backend:
|
juiceshop-backend:
|
||||||
|
|||||||
@@ -15,6 +15,7 @@ USER_EMAIL=user@email.com
|
|||||||
DB_PASSWORD=pass
|
DB_PASSWORD=pass
|
||||||
DB_USER=postgres
|
DB_USER=postgres
|
||||||
DB_HOST=appsec-db
|
DB_HOST=appsec-db
|
||||||
|
POSTGRES_VERSION=18
|
||||||
POSTGRES_STORAGE=./postgres-data
|
POSTGRES_STORAGE=./postgres-data
|
||||||
NGINX_CONF_DIR=./nginx-proxy-config
|
NGINX_CONF_DIR=./nginx-proxy-config
|
||||||
|
|
||||||
|
|||||||
@@ -81,14 +81,14 @@ services:
|
|||||||
appsec-db:
|
appsec-db:
|
||||||
profiles:
|
profiles:
|
||||||
- standalone
|
- standalone
|
||||||
image: postgres
|
image: postgres:${POSTGRES_VERSION}
|
||||||
container_name: appsec-db
|
container_name: appsec-db
|
||||||
restart: always
|
restart: always
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_PASSWORD=${DB_PASSWORD}
|
- POSTGRES_PASSWORD=${DB_PASSWORD}
|
||||||
- POSTGRES_USER=${DB_USER}
|
- POSTGRES_USER=${DB_USER}
|
||||||
volumes:
|
volumes:
|
||||||
- ${POSTGRES_STORAGE}:/var/lib/postgresql/data
|
- ${POSTGRES_STORAGE}:/var/lib/postgresql
|
||||||
|
|
||||||
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
## example juice-shop backend container (vulnerable webserver, USE ONLY FOR TESTING AND IN LAB ENV)
|
||||||
##
|
##
|
||||||
|
|||||||
@@ -209,6 +209,9 @@ save_local_policy_config()
|
|||||||
if [ -n "${CP_ENV_FILESYSTEM}" ] ; then
|
if [ -n "${CP_ENV_FILESYSTEM}" ] ; then
|
||||||
export FILESYSTEM_PATH=$CP_ENV_FILESYSTEM
|
export FILESYSTEM_PATH=$CP_ENV_FILESYSTEM
|
||||||
fi
|
fi
|
||||||
|
if [ -n "${PROMETHEUS}" ] ; then
|
||||||
|
export PROMETHEUS=$PROMETHEUS
|
||||||
|
fi
|
||||||
if [ -n "${CP_ENV_LOG_FILE}" ] ; then
|
if [ -n "${CP_ENV_LOG_FILE}" ] ; then
|
||||||
LOG_FILE_PATH=$CP_ENV_LOG_FILE
|
LOG_FILE_PATH=$CP_ENV_LOG_FILE
|
||||||
fi
|
fi
|
||||||
@@ -433,7 +436,7 @@ if command -v which &>/dev/null; then
|
|||||||
var_which_cmd_exists=1
|
var_which_cmd_exists=1
|
||||||
fi
|
fi
|
||||||
|
|
||||||
if [ $var_arch != "gaia" ] && [ $var_arch != "gaia_arm" ] && [ $var_which_cmd_exists -eq 1 ]; then
|
if [ $var_arch != "gaia" ] && [ $var_arch != "gaia_arm" ] && [ $var_which_cmd_exists -eq 1 ]; then
|
||||||
if [ -n "$(which systemctl)" ]; then
|
if [ -n "$(which systemctl)" ]; then
|
||||||
var_startup_service="systemd"
|
var_startup_service="systemd"
|
||||||
else
|
else
|
||||||
@@ -974,7 +977,7 @@ install_orchestration()
|
|||||||
fi
|
fi
|
||||||
${INSTALL_COMMAND} lib/*.so* ${USR_LIB_PATH}/
|
${INSTALL_COMMAND} lib/*.so* ${USR_LIB_PATH}/
|
||||||
${INSTALL_COMMAND} lib/boost/*.so* ${USR_LIB_PATH}/
|
${INSTALL_COMMAND} lib/boost/*.so* ${USR_LIB_PATH}/
|
||||||
cp_print "Done successfully doing only unpacking lib64 to Path: ${USR_LIB_PATH}" ${FORCE_STDOUT}
|
cp_print "Done successfully doing only unpacking lib64 to Path: ${USR_LIB_PATH}" ${FORCE_STDOUT}
|
||||||
exit 0
|
exit 0
|
||||||
fi
|
fi
|
||||||
|
|
||||||
@@ -1149,6 +1152,9 @@ install_orchestration()
|
|||||||
if [ -n "${FILESYSTEM_PATH}" ]; then
|
if [ -n "${FILESYSTEM_PATH}" ]; then
|
||||||
echo "CP_ENV_FILESYSTEM=${FILESYSTEM_PATH}" >> ${FILESYSTEM_PATH}/${ENV_DETAILS_FILE}
|
echo "CP_ENV_FILESYSTEM=${FILESYSTEM_PATH}" >> ${FILESYSTEM_PATH}/${ENV_DETAILS_FILE}
|
||||||
fi
|
fi
|
||||||
|
if [ -n "${PROMETHEUS}" ]; then
|
||||||
|
echo "PROMETHEUS=${PROMETHEUS}" >> ${FILESYSTEM_PATH}/${ENV_DETAILS_FILE}
|
||||||
|
fi
|
||||||
if [ -n "${VS_ID}" ]; then
|
if [ -n "${VS_ID}" ]; then
|
||||||
echo "CP_VS_ID=${VS_ID}" >> ${FILESYSTEM_PATH}/${ENV_DETAILS_FILE}
|
echo "CP_VS_ID=${VS_ID}" >> ${FILESYSTEM_PATH}/${ENV_DETAILS_FILE}
|
||||||
fi
|
fi
|
||||||
|
|||||||
@@ -115,6 +115,11 @@ load_paths()
|
|||||||
if [ -n "${CP_ENV_LOG_FILE}" ]; then
|
if [ -n "${CP_ENV_LOG_FILE}" ]; then
|
||||||
LOG_FILE_PATH=$CP_ENV_LOG_FILE
|
LOG_FILE_PATH=$CP_ENV_LOG_FILE
|
||||||
fi
|
fi
|
||||||
|
|
||||||
|
if [ -n "${PROMETHEUS}" ]; then
|
||||||
|
export PROMETHEUS=$PROMETHEUS
|
||||||
|
fi
|
||||||
|
|
||||||
if [ -n "${CP_VS_ID}" ]; then
|
if [ -n "${CP_VS_ID}" ]; then
|
||||||
VS_ID=${CP_VS_ID}
|
VS_ID=${CP_VS_ID}
|
||||||
VS_EVAL_PREFIX="ip netns exec CTX0000${VS_ID} env"
|
VS_EVAL_PREFIX="ip netns exec CTX0000${VS_ID} env"
|
||||||
|
|||||||
Reference in New Issue
Block a user